In this guide, you will learn how to install Ansible Automation Platform on RHEL 9 using RPM packages. Red Hat Ansible Automation Platform (AAP) is an enterprise-grade automation solution that provides a comprehensive framework for implementing automation across your entire IT infrastructure.
Table of Contents
Install Ansible Automation Platform on RHEL 9 using RPM
What is Ansible Automation Platform (AAP)?
Ansible Automation Platform (AAP) is Red Hat’s enterprise-ready automation solution designed to help organizations scale, secure, and govern their automation workflows across hybrid and multi-cloud environments. Built around the power of Ansible, AAP provides a comprehensive suite that includes Automation Controller (the direct successor to Ansible Tower), Automation Hub for curated and certified content, customizable Execution Environments for consistent automation runtimes, and Event-Driven Ansible for triggering automation based on real-time events.
How does AAP compare with AWX and Ansible Tower?
While AWX serves as the upstream, open-source community project where new features are developed and tested, AAP takes those innovations, hardens them for enterprise use, adds official support, security patches, lifecycle management, and integrates them into a cohesive, production-grade platform. Similarly, Ansible Tower was the original commercial UI and control plane for Ansible, which has now fully evolved into Automation Controller within AAP.
In short: AWX is the community version, Tower was the first-gen product, and AAP is the modern, full-stack enterprise automation platform that supersedes both, offering scalability, governance, and support for mission-critical operations.
Key Components of Ansible Automation Platform (AAP) 2.5
Red Hat Ansible Automation Platform (AAP) 2.5 is designed as a modular, enterprise-ready suite for scaling automation across IT environments. Each component has a clear role, and together they provide a consistent, secure, and event-driven automation experience.
Here’s a breakdown of the key components:
- The Platform Gateway: It provides a single entry point into AAP. It handles authentication and authorization, and serves the web user interface (UI) for the entire platform. Instead of logging in separately to different services, users and systems connect to the gateway on one address. This centralization simplifies access, improves security, and makes scaling deployments easier.
- The Automation Controller (formerly Ansible Tower): It is the central management layer for automation. It provides a web-based UI and REST API, along with job scheduling, execution history, and detailed role-based access controls. Administrators use it to manage inventories, credentials, workflows, and securely delegate automation across teams.
- The Event-Driven Ansible (EDA) Controller: It enables automation that reacts to real-time events instead of scheduled tasks. By connecting to monitoring tools, security platforms, or IT service systems, the EDA controller listens for events and uses rulebooks to trigger automated responses. This ensures faster, more consistent, and resilient operations.
- The Automation Hub: It serves as the official repository for trusted Ansible Content Collections. It provides certified and supported content from Red Hat and its partners, ensuring that automation building blocks are secure, reliable, and enterprise-grade.
- The Private Automation Hub: It allows organizations to host their own internal repository of automation content. Teams can mirror Red Hat’s certified collections, upload their own, and integrate with external sources such as Galaxy. This is especially valuable in disconnected or restricted environments that require strict control over automation content.
- The High Availability (HA) Automation Hub: It is designed for large-scale or mission-critical environments. Multiple hub nodes run in parallel behind a load balancer, eliminating single points of failure and ensuring the hub service remains resilient and scalable.
- Ansible Galaxy: It is the public community hub where automation content is shared freely. While not supported by Red Hat, it is often the starting point for building automation projects. Many of the certified collections later available in Automation Hub originate in Galaxy.
- The Automation Content Navigator (ansible-navigator): It is the command-line and text-based interface for developers and operators. It simplifies building, testing, and debugging automation content locally, and ensures a smooth workflow from development to production.
- Automation Execution Environments: These are container images that package everything needed to run automation, including Ansible Core, Python, required collections, and dependencies. They replace the older system-Python model and guarantee consistent automation execution across all environments.
- The Automation Mesh: It is the networking layer that connects AAP components such as controllers, gateways, and execution nodes. The mesh securely distributes workloads across datacenters, regions, or edge sites, while handling latency and rerouting around failures. It enables flexible scaling of execution capacity independently from the control plane.
- PostgreSQL Database: It is the persistent storage backend for the platform. PostgreSQL stores automation data including job templates, inventories, credentials, and execution history. In production deployments, PostgreSQL is usually external for resilience, performance, and easier scaling.
Understanding AAP Installation Methods and Deployment Topologies
Red Hat Ansible Automation Platform (AAP) 2.5 supports multiple installation methods, each suited to different infrastructure and operational models. Each method supports one or more tested deployment topologies, designed for scalability, performance, and supportability.
Red Hat Ansible Automation Platform (AAP) 2.5 can be installed using three different methods, depending on your infrastructure and operational preferences:
- RPM Installation
- Container-Based Installation
- Operator-Based Installation (on OpenShift)
Each installation method supports one or more tested topologies such as Growth and Enterprise designed to ensure proper performance, scalability, and supportability.
1. RPM Installation Method
Installs AAP directly on RHEL using RPM packages on virtual machines or bare metal, giving you full control over the operating system and infrastructure lifecycle.
Supported Topologies:
- Growth Topology
- Components are deployed across six virtual machines without redundancy.
- Suitable for development, testing, and small-scale production.
- Minimum per-VM requirements: 16 GB RAM, 4 vCPUs, 60–100 GB storage, 3000 IOPS
- Component layout:
- VM1: Platform Gateway + Redis
- VM2: Automation Controller
- VM3: Private Automation Hub
- VM4: Event-Driven Ansible Controller
- VM5: Execution Node
- VM6: PostgreSQL Database
- Enterprise Topology
- Redundant, scalable deployment across 11 or more VMs.
- Includes 2x Gateways, 2x Controllers, 2x Hubs, 2x EDA Controllers, external PostgreSQL DB, and HAProxy load balancer.
- Designed for high-availability and large-scale production environments.
2. Container Installation Method
Runs AAP components in containers using Podman on RHEL (on VMs or bare metal), offering portability and simplified deployment while still requiring you to manage the underlying infrastructure.
Supported Topologies:
- Growth Topology
- All components run as containers on a single RHEL VM.
- Useful for labs, proof-of-concept, and testing only.
- Not supported for production due to lack of redundancy.
- Enterprise Topology
- Components are containerized and distributed across multiple VMs.
- Offers redundancy and better resource scaling.
- Suitable for production environments.
3. Operator Installation Method
Deploys AAP on Red Hat OpenShift using certified Operators, providing automated lifecycle management in a Kubernetes-native environment.
Supported Topologies:
- Growth Topology
- Runs on Single Node OpenShift (SNO).
- Suitable for evaluation or small-scale use cases.
- Not recommended for production workloads.
- Enterprise Topology
- Deployed on a multi-node OpenShift cluster.
- Supports external services and full redundancy.
- Designed for production-grade, scalable automation.
System Requirements
This guide follows Red Hat’s supported Growth Topology for deploying Ansible Automation Platform, where all core components are distributed across six dedicated virtual machines. Each VM hosts a specific AAP component: Platform Gateway, Automation Controller, Execution Node, Private Automation Hub, Event-Driven Ansible Controller, and the Database; to ensure better performance, scalability, and alignment with Red Hat’s reference architecture. This topology is recommended for production environments, as it supports high availability (with further scaling) and allows independent scaling, management, and troubleshooting of each component.
Key Prerequisites
- Root access via
sudo umaskset to0022- NTP client configured
Minimum Hardware Requirements
Minimum hardware requirements for each of the 6 virtual machines:
| Component | RAM | vCPU | Disk IOPS | Storage |
|---|---|---|---|---|
| Platform Gateway | 16 GB | 4 | 3000 | 60 GB minimum |
| Control Nodes | 16 GB | 4 | 3000 | 80 GB minimum At least 20 GB must be under /var/lib/awx |
| Execution Nodes | 16 GB | 4 | 3000 | 60 GB minimum |
| Automation Hub | 16 GB | 4 | 3000 | 60 GB minimum At least 40 GB must be under /var/lib/pulp |
| Database | 16 GB | 4 | 3000 | 100 GB minimum Allocated to /var/lib/pgsql |
| Event-Driven Ansible Controller | 16 GB | 4 | 3000 | 60 GB minimum |
Minimum Software Requirements:
- OS: Red Hat Enterprise Linux 8.8+ or 9.2+
- Architecture: x86_64, AArch64, s390x, or ppc64le
- Database: PostgreSQL 15
- Ansible-core: Version 2.16+
Network Requirements
Key ports that must be open between components:
| Port Number | Protocol | Service | Source | Destination | Description |
|---|---|---|---|---|---|
| 80/443 | TCP | HTTP/HTTPS | Event-Driven Ansible | Automation Hub, Automation Controller | Handles HTTP/HTTPS communication from Event-Driven Ansible to Automation Hub and Controller. |
| 80/443 | TCP | HTTP/HTTPS | Automation Controller | Automation Hub | Handles HTTP/HTTPS communication from Automation Controller to Automation Hub. |
| 80/443 | TCP | HTTP/HTTPS | Platform Gateway | Automation Controller, Automation Hub, Event-Driven Ansible | Handles HTTP/HTTPS communication from Platform Gateway to other components. |
| 5432 | TCP | PostgreSQL | Event-Driven Ansible, Platform Gateway, Automation Hub, Automation Controller | Database | Database access for all components to the PostgreSQL database. |
| 6379 | TCP | Redis | Event-Driven Ansible, Platform Gateway | Redis Node | Redis communication for Event-Driven Ansible and Platform Gateway. |
| 8443 | TCP | HTTPS | Platform Gateway | Platform Gateway | Internal communication within Platform Gateway. |
| 27199 | TCP | Receptor | Automation Controller | Execution Node | Receptor communication for automation execution. |
The installer will open the respective ports on the respective nodes on firewalld. Be sure to verify after the installation is done:
sudo firewall-cmd --list-servicessudo firewall-cmd --list-portsFor more details, refer to RPM topologies page.
Repository Requirements
Enable only the following repositories before installing Ansible Automation Platform:
RHEL 9 repositories:
rhel-9-for-x86_64-baseos-rpms(BaseOS)rhel-9-for-x86_64-appstream-rpms(AppStream)
AAP RHEL 9 repository:
ansible-automation-platform-2.5-for-rhel-9-x86_64-rpms
You will to ensure that all the nodes for deploying AAP components have the repositories enabled.
Read more on system requirements page.
Required Licensing for Ansible Automation Platform
To install and operate Red Hat Ansible Automation Platform (AAP), a valid Red Hat subscription is required. AAP is built on open-source components like Ansible, which is licensed under the GNU General Public License v3, but the full AAP platform itself requires a commercial license for use, support, and updates.
Red Hat offers free trial licenses through the Red Hat Product Trial Center. Trials allow users to evaluate the platform but do not include official support. A valid license is still required, even for trial use.
Preparing RHEL 9 Nodes for AAP Installation
We have deployed 6 RHEL 9.6 vms on our KVM for deploying AAP.
Sample OS release version:
hostnamectl Static hostname: gateway.kifarunix.com
Icon name: computer-vm
Chassis: vm 🖴
Machine ID: 3c414936340f4f0da2709fbf25779847
Boot ID: 904c2bad7d8b4c2495d0789044204d45
Virtualization: kvm
Operating System: Red Hat Enterprise Linux 9.6 (Plow)
CPE OS Name: cpe:/o:redhat:enterprise_linux:9::baseos
Kernel: Linux 5.14.0-570.44.1.el9_6.x86_64
Architecture: x86-64
Hardware Vendor: QEMU
Hardware Model: Standard PC _Q35 + ICH9, 2009_
Firmware Version: 1.16.2-debian-1.16.2-1RAM allocated:
free -h total used free shared buff/cache available
Mem: 15Gi 517Mi 14Gi 4.0Mi 237Mi 14Gi
Swap: 2.0Gi 0B 2.0GiDisk allocated:
df -hT -P /Filesystem Type Size Used Avail Use% Mounted on
/dev/mapper/rhel-root xfs 47G 2.9G 45G 7% /Number of CPU cores:
nproc4Confirming drive IOPs:
sudo dnf install fio -yCheck the IOPS:
fio --name=randrw --ioengine=libaio --direct=1 --bs=4k --rw=randrw --rwmixread=70 \
--size=1G --numjobs=4 --runtime=60 --time_based --group_reportingSample truncated output;
fio-3.35
Starting 4 processes
randrw: Laying out IO file (1 file / 1024MiB)
randrw: Laying out IO file (1 file / 1024MiB)
randrw: Laying out IO file (1 file / 1024MiB)
randrw: Laying out IO file (1 file / 1024MiB)
Jobs: 4 (f=0): [f(4)][100.0%][r=229MiB/s,w=99.2MiB/s][r=58.7k,w=25.4k IOPS][eta 00m:00s]
randrw: (groupid=0, jobs=4): err= 0: pid=2767: Tue Sep 16 04:48:00 2025
read: IOPS=58.7k, BW=229MiB/s (240MB/s)(13.4GiB/60001msec)
...
write: IOPS=25.2k, BW=98.4MiB/s (103MB/s)(5905MiB/60001msec); 0 zone resets
...Result: read: IOPS=58.7k, write: IOPS=25.2k against required 3k!
Checking Umask Setting
Umask is set to 0022 as required. Confirm by running the command below.
umaskThe resulting umask value should be 0022. If it differs, you can update the default system-wide value in /etc/profile, /etc/bashrc, or /etc/login.defs, depending on the shell and login context.
NTP Time synchronization
Also, ensure all the nodes time is synchronized.
chronyc sourcesMS Name/IP address Stratum Poll Reach LastRx Last sample
===============================================================================
^* 192.168.122.110 3 6 17 14 +4889ns[ +11us] +/- 4361usEnsure external DNS Resolution works
dig goole.com +shortAttaching Red Hat Ansible Automation Platform Subscription
Before installing Red Hat Ansible Automation Platform (AAP), it is mandatory to have a valid subscription attached to all the relevant nodes. This ensures access to subscription-restricted content such as:
- Repositories required for AAP packages
- Certified Ansible collections
- Updates and support (if applicable)
In this guide, we’re using a trial license, but the steps apply to both trial and full subscriptions.
Depending on your environment, there are two primary methods to attach the AAP subscription to your nodes:
- Register Directly with Red Hat CDN
- Use Red Hat Satellite with Subscription Allocations
Register the Nodes Directly with Red Hat CDN
For standalone systems with direct Internet access, use this method if you’re not using Satellite, or want to attach the subscription directly via the Internet.
Register the system:
sudo subscription-manager register --username=<your_redhat_username>Find AAP subscription pool ID:
sudo subscription-manager list --available --allNote that:
- If your subscription is allocated to the Red Hat CDN, it will appear in this list.
- If it is allocated to Satellite or another manifest-based allocation (for disconnected installs or Cloud Access), it will not appear here. In that case, use a Satellite activation key or import the manifest instead.
Attach the subscription using the pool ID (Note: If Simple Content Access (SCA) is enabled for your Red Hat organization (which is the default in most cases), you do not need to attach subscriptions manually, you can skip this step):
subscription-manager attach --pool=<pool_id>Ensure that the AAP repos are enabled:
sudo subscription-manager repos --enable ansible-automation-platform-2.5-for-rhel-9-x86_64-rpmsAnd of course the RHEL 9 BaseOS and AppStream repos:
sudo subscription-manager repos --list-enabled Available Repositories in /etc/yum.repos.d/redhat.repo
+----------------------------------------------------------+
Repo ID: rhel-9-for-x86_64-baseos-rpms
Repo Name: Red Hat Enterprise Linux 9 for x86_64 - BaseOS (RPMs)
Repo URL: https://cdn.redhat.com/content/dist/rhel9/$releasever/x86_64/baseos/os
Enabled: 1
Repo ID: rhel-9-for-x86_64-appstream-rpms
Repo Name: Red Hat Enterprise Linux 9 for x86_64 - AppStream (RPMs)
Repo URL: https://cdn.redhat.com/content/dist/rhel9/$releasever/x86_64/appstream/os
Enabled: 1
Repo ID: ansible-automation-platform-2.5-for-rhel-9-x86_64-rpms
Repo Name: Red Hat Ansible Automation Platform 2.5 for RHEL 9 x86_64 (RPMs)
Repo URL: https://cdn.redhat.com/content/dist/layered/rhel9/x86_64/ansible-automation-platform/2.5/os
Enabled: 1Use Red Hat Satellite with Subscription Allocations
If you’re managing Red Hat Ansible Automation Platform (AAP) through Red Hat Satellite, you need to ensure that the AAP subscription is available via a Subscription Allocation in the Red Hat Customer Portal.
Therefore:
- Log into the Red Hat Customer Portal.
- Navigate to Subscription Allocations.
- Either:
- Create a new allocation for Satellite (if one doesn’t exist), or
- Open an existing allocation you already use with Satellite.
- Add the AAP subscription to that allocation.
- Depending on the scenario:
- If you created a new allocation:
- Download the manifest
.zipfile. - Import it into Satellite via Content > Subscriptions > Manage Manifest.
- Download the manifest
- If you’re just updating an existing allocation (e.g., by adding the AAP subscription to it):
- You do not need to re-download or re-import the manifest.
- Simply go to Subscriptions > Manage Manifest in Satellite and click Refresh.
- If you created a new allocation:
- Enable the relevant AAP repositories in Satellite:
- For example:
ansible-automation-platform-2.5-for-rhel-9-x86_64-rpms
- For example:
- You can do this via the Web UI:
- Content > Red Hat Repositories
- Filter by “Ansible Automation Platform”
- Check the appropriate repository and enable it.
- Sync the enabled repositories:
- Web UI: Content > Red Hat Repositories > Sync Status > expand the Red Hat Ansible Automation Platform repos check and > Synchronize Now.
- Add the synced repo to a Content View:
- Edit your existing content view (or create a new one).
- Include the AAP repository in the view.
- Publish and promote the content view to relevant lifecycle environments (e.g., Dev, Test, Prod).
- Ensure Activation Keys include the AAP subscription and repo access:
- Go to Content > Activation Keys
- Edit the Activation Key used for AAP systems.
- Under Subscriptions, attach the AAP subscription (or use Simple Content Access if enabled).
- Under Repositories, make sure the relevant AAP repositories are added.
This ensures the new AAP entitlements are visible in Satellite and can be used with Activation Keys or attached manually to registered systems.
Thus, register your AAP node to Satellite using the correct Activation key:
This ensures your system trusts the Satellite server’s SSL certificates. Replace <satellite_fqdn> with the actual FQDN of your Satellite server (e.g., satellite.example.com).
sudo rpm -Uvh http://<satellite_fqdn>/pub/katello-ca-consumer-latest.noarch.rpmUse the subscription-manager tool to register the system using your Organization and Activation Key.
sudo subscription-manager register \
--org="YourOrg" \
--activationkey="aap-activation-key"- Replace
YourOrgwith your Satellite organization name. - Replace
aap-activation-keywith the actual activation key name.
Check that the system is registered and has received its content access.
sudo subscription-manager repos --list-enabledYou should be able to see the required repositories in place; RHEL 9 BaseOS, AppStream and AAP.
For more guides on Red Hat Satellite, check our site.
Installing Ansible Automation Platform on RHEL 9
Step 1: Run RHEL OS Update
Before you can proceed, ensure the OS is already on the latest minor version. Hence:
sudo dnf update -yCheck if OS requires a reboot after update:
sudo dnf install yum-utils -yThe command below checks if a system reboot is required, and if so, automatically reboots the system.
needs-restarting -r || sudo rebootStep 2: Defining Resolvable FQDNs for AAP Deployment Nodes
You need to define unique fully qualified domain names (FQDNs) for the various AAP services. These FQDNs must resolve to each server’s IP address to ensure proper communication between components. If DNS is not available, this resolution can be achieved by configuring the /etc/hosts file accordingly.
We will define unique FQDNs for each AAP service component listed below (Replace the domain name, kifarunix.com, with your domain name). The services and their hostnames are:
- automationcontroller:
controller.kifarunix.com - execution_nodes:
exec.kifarunix.com - automationhub:
hub.kifarunix.com - automationedacontroller:
eda.kifarunix.com - database:
db.kifarunix.com - gateway:
gateway.kifarunix.com
If you want, you can also use your own naming convention. Just be sure to define the correct names on the inventory file.
Here is how we have defined the FQDNs in the /etc/hosts file:
cat /etc/hosts192.168.233.151 controller.kifarunix.com controller
192.168.233.152 gateway.kifarunix.com gateway
192.168.233.153 hub.kifarunix.com hub
192.168.233.154 exec.kifarunix.com exec
192.168.233.155 eda.kifarunix.com eda
192.168.233.156 db.kifarunix.com dbStep 3: Choose Your Installation Method
Red Hat AAP 2.5 offers three RPM-based installation methods for RHEL 9:
- RPM Direct installation: In this method, the AAP installer is delivered as a standard RPM package such as dnf/yum, which automatically pulls all dependencies from enabled repositories. Cleanest method for connected production environments.
- Bundle installer: The bundle installation is designed for disconnected or air-gapped environments. The archive (about 4–6 GB) contains all RPM packages and default execution environment images, so no internet is required once it has been downloaded. Use this method if you cannot access the internet or want to avoid pulling dependencies from external repositories.
- Online Installer: The online installation is smaller to download (~100–200 MB) but requires reliable connectivity throughout setup. Packages are fetched in real time from Red Hat repositories, making it the better option for connected environments without strict security restrictions.
We will focus on the RPM direct installation method in this guide.
Install AAP RPM Installer
Login to your chosen installer node. We are using controller node in this setup as our installation node.
So, depending on whether you’re subscribed to the Red Hat CDN directly or using a local Satellite server, ensure that the Ansible Automation Platform (AAP) repositories are enabled.
Then run the following command to install the AAP installer package along with its core dependencies on the installation node:
sudo dnf install ansible-automation-platform-installer -yUpdating Subscription Management repositories.
Red Hat Satellite Capsule 6.16 for RHEL 9 x86_64 (RPMs) 77 kB/s | 4.0 kB 00:00
Red Hat Enterprise Linux 9 for x86_64 - AppStream (RPMs) 141 kB/s | 4.5 kB 00:00
Red Hat Ansible Automation Platform 2.5 for RHEL 9 x86_64 (RPMs) 163 kB/s | 4.0 kB 00:00
Red Hat Enterprise Linux 9 for x86_64 - BaseOS (RPMs) 161 kB/s | 4.1 kB 00:00
Dependencies resolved.
==============================================================================================================================================================================================================
Package Architecture Version Repository Size
==============================================================================================================================================================================================================
Installing:
ansible-automation-platform-installer noarch 2.5-17.el9ap ansible-automation-platform-2.5-for-rhel-9-x86_64-rpms 3.6 M
Installing dependencies:
ansible-core noarch 1:2.16.14-2.el9ap ansible-automation-platform-2.5-for-rhel-9-x86_64-rpms 2.5 M
mpdecimal x86_64 2.5.1-3.el9 rhel-9-for-x86_64-appstream-rpms 88 k
python3.11 x86_64 3.11.11-2.el9_6.2 rhel-9-for-x86_64-appstream-rpms 25 k
python3.11-cffi x86_64 1.15.1-5.el9pc satellite-capsule-6.16-for-rhel-9-x86_64-rpms 299 k
python3.11-cryptography x86_64 42.0.8-1.el9pc satellite-capsule-6.16-for-rhel-9-x86_64-rpms 1.1 M
python3.11-jinja2 noarch 3.1.6-1.el9ap ansible-automation-platform-2.5-for-rhel-9-x86_64-rpms 327 k
python3.11-libs x86_64 3.11.11-2.el9_6.2 rhel-9-for-x86_64-appstream-rpms 10 M
python3.11-markupsafe x86_64 2.1.5-1.el9ap ansible-automation-platform-2.5-for-rhel-9-x86_64-rpms 31 k
python3.11-packaging noarch 23.2-1.el9ap ansible-automation-platform-2.5-for-rhel-9-x86_64-rpms 117 k
python3.11-pip-wheel noarch 22.3.1-5.el9 rhel-9-for-x86_64-appstream-rpms 1.4 M
python3.11-pycparser noarch 2.21-5.el9pc satellite-capsule-6.16-for-rhel-9-x86_64-rpms 249 k
python3.11-pyyaml x86_64 6.0-1.el9 rhel-9-for-x86_64-appstream-rpms 229 k
python3.11-resolvelib noarch 1.0.1-1.el9ap ansible-automation-platform-2.5-for-rhel-9-x86_64-rpms 39 k
python3.11-setuptools noarch 65.5.1-4.el9_6 rhel-9-for-x86_64-appstream-rpms 1.7 M
python3.11-setuptools-wheel noarch 65.5.1-4.el9_6 rhel-9-for-x86_64-appstream-rpms 712 k
sshpass x86_64 1.09-5.el9ap ansible-automation-platform-2.5-for-rhel-9-x86_64-rpms 27 k
Transaction Summary
==============================================================================================================================================================================================================
Install 17 Packages
Total download size: 23 M
Installed size: 98 M
Downloading Packages:
(1/17): python3.11-pycparser-2.21-5.el9pc.noarch.rpm 635 kB/s | 249 kB 00:00
(2/17): python3.11-cryptography-42.0.8-1.el9pc.x86_64.rpm 2.7 MB/s | 1.1 MB 00:00
(3/17): python3.11-cffi-1.15.1-5.el9pc.x86_64.rpm 712 kB/s | 299 kB 00:00
(4/17): mpdecimal-2.5.1-3.el9.x86_64.rpm 251 kB/s | 88 kB 00:00
(5/17): python3.11-pip-wheel-22.3.1-5.el9.noarch.rpm 3.9 MB/s | 1.4 MB 00:00
(6/17): python3.11-setuptools-wheel-65.5.1-4.el9_6.noarch.rpm 1.8 MB/s | 712 kB 00:00
(7/17): python3.11-setuptools-65.5.1-4.el9_6.noarch.rpm 3.7 MB/s | 1.7 MB 00:00
(8/17): python3.11-3.11.11-2.el9_6.2.x86_64.rpm 69 kB/s | 25 kB 00:00
(9/17): python3.11-libs-3.11.11-2.el9_6.2.x86_64.rpm 20 MB/s | 10 MB 00:00
(10/17): python3.11-packaging-23.2-1.el9ap.noarch.rpm 355 kB/s | 117 kB 00:00
(11/17): python3.11-pyyaml-6.0-1.el9.x86_64.rpm 122 kB/s | 229 kB 00:01
(12/17): python3.11-resolvelib-1.0.1-1.el9ap.noarch.rpm 104 kB/s | 39 kB 00:00
(13/17): ansible-core-2.16.14-2.el9ap.noarch.rpm 5.3 MB/s | 2.5 MB 00:00
(14/17): python3.11-jinja2-3.1.6-1.el9ap.noarch.rpm 846 kB/s | 327 kB 00:00
(15/17): python3.11-markupsafe-2.1.5-1.el9ap.x86_64.rpm 17 kB/s | 31 kB 00:01
(16/17): sshpass-1.09-5.el9ap.x86_64.rpm 19 kB/s | 27 kB 00:01
(17/17): ansible-automation-platform-installer-2.5-17.el9ap.noarch.rpm 1.6 MB/s | 3.6 MB 00:02
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
Total 4.1 MB/s | 23 MB 00:05
Running transaction check
Transaction check succeeded.
Running transaction test
Transaction test succeeded.
Running transaction
Preparing : 1/1
Installing : sshpass-1.09-5.el9ap.x86_64 1/17
Installing : python3.11-setuptools-wheel-65.5.1-4.el9_6.noarch 2/17
Installing : python3.11-pip-wheel-22.3.1-5.el9.noarch 3/17
Installing : mpdecimal-2.5.1-3.el9.x86_64 4/17
Installing : python3.11-3.11.11-2.el9_6.2.x86_64 5/17
Installing : python3.11-libs-3.11.11-2.el9_6.2.x86_64 6/17
Installing : python3.11-pycparser-2.21-5.el9pc.noarch 7/17
Installing : python3.11-pyyaml-6.0-1.el9.x86_64 8/17
Installing : python3.11-setuptools-65.5.1-4.el9_6.noarch 9/17
Installing : python3.11-cffi-1.15.1-5.el9pc.x86_64 10/17
Installing : python3.11-cryptography-42.0.8-1.el9pc.x86_64 11/17
Installing : python3.11-markupsafe-2.1.5-1.el9ap.x86_64 12/17
Installing : python3.11-jinja2-3.1.6-1.el9ap.noarch 13/17
Installing : python3.11-packaging-23.2-1.el9ap.noarch 14/17
Installing : python3.11-resolvelib-1.0.1-1.el9ap.noarch 15/17
Installing : ansible-core-1:2.16.14-2.el9ap.noarch 16/17
Installing : ansible-automation-platform-installer-2.5-17.el9ap.noarch 17/17
Running scriptlet: ansible-automation-platform-installer-2.5-17.el9ap.noarch 17/17
Verifying : python3.11-cffi-1.15.1-5.el9pc.x86_64 1/17
Verifying : python3.11-cryptography-42.0.8-1.el9pc.x86_64 2/17
Verifying : python3.11-pycparser-2.21-5.el9pc.noarch 3/17
Verifying : python3.11-pyyaml-6.0-1.el9.x86_64 4/17
Verifying : mpdecimal-2.5.1-3.el9.x86_64 5/17
Verifying : python3.11-pip-wheel-22.3.1-5.el9.noarch 6/17
Verifying : python3.11-setuptools-65.5.1-4.el9_6.noarch 7/17
Verifying : python3.11-setuptools-wheel-65.5.1-4.el9_6.noarch 8/17
Verifying : python3.11-3.11.11-2.el9_6.2.x86_64 9/17
Verifying : python3.11-libs-3.11.11-2.el9_6.2.x86_64 10/17
Verifying : python3.11-markupsafe-2.1.5-1.el9ap.x86_64 11/17
Verifying : python3.11-packaging-23.2-1.el9ap.noarch 12/17
Verifying : python3.11-resolvelib-1.0.1-1.el9ap.noarch 13/17
Verifying : sshpass-1.09-5.el9ap.x86_64 14/17
Verifying : ansible-core-1:2.16.14-2.el9ap.noarch 15/17
Verifying : python3.11-jinja2-3.1.6-1.el9ap.noarch 16/17
Verifying : ansible-automation-platform-installer-2.5-17.el9ap.noarch 17/17
Installed products updated.
Installed:
ansible-automation-platform-installer-2.5-17.el9ap.noarch ansible-core-1:2.16.14-2.el9ap.noarch mpdecimal-2.5.1-3.el9.x86_64 python3.11-3.11.11-2.el9_6.2.x86_64
python3.11-cffi-1.15.1-5.el9pc.x86_64 python3.11-cryptography-42.0.8-1.el9pc.x86_64 python3.11-jinja2-3.1.6-1.el9ap.noarch python3.11-libs-3.11.11-2.el9_6.2.x86_64
python3.11-markupsafe-2.1.5-1.el9ap.x86_64 python3.11-packaging-23.2-1.el9ap.noarch python3.11-pip-wheel-22.3.1-5.el9.noarch python3.11-pycparser-2.21-5.el9pc.noarch
python3.11-pyyaml-6.0-1.el9.x86_64 python3.11-resolvelib-1.0.1-1.el9ap.noarch python3.11-setuptools-65.5.1-4.el9_6.noarch python3.11-setuptools-wheel-65.5.1-4.el9_6.noarch
sshpass-1.09-5.el9ap.x86_64
Complete!
This package installs the Ansible Automation Platform installer under the following directory:
/opt/ansible-automation-platform/installer/The directory includes important components such as:
collections/inventory/inventory-growth/README.mdsetup.sh
Step 4: Create and Secure Credentials Using Ansible Vault
When deploying Ansible Automation Platform (AAP), you’ll need to authenticate to remote nodes as well as access Red Hat’s container registry. The required credentials include:
ansible_user: SSH username used to connect to managed nodesansible_password: SSH password for that user (if not using key-based authentication)
It is strongly recommended not to store these values in plain text. Instead, use Ansible Vault to encrypt and securely manage them.
Thus:
- Create a file to store the credentials. For example:
You can then paste the contents below and update them accordingly.vim vault.yml
You can also include sensitive variables required by the AAP components themselves as defined in the inventory file. These are used for setting admin passwords and connecting to internal databases:ansible_user: your-ssh-username
ansible_password: your-ssh-passwordautomationgateway_admin_passwordautomationgateway_pg_passwordadmin_passwordpg_passwordautomationhub_admin_passwordautomationhub_pg_passwordautomationedacontroller_admin_passwordautomationedacontroller_pg_password
- Encrypt the file using Ansible Vault (You will be prompted for a password to secure the vault):
ansible-vault encrypt vault.yml
- When running the installation setup, provide the vault password:
If you want, you can put the vault password in a file and reference the password file using the./setup.sh -- -e @vault.yml --ask-vault-pass--vault-password-fileoption.
Once you have the credentials on the vault, instead of hardcoding the values in the inventory file, you can reference them as variables:
[all:vars]
ansible_user={{ ansible_user }}
ansible_password={{ ansible_password }}This ensures your credentials are protected and the setup remains compliant with security best practices.
In addition to securely storing credentials using Ansible Vault, you may also need to configure how Ansible connects to managed nodes and performs privilege escalation especially when using a non-root user with sudo rights.
You can define the following Ansible variables in your inventory file:
ansible_become=True
ansible_become_method=sudo
ansible_become_password={{ ansible_become_password }} # defined in the vault alreadyThese settings ensure that the non-root user can escalate privileges using sudo when running tasks on remote nodes.
Also, if this is your first time connecting to remote nodes from the installation node, and you haven’t accepted their SSH keys before, you can temporarily disable host key checking to avoid interactive prompts. To do this, edit the default Ansible configuration file used by the AAP installer:
vim /etc/ansible/ansible.cfgAnd add or modify the following under the [defaults] section:
[defaults]
host_key_checking = FalseDisabling host key checking should only be used in trusted environments, such as initial setup or lab testing. Re-enable it for production deployments to avoid potential MITM risks.
Step 5: Edit the Inventory File
The inventory file is a configuration file that tells the AAP installer:
- Which AAP components to install (Controller, Hub, Database, etc.)
- Where to deploy each component (which servers/hosts)
- How to configure each component (database settings, passwords, network settings)
The AAP installer provides two inventory file templates, each tailored to a specific deployment scenario:
- inventory:
- Used for enterprise, high-availability deployments.
- Includes redundant nodes for each AAP component.
- Suitable for production environments needing fault tolerance and load balancing.
- inventory-growth:
- Used for non-redundant setups with one instance per component.
- Good for testing, development, or smaller environments.
- Easier to manage and more resource-efficient.
For this guide: Since we are just running a small AAP setup, we’ll update the inventory-growth template and configure all AAP components to run on the respective server nodes. This simplifies testing and evaluation but is not recommended for enterprise production due to lack of high availability and resource contention.
Hence, before you can proceed, navigate into the installer directory and backup the original inventory:
sudo su -cd /opt/ansible-automation-platform/installercp inventory-growth{,.bak}Next, let’s update the inventory files. Since we are deploying Red Hat Ansible Automation Platform (AAP) in a 6-node setup, let’s begin by:
- Replacing all
.example.orghostnames with a reachable/valid FQDN with no-or_characters. See our hostnames definition in step 2 above. - Updating connections username and password.
Hence, run the command below. Replace the domain name of your AAP components accordingly.
sed -i 's/example.org/kifarunix.com/g' inventory-growthSample customized inventory files:
cat inventory-growth# This is the AAP installer inventory file intended for the RPM growth deployment topology.
# Please consult the Ansible Automation Platform product documentation about this topology's tested hardware configuration.
# https://docs.redhat.com/en/documentation/red_hat_ansible_automation_platform/2.5/html/tested_deployment_models/rpm-topologies
#
# Please consult the docs if you're unsure what to add
# For all optional variables please consult the Ansible Automation Platform documentation:
# https://docs.redhat.com/en/documentation/red_hat_ansible_automation_platform/2.5/html/rpm_installation
# This section is for your AAP Gateway host(s)
# -----------------------------------------------------
[automationgateway]
gateway.kifarunix.com
# This section is for your AAP Controller host(s)
# -----------------------------------------------------
[automationcontroller]
controller.kifarunix.com
[automationcontroller:vars]
peers=execution_nodes
# This section is for your AAP Execution host(s)
# -----------------------------------------------------
[execution_nodes]
exec.kifarunix.com
# This section is for your AAP Automation Hub host(s)
# -----------------------------------------------------
[automationhub]
hub.kifarunix.com
# This section is for your AAP EDA Controller host(s)
# -----------------------------------------------------
[automationedacontroller]
eda.kifarunix.com
# This section is for the AAP database
# -----------------------------------------------------
[database]
db.kifarunix.com
[all:vars]
ansible_user={{ ansible_user }}
ansible_password={{ ansible_password }}
ansible_become=True
ansible_become_method=sudo
ansible_become_password={{ ansible_become_password }}
# Common variables
# https://docs.redhat.com/en/documentation/red_hat_ansible_automation_platform/2.5/html/rpm_installation/appendix-inventory-files-vars#ref-general-inventory-variables
# -----------------------------------------------------
registry_username=
registry_password=
redis_mode='standalone'
# AAP Gateway
# https://docs.redhat.com/en/documentation/red_hat_ansible_automation_platform/2.5/html/rpm_installation/appendix-inventory-files-vars#ref-gateway-variables
# -----------------------------------------------------
automationgateway_admin_password={{ automationgateway_admin_password }}
automationgateway_pg_host=db.kifarunix.com
automationgateway_pg_password={{ automationgateway_pg_password }}
# AAP Controller
# https://docs.redhat.com/en/documentation/red_hat_ansible_automation_platform/2.5/html/rpm_installation/appendix-inventory-files-vars#ref-controller-variables
# -----------------------------------------------------
admin_password={{ admin_password }}
pg_host=db.kifarunix.com
pg_password={{ pg_password }}
# AAP Automation Hub
# https://docs.redhat.com/en/documentation/red_hat_ansible_automation_platform/2.5/html/rpm_installation/appendix-inventory-files-vars#ref-hub-variables
# -----------------------------------------------------
automationhub_admin_password={{ automationhub_admin_password }}
automationhub_pg_host=db.kifarunix.com
automationhub_pg_password={{ automationhub_pg_password }}
# AAP EDA Controller
# https://docs.redhat.com/en/documentation/red_hat_ansible_automation_platform/2.5/html/rpm_installation/appendix-inventory-files-vars#event-driven-ansible-controller
# -----------------------------------------------------
automationedacontroller_admin_password={{ automationedacontroller_admin_password }}
automationedacontroller_pg_host=db.kifarunix.com
automationedacontroller_pg_password={{ automationedacontroller_pg_password }} Step 6: Running AAP Installer Setup Script
Once you are done editing the inventory file, run the setup script to begin the installation.
- If you did not use Ansible Vault to store credentials, simply run:
./setup.sh -i inventory-growth - If you used Ansible Vault to encrypt sensitive variables (e.g., passwords, SSH credentials), run:
./setup.sh -i inventory-growth -- -e @vault.yml --ask-vault-pass
This will prompt you for the vault password and apply the encrypted variables during installation.
If all goes well, your AAP should be installed in a short while. Sample setup logs:
...
TASK [ansible.automation_platform_installer.misc : Unregister from Insights] ***
skipping: [gateway.kifarunix.com] => {"changed": false, "false_condition": "not enable_insights_collection | bool", "skip_reason": "Conditional result was False"}
skipping: [controller.kifarunix.com] => {"changed": false, "false_condition": "not enable_insights_collection | bool", "skip_reason": "Conditional result was False"}
skipping: [hub.kifarunix.com] => {"changed": false, "false_condition": "not enable_insights_collection | bool", "skip_reason": "Conditional result was False"}
skipping: [eda.kifarunix.com] => {"changed": false, "false_condition": "not enable_insights_collection | bool", "skip_reason": "Conditional result was False"}
skipping: [db.kifarunix.com] => {"changed": false, "false_condition": "not enable_insights_collection | bool", "skip_reason": "Conditional result was False"}
skipping: [exec.kifarunix.com] => {"changed": false, "false_condition": "not enable_insights_collection | bool", "skip_reason": "Conditional result was False"}
PLAY [Install PCP and configure pmproxy] ***************************************
TASK [include_role : monitoring] ***********************************************
skipping: [gateway.kifarunix.com] => {"changed": false, "false_condition": "setup_monitoring | default(false) | bool", "skip_reason": "Conditional result was False"}
skipping: [controller.kifarunix.com] => {"changed": false, "false_condition": "setup_monitoring | default(false) | bool", "skip_reason": "Conditional result was False"}
skipping: [hub.kifarunix.com] => {"changed": false, "false_condition": "setup_monitoring | default(false) | bool", "skip_reason": "Conditional result was False"}
skipping: [eda.kifarunix.com] => {"changed": false, "false_condition": "setup_monitoring | default(false) | bool", "skip_reason": "Conditional result was False"}
skipping: [db.kifarunix.com] => {"changed": false, "false_condition": "setup_monitoring | default(false) | bool", "skip_reason": "Conditional result was False"}
PLAY [Post-install cleanup] ****************************************************
TASK [Remove stale packages] ***************************************************
ok: [controller.kifarunix.com] => {"changed": false, "msg": "Nothing to do", "rc": 0, "results": []}
ok: [db.kifarunix.com] => {"changed": false, "msg": "Nothing to do", "rc": 0, "results": []}
ok: [eda.kifarunix.com] => {"changed": false, "msg": "Nothing to do", "rc": 0, "results": []}
ok: [gateway.kifarunix.com] => {"changed": false, "msg": "Nothing to do", "rc": 0, "results": []}
changed: [hub.kifarunix.com] => {"changed": true, "msg": "", "rc": 0, "results": ["Removed: grub2-tools-efi-1:2.06-104.el9_6.x86_64", "Removed: grub2-tools-extra-1:2.06-104.el9_6.x86_64"]}
ok: [exec.kifarunix.com] => {"changed": false, "msg": "Nothing to do", "rc": 0, "results": []}
PLAY RECAP *********************************************************************
controller.kifarunix.com : ok=345 changed=115 unreachable=0 failed=0 skipped=224 rescued=0 ignored=5
db.kifarunix.com : ok=92 changed=24 unreachable=0 failed=0 skipped=74 rescued=0 ignored=0
eda.kifarunix.com : ok=216 changed=55 unreachable=0 failed=0 skipped=182 rescued=0 ignored=0
exec.kifarunix.com : ok=117 changed=33 unreachable=0 failed=0 skipped=103 rescued=0 ignored=1
gateway.kifarunix.com : ok=210 changed=44 unreachable=0 failed=0 skipped=220 rescued=0 ignored=2
hub.kifarunix.com : ok=248 changed=42 unreachable=0 failed=0 skipped=206 rescued=0 ignored=0
localhost : ok=0 changed=0 unreachable=0 failed=0 skipped=1 rescued=0 ignored=0
The setup process completed successfully.
Setup log saved to /var/log/tower/setup-2025-09-21-14:01:16.log.Bottom line: The setup process completed successfully.
Systemd Services Created by the RPM-Based Installer
When deploying Red Hat Ansible Automation Platform using the RPM-based installer, several systemd services are automatically created and enabled to manage the core components of the platform. These services ensure that essential components such as the automation controller, automation hub, and event-driven Ansible are started at boot and managed consistently across the system. Each service corresponds to a key part of the platform and allows administrators to control them using standard systemctl commands (e.g., start, stop, enable, restart, and status).
Platform Gateway services:
- automation-gateway-proxy.service: Main gateway proxy service
- nginx.service: Web server for gateway UI/reverse proxy
- redis.service: Redis for session management and caching
- supervisord.service: Process supervisor
Automation Controller systemd services:
- automation-controller.service: Main automation controller service
- nginx.service: Web server for controller UI/API
- receptor.service: Mesh networking and job execution
- supervisord.service: Process supervisor managing AWX processes
Event-Drive Ansible Services:
- automation-eda-controller.service: Main EDA controller service
- automation-eda-controller-daphne.service: ASGI/WebSocket server
- automation-eda-controller-scheduler.service: Event scheduling service
- automation-eda-controller-event-stream.service: Event stream processing
- nginx.service: Web server for EDA UI/API
- automation-eda-controller-default-worker: Handle general background tasks
- automation-eda-controller-activation-worker: Handle rulebook activations and event processing
Automation Hub services:
- pulpcore.service: Main Pulp core service
- pulpcore-api.service: Pulp REST API service
- pulpcore-content.service: Content delivery service
- redis.service: Redis for caching and task queuing
- nginx.service: Web server for Hub UI/API
- pulpcore-worker: Content processing worker
Execution Nodes:
- receptor.service: Mesh networking and job execution
Database Server:
- postgresql.service: Main PostgreSQL database service
Activating Red Hat Ansible Automation Platform
After installing Red Hat Ansible Automation Platform (AAP) 2.5, administrators and users primarily interact with it through the web-based user interface (UI).
Before accessing the full platform features, you must first activate your AAP subscription by logging in to the Platform Gateway at:
https://gateway.<domain>.comThe Gateway acts as the central entry point, giving you unified access to Automation Controller, Automation Hub, and Event-Driven Ansible (EDA).
Sample web user login interface:
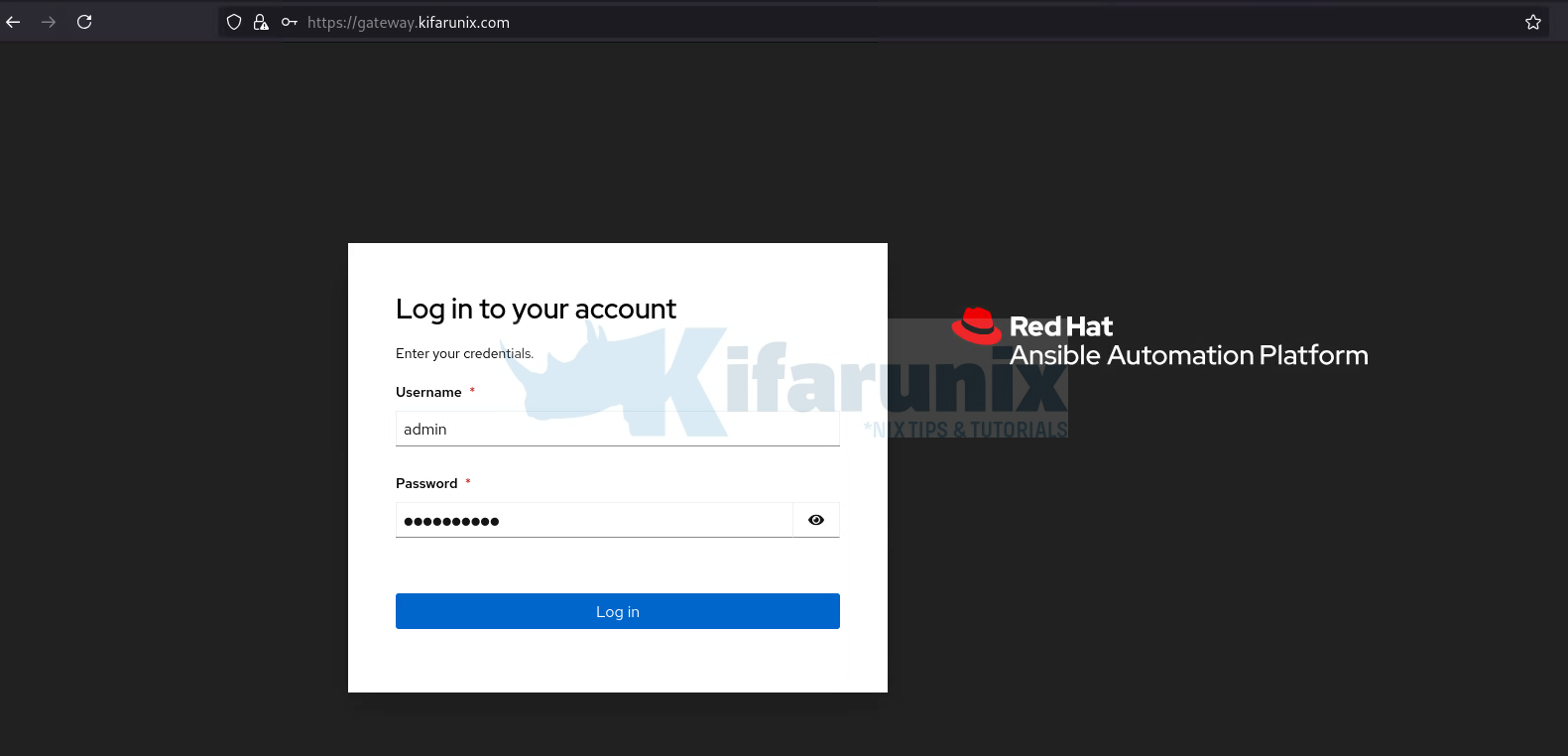
By default, the login credentials for the AAP Web UI come from what you define in your Ansible inventory file during installation.
The default username is admin, and the password is the value you set for the admin_password variable in your inventory file during installation.
When you login, you land on the AAP activation page.
There are different methods you can use to activate AAP:
Option 1: Activate Using Credentials
Use this method if you’re an Organization Administrator (recommended) with a Red Hat Registry Service Account (Client ID and Secret). You can see how to create a service account on Red Hat documentation page.
If you’re a non-admin, you can use your Red Hat Customer Portal username and password instead.
If your AAP is connected to Red Hat Satellite, use your Satellite username and password.
Once you have that information;
- Go back to AAP web UI (https://<gateway.domain.com>).
- On the subscription activation page, select Service Account/Red Hat Satellite as the activation method.
- Enter your Client ID and Secret, or Satellite credentials. We use Satellite admin credentials in this setup.
- Select the appropriate subscription from the list.
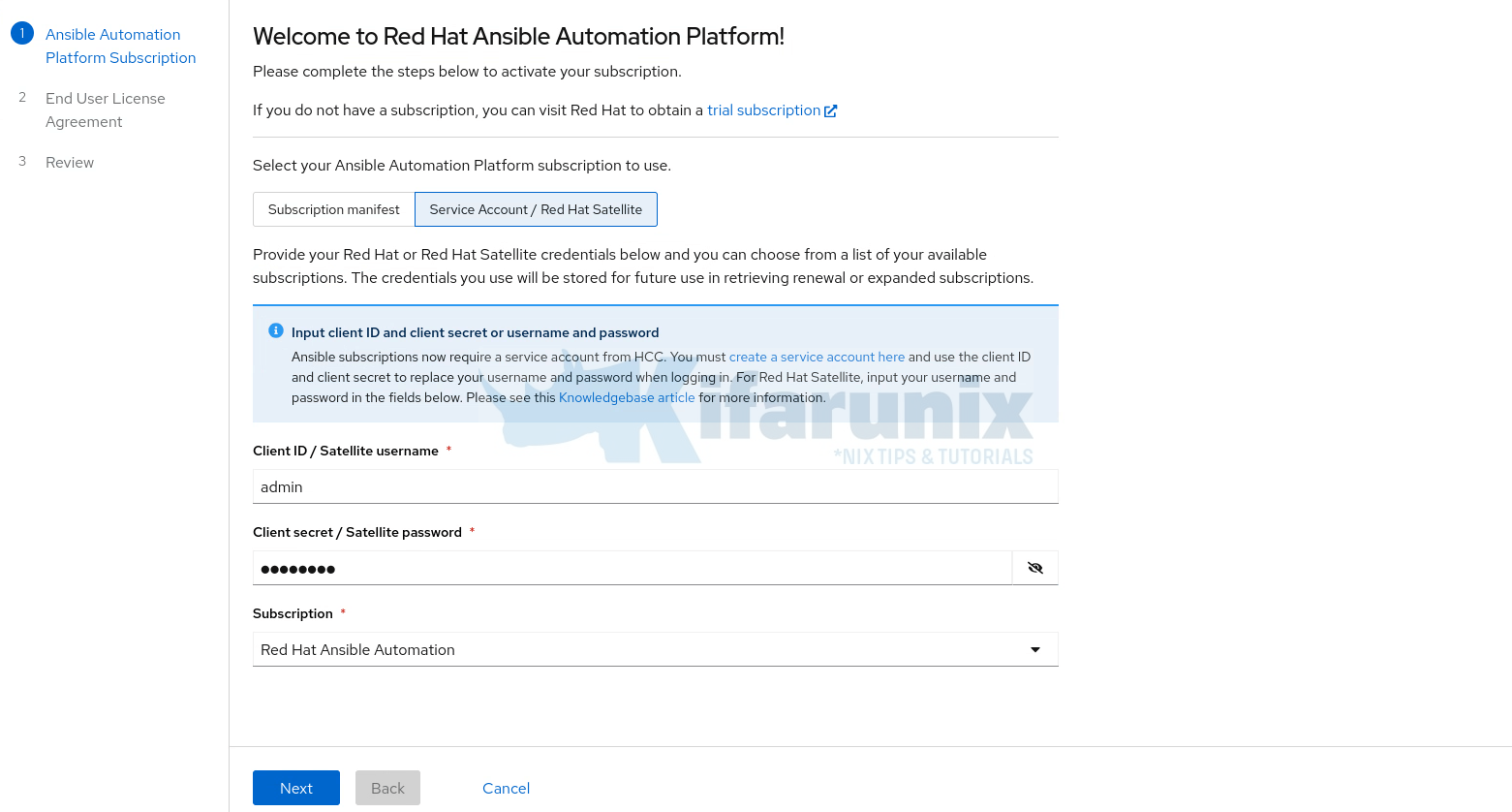
- Go to the Next page and accept the End User License Agreement (EULA).
- Click Finish to activate the AAP.
Verification:
- If successful, you’ll see your subscription listed with status: Compliant.
- If you exceed your entitled node count, the status will show Out of Compliance.
Option 2: Activate AAP with a Manifest File
You can activate Red Hat Ansible Automation Platform (AAP) using a subscription manifest file obtained from the Red Hat Customer Portal.
Once you have the manifest file;
- Log in to the Red Hat Ansible Automation Platform interface.
- If you are not prompted for a manifest file immediately, navigate to Settings > Subscription.
- Select Subscription manifest.
- Click Browse and locate your subscription manifest file.
- Review and accept the End User License Agreement.
- Click Finish to activate the AAP.
Navigating through AAP Interface
After the activation, you will be redirected to the overview page.
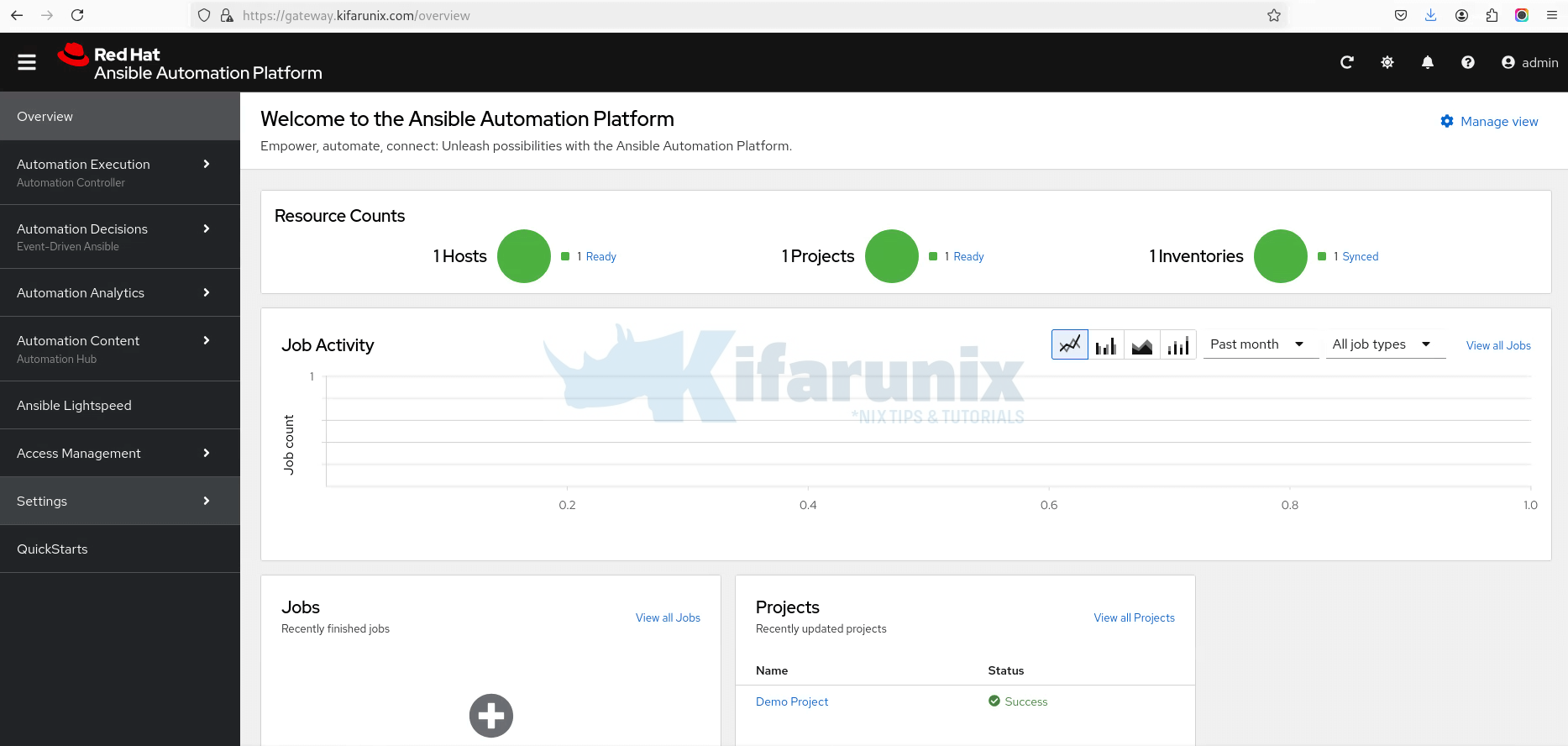
From the left menu panel, you can access services like the Ansible controller, EDA, the Hub, analytics, and other functionalities/settings.
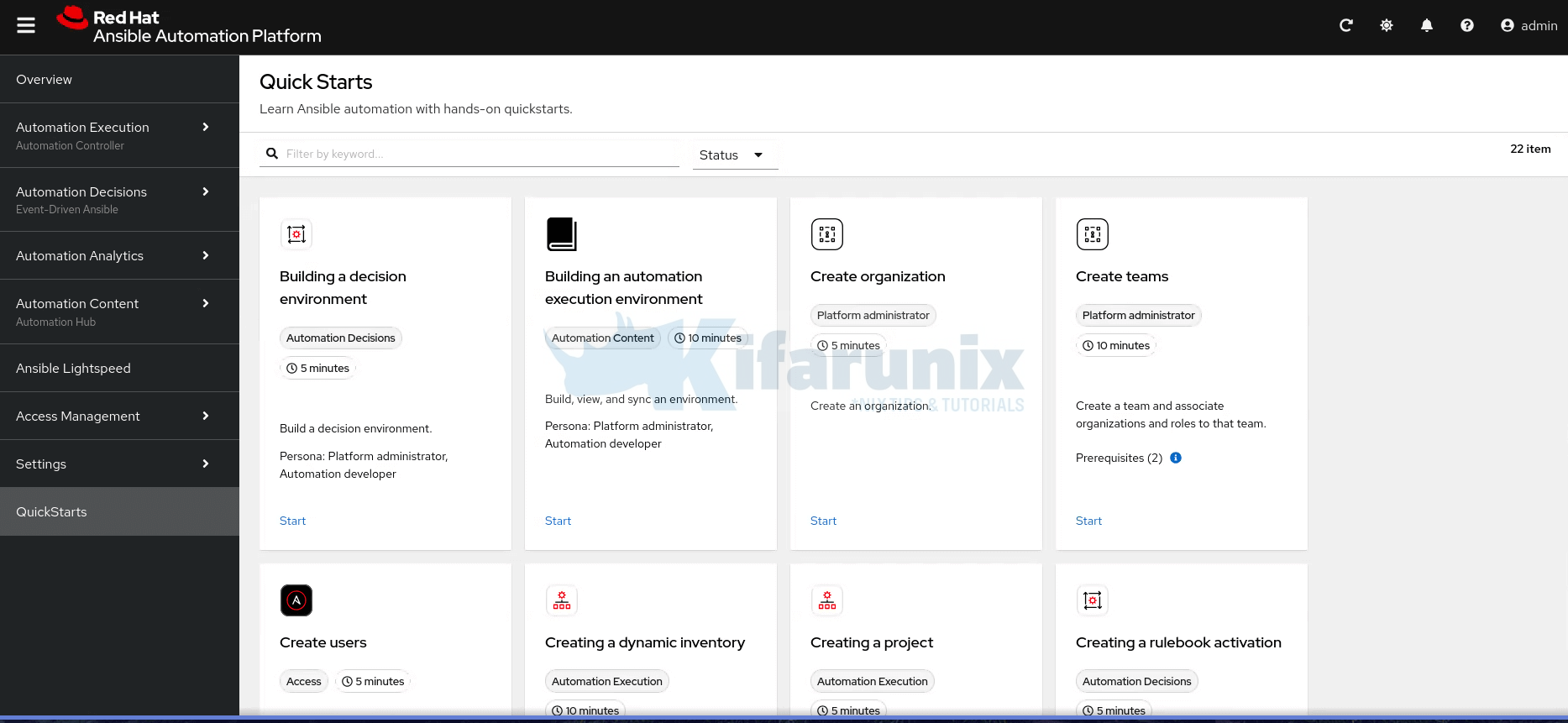
You can easily get started with Ansible Automation Platform by using the built-in QuickStarts: short, interactive guides for common tasks.
Next Steps After Installation
Now that you’ve successfully installed Red Hat Ansible Automation Platform, you’re ready to start using its key features. Here are some recommended guides to help you get started:
- Getting started with Ansible Automation Platform: Learn the basics of navigating the platform and configuring your environment.
- Managing automation content: Understand how to organize, import, and curate Ansible content such as playbooks, roles, and collections.
- Creating and using execution environments: Discover how to build and run isolated environments for executing your automation tasks.
Conclusion
That marks the end of our guide on how to install Ansible Automation Platform on RHEL 9 using RPM based installer on a 6-node architecture. This setup provides a robust and scalable foundation that includes:
- Automation Controller
- Automation Hub
- Event-Driven Ansible (EDA) Controller
- Platform Gateway
- Execution Node
- Centralized Database
This multi-node deployment ensures separation of concerns, better performance, and easier scaling for enterprise automation workloads.
With the platform now installed and services running, you’re ready to begin building, managing, and scaling your automation strategies using Ansible’s powerful capabilities.
For more details on using the platform, see the official Red Hat documentation

