
In this blog post, we will take you through how to install and configure Fetchmail with OAuth2 support for Request Tracker (RT). OAuth2 has become increasingly necessary for email retrieval from major providers like Google and Microsoft, who have implemented stricter security policies. While Fetchmail version 7 includes OAuth2 capabilities, setting it up requires several careful steps including creating cloud projects, obtaining client credentials, and managing access tokens. This guide will walk you through the entire process to ensure your Request Tracker system can reliably retrieve emails using modern authentication methods, even as service providers continue to phase out traditional password-based access.
Table of Contents
Install and Configure Fetchmail with OAuth2 Support for Request Tracker
Install and Configure Request Tracker
We are setting up Fetchmail specifically for RT. Hence, if you are looking for guides on how to setup Request Tracker on Linux, follow the link below;
Install and setup Request Tracker on Linux
Create Fetchmail System Account
Switch to root user or at least be logged in as user with sudo privileges so you can prefix the commands below with sudo;
sudo su -Create a system account to use for running Fetchmail.
useradd -m -d /var/lib/fetchmail -r -s /usr/bin/false fetchmailCreate Fetchmail configuration directory.
mkdir /etc/fetchmailInstall Fetchmail with OAuth2 Support
Fetchmail is an open-source utility that retrieves emails from remote servers (supporting POP3, IMAP4, ETRN, ODMR) and forwards them to local mail systems. It offers strong security features including multiple authentication methods and encryption options, making it ideal for securely managing email delivery over various network connections.
Fetchmail 7 adds support for OAuth2 and thus, you have to build it from the source code.
Next, optionally create a temporary directory to keep the Fetchmail 7 project source code.
mkdir /tmp/fetchmail7cd /tmp/fetchmail7Clone the Fetchmail 7 git repository into your local system directory;
git clone https://gitlab.com/fetchmail/fetchmail.gitAfter that, you should have fetchmail project directory on your system.
ls -lAtotal 4
drwxr-xr-x 14 root root 4096 Mar 18 04:55 fetchmailNavigate into that directory;
cd fetchmailBefore you can proceed, install some of the required package dependencies. (The command below is for Debian/Ubuntu systems. If using a different OS, consult respective system documentation on how to install the packages).
apt install bison byacc flex -yInstall Gettext version 0.23.1, currently not available on default Ubuntu 24.04 LTS repos, hence use repos for Ubuntu 25.04:
echo "deb http://archive.ubuntu.com/ubuntu plucky main" | sudo tee /etc/apt/sources.list.d/plucky.listapt updateapt install gettext autopoint -yDisable the Ubuntu 25.04 repo after installing the above packages:
sed -i 's/^/#/' /etc/apt/sources.list.d/plucky.listapt updateThen switch to a remote Fetchmail next branch.
git checkout -t origin/nextGenerate configuration files (like configure script) for building Fetchmail.
./autogen.shNext, run the generated configure script to check system dependencies and prepare the build environment by creating necessary Makefiles for the project.
./configureCompiles the project;
make -j10In case you encounter such an error;
cc1: fatal error: rcfile_l.c: No such file or directory
compilation terminated.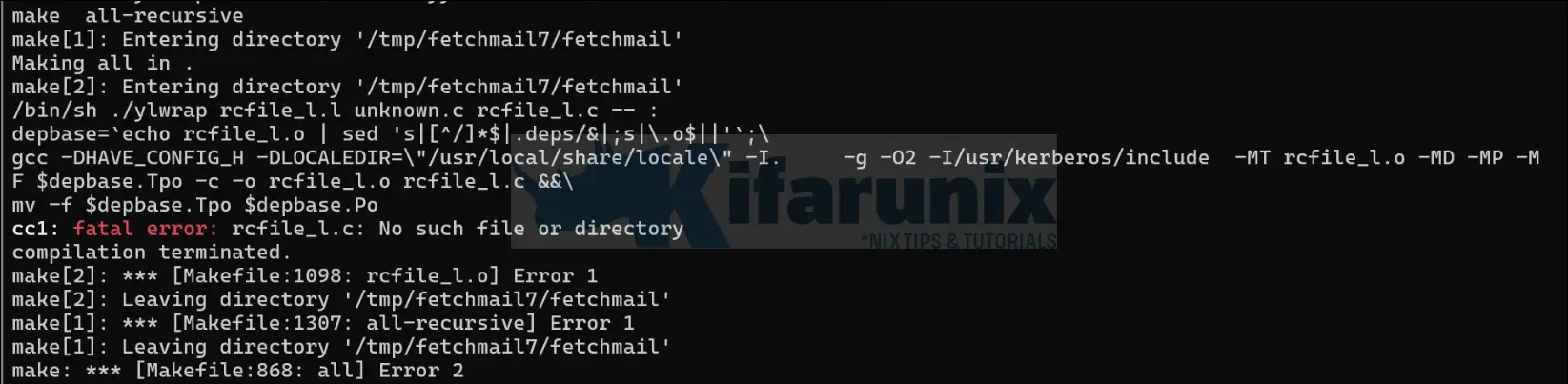
This typically means that a required source file (rcfile_l.c) was not generated before the build process. You can resolve it as follows:
Manually generate the missing file rcfile_l.c:
flex -o rcfile_l.c rcfile_l.lClean and rebuild:
make clean
./configure
make -j10
Next, run the project’s tests;
make check -j10Sample checks report;
============================================================================
Testsuite summary for fetchmail 7.0.0-alpha11
============================================================================
# TOTAL: 7
# PASS: 5
# SKIP: 2
# XFAIL: 0
# FAIL: 0
# XPASS: 0
# ERROR: 0
============================================================================
Install Fetchmail.
sudo make installConfirm the installation;
fetchmail -VMar 18 07:41:12 fetchmail: WARNING: Running as root is discouraged.
This is fetchmail release 7.0.0-alpha11+TLS+NLS.
Compiled with SSL library 0x300000d0 "OpenSSL 3.0.13 30 Jan 2024"
Run-time uses SSL library 0x300000d0 "OpenSSL 3.0.13 30 Jan 2024"
OpenSSL: OPENSSLDIR: "/usr/lib/ssl"
Engines: ENGINESDIR: "/usr/lib/x86_64-linux-gnu/engines-3"
Copyright (C) 2002, 2003 Eric S. Raymond
Copyright (C) 2004 Matthias Andree, Eric S. Raymond,
Robert M. Funk, Graham Wilson
Copyright (C) 2005 - 2012 Sunil Shetye
Copyright (C) 2005 - 2025 Matthias Andree
Fetchmail comes with ABSOLUTELY NO WARRANTY. This is free software, and you
are welcome to redistribute it under certain conditions. For details,
please see the file COPYING in the source or documentation directory.
This product includes software developed by the OpenSSL Project
for use in the OpenSSL Toolkit. (http://www.openssl.org/)
Linux rt.kifarunix.com 6.8.0-54-generic #56-Ubuntu SMP PREEMPT_DYNAMIC Sat Feb 8 00:37:57 UTC 2025 x86_64 x86_64 x86_64 GNU/Linux
Taking options from command line
No mailservers set up -- perhaps /root/.fetchmailrc is missing?
Setup OAuth2 Authentication for Fetchmail
The general workflow of Fetchmail with OAuth2 support is that you need to create a project on your respective mail service provider (e.g., Google Cloud or Microsoft Azure…), which generates a client_id and client_secret. These credentials will be used to configure Fetchmail OAuth2 script to request OAuth access tokens from the respective mail service provider.
Fetchmail will then use these tokens like a password to access your email account.
Access tokens also have an expiry period. As such, refresh token is also required for the Fetchmail OAuth2 script to use it to request new tokens upon expiry of the old ones.
Microsoft 365: How to Obtain OAuth2 Client Secret and ID
As a user with correct permissions to manage apps, navigate to Azure AD portal.
Once you have logged in, search for App Registrations on the search bar.
Click on App registrations > + New registrations.
On the Registration Page:
- Enter the project name as “fetchmail-oauth2” or any name of your preference.
- Select “Accounts in this organizational directory only (Single tenant)” under “Supported account types“.
- Specify “http://localhost” for the “Redirect URI” and choose Web as the type.
- Click “Register” to complete the registration process.
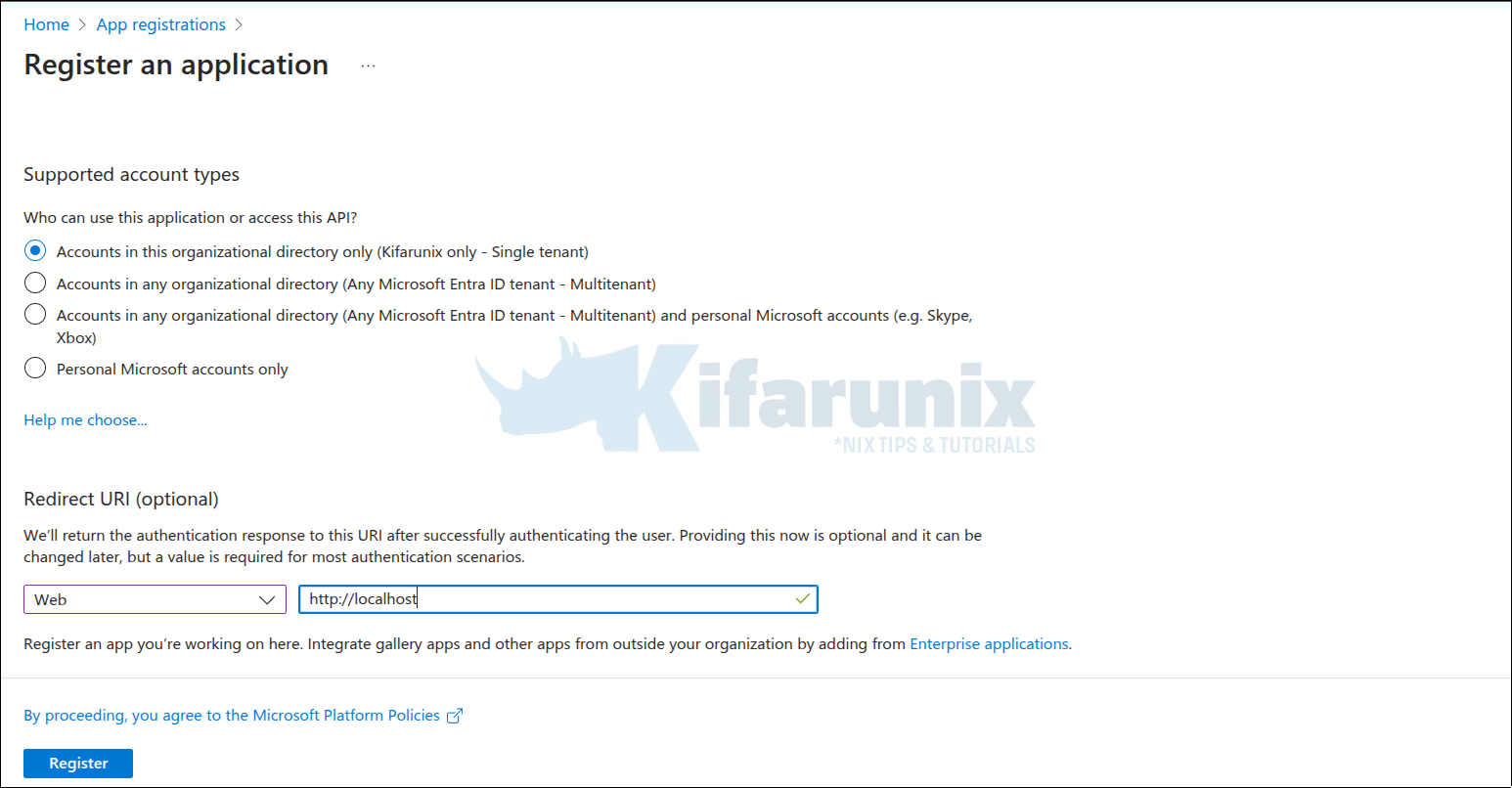
When you click Register, the app will be registered and you are taken to details page for the new App.
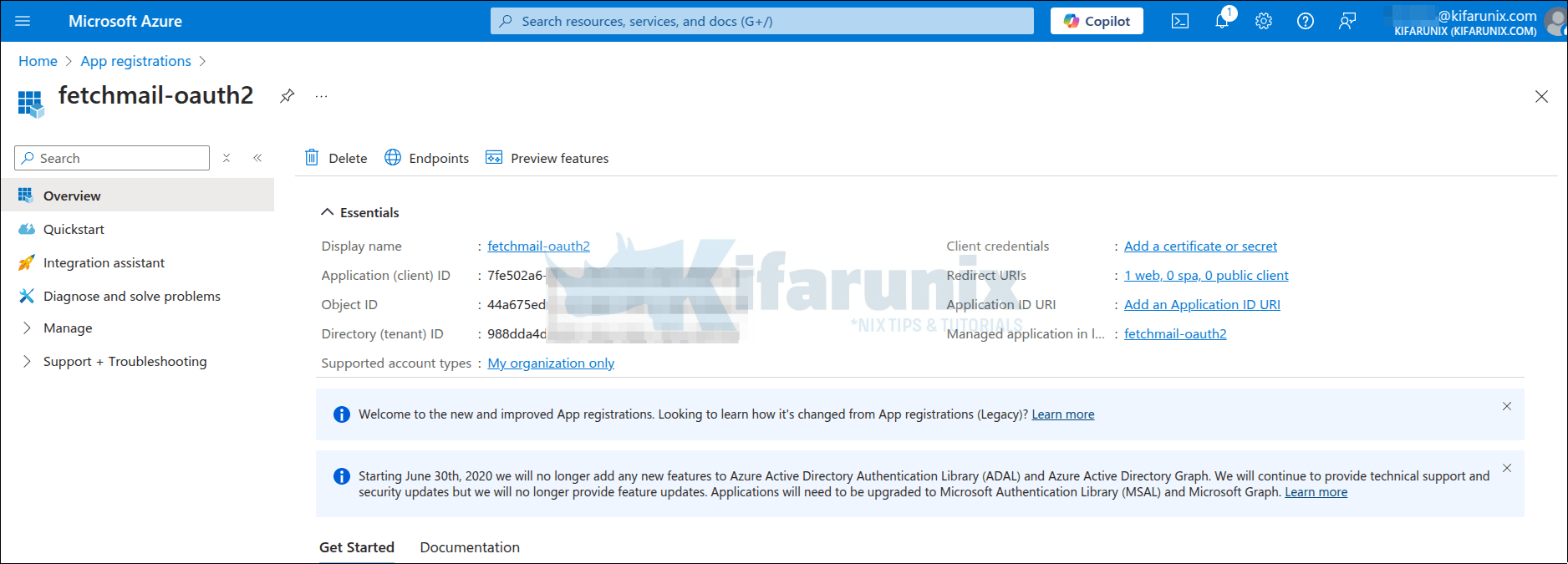
Copy the Application (client) ID and Directory (tenant) ID and save them somewhere safe as we will need them in the next steps.
Under Client credentials, click the Add a certificate or secret to create credentials that enable confidential applications to identify themselves to the authentication service when receiving tokens.
Once you open the certificate and secrets page, click New client secret under client secrets.
Enter the secret description and expiry period.
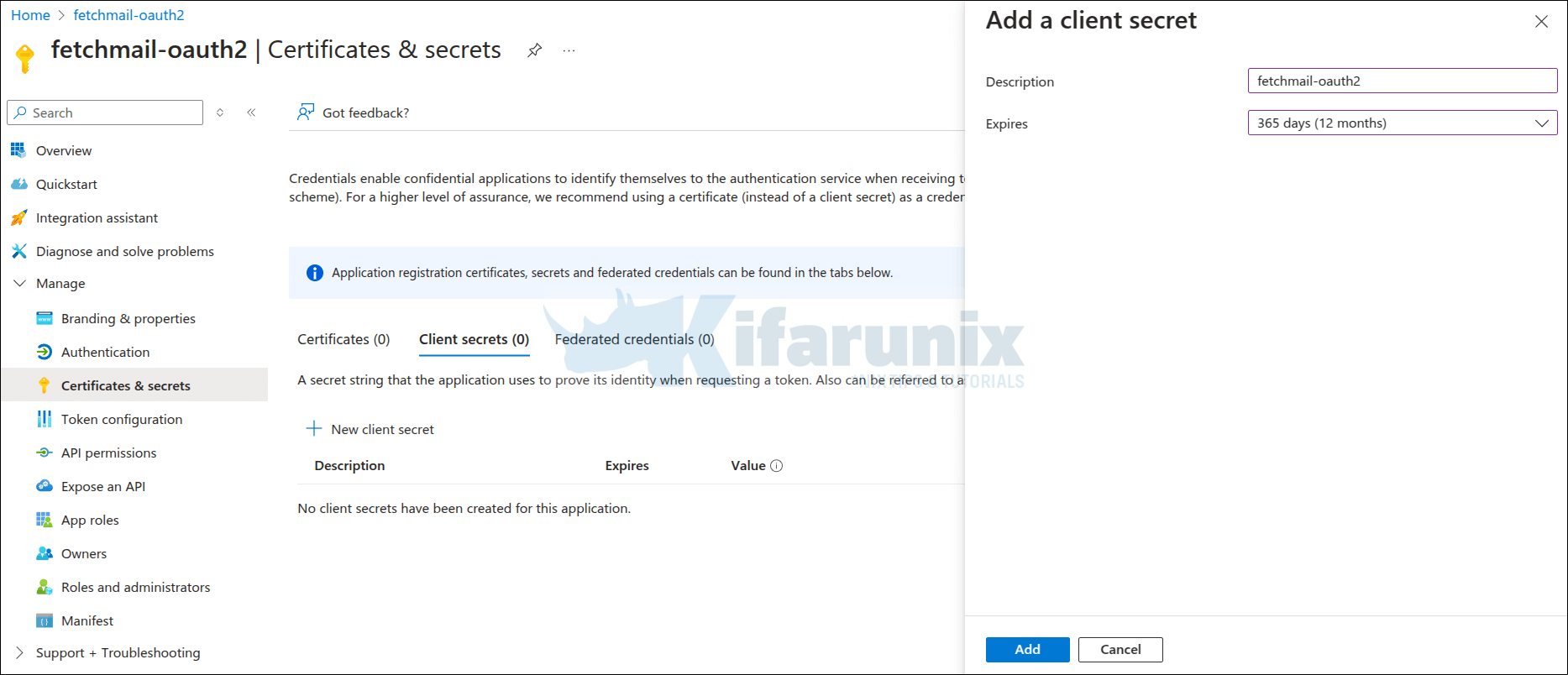
Click Add.
The secret is then displayed. Copy the Value of the secret and keep it somewhere safe as we will need it in the next steps.
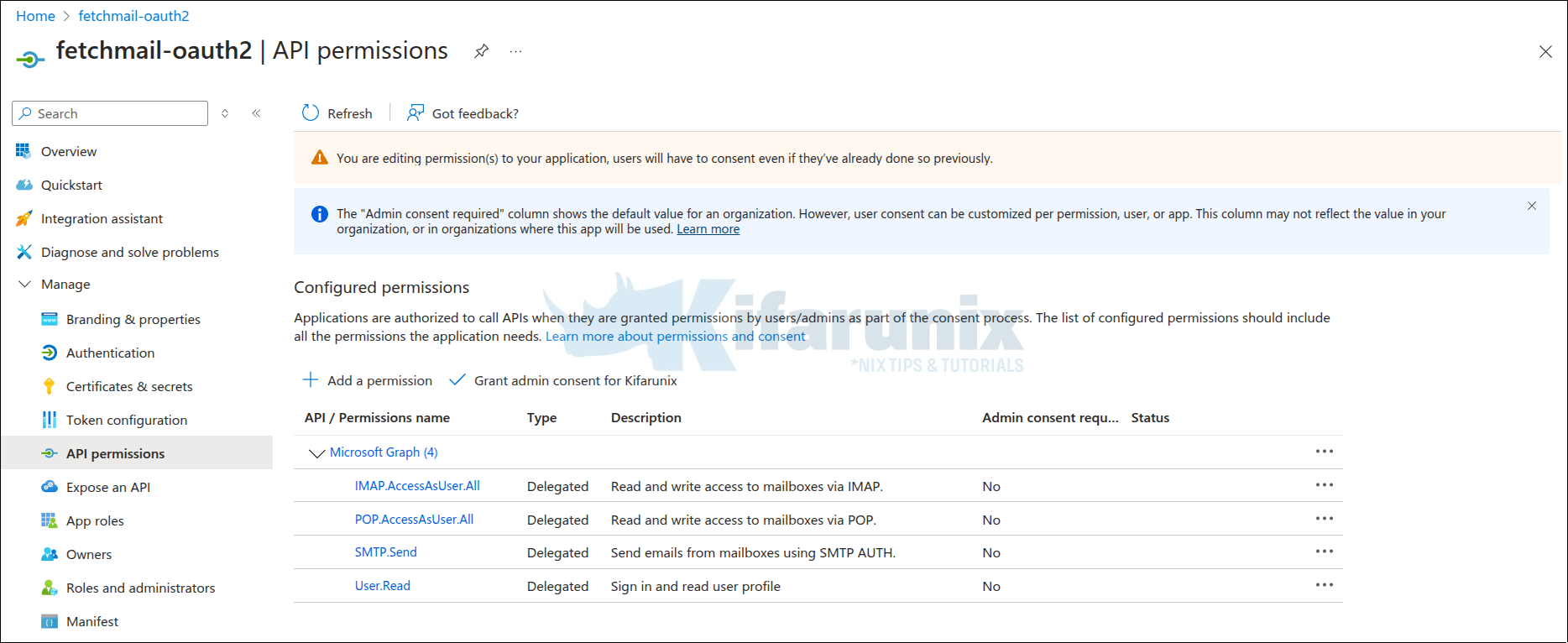
Configure API Permissions for Fetchmail App Access to Email:
- In the left menu, select “API permissions”.
- Click on “Add a permission”.
- Choose “Microsoft Graph” and then “Delegated Permissions”.
- Search for and select the following permissions:
- IMAP.AccessAsUser.All
- POP.AccessAsUser.All
- SMTP.Send
- Click “Add permissions”.
Google: How to Obtain OAuth2 Client Secret and ID
Open the Google API Dashboard, select your country, and agree to the terms of service.
Create a New Project:
- Click “NEW PROJECT”.
- Enter the project name (e.g., “fetchmail”).
- Set “Location” as “No organization” (unless using G Suite).
- Make a note of the Project ID (e.g., “fetchmail-123456”).
- Click “CREATE”.
Switch to the New Project:
- Select the new project either from the “SELECT PROJECT” window or the title bar dropdown.
Configure OAuth Consent Screen:
- In the left menu, go to “Credentials”.
- Click “+ CREATE CREDENTIALS” and select “OAuth client ID”.
- Click on “CONFIGURE CONSENT SCREEN”.
- Choose “External” as the user type.
- Fill out the required fields:
- App name: Use the full project name (e.g., “fetchmail-123456”).
- User support email: Enter your Gmail email.
- Leave app logo, home page, privacy policy, and terms of service empty.
- Developer contact email: Enter your Gmail email.
- Click “SAVE AND CONTINUE”.
Enable Gmail API Scopes:
- In the “Edit app registration” screen, click “ADD OR REMOVE SCOPES”.
- In the Google API Library, filter for “Email” and enable the Gmail API.
- Return to the “Edit app registration” tab and refresh.
- Under “Scopes”, select
.../auth/gmail.modify. - Click “SAVE AND CONTINUE”.
Add Test Users:
- Click on “+ ADD USERS” in the “Test Users” section.
- Enter your Gmail address and click “ADD”.
- Click “SAVE AND CONTINUE”.
Create OAuth2 Client Credentials:
- Go back to “Credentials”.
- Click “+ CREATE CREDENTIALS” and select “OAuth client ID”.
- Choose “Desktop app” as the application type.
- Name the client (e.g., “DesktopClient1”).
- Click “CREATE”.
- Copy the Client ID and Client Secret from the pop-up window.
Configure Fetchmail OAuth2 Script for Access Tokens Request
Create Fetchmail OAuth2 script configuration file on your preferred directory. In this guide, we will install the configuration under the Fetchmail configuration directory.
Before you can proceed, copy the Fetchmail OAuth2 python script itself into the Fetchmail configuration directory we created above.
cp contrib/fetchmail-oauth2.py /etc/fetchmailMake the script executable:
chmod +x /etc/fetchmail/fetchmail-oauth2.pyConfigure script to use Python3 by changing the shebang (#!/usr/bin/python) to #!/usr/bin/python3 in the file
sed -i '1s|#!/usr/bin/python|#!/usr/bin/python3|' /etc/fetchmail/fetchmail-oauth2.pyConfirm that the script is working:
/etc/fetchmail/fetchmail-oauth2.py --helpUsage: Performs client tasks for testing IMAP OAuth2 authentication.
This documentation and examples is for gmail. For other providers,
you will likely need to track down appropriate non-default settings
for auth_url, token_url, and scope.
To use this script, you'll need to have registered with Google as an OAuth
application and obtained an OAuth client ID and client secret.
See https://developers.google.com/identity/protocols/OAuth2 and
https://developers.google.com/identity/sign-in/web/devconsole-project
for instructions on registering and for documentation of the APIs
invoked by this code.
This script has 2 main modes of operation.
1. The first mode is used to generate and authorize an OAuth2 token, the
first step in logging in via OAuth2.
First, after registering your "application" (above) you should setup a
configuration file. Use a text editor to do the command-line equivalent of:
sed 's/^ *//' > /path/to/oauth2Config.properties << EOF
client_id=1038[...].apps.googleusercontent.com
client_secret=VWFn8LIKAMC-MsjBMhJeOplZ
refresh_token_file=/home/path/to/refresh_token_file
access_token_file=/home/path/to/access_token_file
EOF
chmod 600 /path/to/oauth2Config.properties
Then run the following, and repeat any time the refresh token stops
working, such as when you change your password. This is interactive
and requires a web browser to complete:
oauth2 -c /path/to/oauth2Config.properties --obtain_refresh_token_file
The script will converse with Google and generate an oauth request
token, then present you with a URL you should visit in your browser to
authorize the token. Once you get the verification code from the Google
website, enter it into the script, which will then save access and referesh
tokens to the corresponding files for later use.
Also, you'll usually need to configure fetchmail by
including a section like the following in your .fetchmailrc:
poll imap.gmail.com protocol imap
auth oauthbearer username "[email protected]"
passwordfile "/home/path/to/access_token_file"
is LOCALUSER here sslmode wrapped sslcertck
Alternative for debugging: You can also use the original google
script interface to obtain these tokens without involving files:
oauth2 --client_id=1038[...].apps.googleusercontent.com --client_secret=VWFn8LIKAMC-MsjBMhJeOplZ --generate_oauth2_token
-----
2. The script will generate new access tokens using a refresh token.
This uses the same config file setup above.
oauth2 -c /path/to/oauth2Config.properties --auto_refresh
# Or force refresh by using --refresh instead of --auto_refresh.
fetchmail -s # or other tools configured to use the access_token_file
# And/or call something to update outgoing MTA relay configuration,
# if necessary.
You may put this sequence in a short shell script,
and configure cron to call it a few times per hour.
Alternative for debugging: You can also use the original google
script interface to refresh the token without involving files:
oauth2 --client_id=1038[...].apps.googleusercontent.com --client_secret=VWFn8LIKAMC-MsjBMhJeOplZ --refresh_token=1/Yzm6MRy4q1xi7Dx2DuWXNgT6s37OrP_DW_IoyTum4YA
-----
Google's non-file script interface also supports a few other
testing modes; see --help.
Options:
-h, --help show this help message and exit
-c CONFIG_FILE, --config_file=CONFIG_FILE
Configuration file for --refresh and
--obtain_refresh_token_file. The file should contain 4
(or more) settings, one per line, or they can also be
overridden by the equivalent options: client_id=...
client_secret=... refresh_token_file=/path/to/...
access_token_file=/path/to/... Also max_age_sec,
scope, umask, auth_url, token_url, and redirect_uri
have reasonable defaults for google.
--auto_refresh Automatically refresh access_token_file, if older than
max_age_sec from required -c /file/ info.
--refresh Refresh access_token_file unconditionally. Requires
-c /file/ info.
--obtain_refresh_token_file
Update refresh token in file. This is interactive,
and requires a web browser. Also requires -c /file/
info. This also saves an initial access_token_file.
--client_id=CLIENT_ID
Client ID of the application that is authenticating.
See OAuth2 documentation for details.
--client_secret=CLIENT_SECRET
Client secret of the application that is
authenticating. See OAuth2 documentation for details.
--access_token_file=ACCESS_TOKEN_FILE
File name containing OAuth2 access token
--refresh_token_file=REFRESH_TOKEN_FILE
File name containing OAuth2 refresh token
--max_age_sec=MAX_AGE_SEC
default max file age for --auto_refresh. Defaults to
3000 (10 minutes short of normal 3600 sec token
expiration).
--umask=UMASK default umask for --auto_refresh and
--obtain_refresh_token_file. Defaults to 0077.
--scope=SCOPE scope for the access token. Multiple scopes can be
listed separated by spaces with the whole argument
quoted. Defaults to https://mail.google.com/
--auth_url=AUTH_URL Permission URL for --obtain_refresh_token_file.
Defaults to https://accounts.google.com/o/oauth2/auth.
--token_url=TOKEN_URL
Token URL for --obtain_refresh_token_file, and
--refresh. Defaults to
https://accounts.google.com/o/oauth2/token.
--redirect_uri=REDIRECT_URI
Redirect URI for --obtain_refresh_token_file, and
--refresh. Defaults to urn:ietf:wg:oauth:2.0:oob.
--generate_oauth2_token
(OLD/testing) generates an OAuth2 token for testing.
Ignores all files.
--refresh_token=REFRESH_TOKEN
(OLD/testing) Generate a new access token using this
OAuth2 refresh token. Ignores all files.
--user=USER (OLD/testing) email address of user whose account is
being accessed
--imap_server=IMAP_SERVER
(OLD/testing) IMAP server that is being accessed.
Defaults to imap.gmail.com.
--smtp_server=SMTP_SERVER
(OLD/testing) SMTP server that is being accessed.
Defaults to smtp.gmail.com.
--access_token=ACCESS_TOKEN
(OLD/testing) OAuth2 access token.
--generate_oauth2_string
(OLD/testing) generates an initial client response
string for OAuth2. Ignores all files.
--test_imap_authentication
(OLD/testing) attempts to authenticate to IMAP.
Ignores all files.
--test_smtp_authentication
(OLD/testing) attempts to authenticate to SMTP.
Ignores all files.
If you get the help page, then you are good to go.
The Fetchmail source code ships with two templates of the script, for Google and Microsoft.
ls -1 contrib/oauth2-example-*contrib/oauth2-example-google
contrib/oauth2-example-microsoftSo, depending on which mail service platform you are using, copy the respective OAuth2 script and use it as base configuration.
Since we are using Office365 in this guide, let’s copy Microsoft template.
cp contrib/oauth2-example-microsoft /etc/fetchmail/.fetchmail-oauth2cat /etc/fetchmail/.fetchmail-oauth2user=
client_id=
client_secret=
refresh_token_file=/home/{your_username}/.fetchmail-refresh
access_token_file=/home/{your_username}/.fetchmail-token
imap_server=outlook.office365.com
smtp_server=outlook.office365.com
scope=https://outlook.office365.com/IMAP.AccessAsUser.All https://outlook.office365.com/POP.AccessAsUser.All https://outlook.office365.com/SMTP.Send offline_access
auth_url=https://login.microsoftonline.com/{tenant-id}/oauth2/v2.0/authorize
token_url=https://login.microsoftonline.com/{tenant-id}/oauth2/v2.0/token
redirect_uri=http://localhost
Then, update the configuration. Replace YOUR-CLIENT-ID and YOUR-CLIENT-SECRET with the keys for your “Client ID” and “Client Secret” from the previous step. For Microsoft: replace YOUR-TENANT-ID in the auth_url and token_url hostnames with the tenant_id from the previous step.
Here is my updated config;
cat /etc/fetchmail/.fetchmail-oauth2user=
client_id=7fe502a6-xxxx-xxxx-xxxx-xxxxxxxxxxxx
client_secret=d9R8Q~Fh3OPhKN7QM5V-XXXMfSb1H0LdVs23Ialy
refresh_token_file=/etc/fetchmail/.fetchmail-refresh
access_token_file=/etc/fetchmail/.fetchmail-token
imap_server=outlook.office365.com
smtp_server=outlook.office365.com
scope=https://outlook.office365.com/IMAP.AccessAsUser.All https://outlook.office365.com/POP.AccessAsUser.All https://outlook.office365.com/SMTP.Send offline_access
auth_url=https://login.microsoftonline.com/988dda4d-xxxx-xxxx-xxxx-xxxxxxxxxxxx/oauth2/v2.0/authorize
token_url=https://login.microsoftonline.com/988dda4d-xxxx-xxxx-xxxx-xxxxxxxxxxxx/oauth2/v2.0/token
redirect_uri=http://localhost
Note that the refresh and token files do not need to exist, but they have to be valid paths.
If you have multiple Email accounts representing different RT queues, and you want to fetch mails from those accounts into their respective RT queues, then duplicate the configuration above, /etc/fetchmail/.fetchmail-oauth2, for each of the email accounts and update the paths to the refresh and token files to reflect the specific email account/queue.
Next, run the script to update the refresh and token files.
/etc/fetchmail/fetchmail-oauth2.py -c /etc/fetchmail/.fetchmail-oauth2 --obtain_refresh_token_fileWhen the script is ran, it will provide a URL:
To authorize token, visit this url and follow the directions:
https://login.microsoftonline.com/988dda4d-xxxx-xxxx-xxxx-xxxxxxxxxxxx/oauth2/v2.0/authorize?client_id=7fe502a6-6934-4f26-b24d-abe3358a6ba6&redirect_uri=http%3A%2F%2Flocalhost&response_type=code&scope=https%3A%2F%2Foutlook.office365.com%2FIMAP.AccessAsUser.All%20https%3A%2F%2Foutlook.office365.com%2FPOP.AccessAsUser.All%20https%3A%2F%2Foutlook.office365.com%2FSMTP.Send%20offline_access
Enter verification code:
- Copy and paste the URL into a web browser.
- The URL opens an authentication page.
- Select the email account that you want Fetchmail to fetch messages from.
- If using Gmail, Google may warn that the app isn’t verified.
- Click “Continue”.
- Confirm permission to read your email and Click “Allow.”
- The page will display the sign-in key, or you can find it in the URL as the value to the “code” variable.
Sample URL after accessing on the link above on browser:
http://localhost/?code=1.AU8ATdqNmPNSykmEKsRM7DkbVqYC5X80aSZPsk2r4zWKa6Y5AQBPAA.AgABBAIAAABVrSpeuWamRam2jAF1XRQEAwDs_wUA9P80dRu3Slu0aR6DsiouNAGrdFENU5pAEfLOv_9qDcqhr2mhreDWFJJPBGz1OaYLlaXEZ6hkcX75FxrdQsRrKQgquNkMeQhylmuplcNVaNtfPpJl1zmfUcfxqSvk0p6QT1vuiOMNVhmxwvgopPbvwPu0M1zA6w24tsbBVSkzS_6pbrHo2DPh103hg1ZQcTjN78rM7m4Qq4AU8_hy0NnrViAZLGCrx0r0M2XD2ikUNDpwtdS2dcahB0nMYp6wHAWDxTy89AxMCKMl7gRl9GgWZstGLUoNCfWnLL-LWaQXEWME4NFm-3P23H7buDwEFvVIQWXPh_vxlkpQQZNiKMIlZRZLR4XVjWL4FZq_UAX0YbRP9PYH2Q6Yu9LaNVEmaEqrOigEcIBeOv3xpZJ5J2Ewt5p-h01G3zhZfvByHOxJZoAiqddcT1EGB5RlsoUUpfwWWaIjGO8X4wZMAixWmX2RkboKWklImyori3TyxPcDxpYn8dTzMNZf2m5IGG9cja4METzeapVX1MeVPerjMWZ_qaSwlMHiMFGxwflVe74VwcNPcNv97Z-kb_rXK3rN0ZmhDg8pfcKFZfNRXAlvKgxNqs_5INgnI9xscztaBKVoZMxQwY1j_mow3QKC1Z_J5E_9wihQhEuaI8DMK4TwHe2Hu4oTXOeOB11bpfzs8KtfgnN5fT7gpC_O0cgQDiBGfU26Zk2l_3RsfoYCKxuvKmv1rX96Ao1A8ac74kWTCBBU2TQ2WEEWHkn1aRxLaORbt7H1WH1exZSifMs9ub2VIZ7wQDg3v-ffwh2X64DYBX2s1wrP2wD3FQ&session_state=00308dc9-aeb6-d9cf-bebd-ed2721b67ec6#Copy the code and paste onto the Enter verification code: prompt from the script executed above.
The script will the report:
Refresh token saved to '/etc/fetchmail/.fetchmail-refresh'
Initial access token saved to '/etc/fetchmail/.fetchmail-token'
Access Token Expiration Seconds: 4104
Like as mentioned above, if you have multiple email accounts, you can generate refresh tokens for each, by using their respective configuration files.
Update the permissions on Fetchmail OAuth2 configuration and refresh/token files.
chmod 0600 /etc/fetchmail/{.fetchmail-refresh,.fetchmail-token,.fetchmail-oauth2}Install a cron job to take care of token refresh. Since we have updated the config to refresh the token hourly; we can install a cron job that takes care of refreshing them in every 2 mins;
crontab -e*/2 * * * * (sudo -u fetchmail /etc/fetchmail/fetchmail-oauth2.py -c /etc/fetchmail/.fetchmail-oauth2 --auto_refresh;sudo -u fetchmail fetchmail) >> /var/log/fetchmail.log 2>&1Add similar job for other email accounts token refresh.
Save and exit to crontab.
Ensure the Fetchmail log file is rotated;
sed -i '/{/i /var/log/fetchmail.log' /etc/logrotate.d/rsyslogConfigure Fetchmail to Deliver Mails to Respective RT Queues
Depending on your mail service provider, you need to configure RT to fetch mails from the ticketing mail INBOX and deliver it to the respective RT queues.
Therefore, create Fetchmail configuration under the /etc/fetchmail. In this guide, we have created the config as /etc/fetchmail/.fetchmailrc with the content below:
cat /etc/fetchmail/.fetchmailrcset daemon 60
set postmaster "kifarunix"
set no syslog
set logfile "/var/log/fetchmail.log"
poll outlook.office365.com protocol IMAP port 993
auth oauthbearer username "[email protected]"
passwordfile "/etc/fetchmail/.fetchmail-token"
folders INBOX
no fetchall
no rewrite
limit 0
keep
tlsmode wrapped sslcertck
mda "/opt/rt5/bin/rt-mailgate --url https://rt.kifarunix.com --no-verify-ssl --queue General --action correspond --debug"Where:
- set daemon 60: This sets fetchmail to run as a daemon, polling the mail server every 60 seconds (1 minute) to check for new emails.
- set postmaster “kifarunix”: This sets the postmaster’s email address to “kifarunix”. Error messages and system notifications will be sent to this address ([email protected]).
- set no syslog: This disables logging to syslog, so fetchmail will log to the file specified instead of the system log.
- set logfile “/var/log/fetchmail.log”: This sets the log file to
/var/log/fetchmail.log, where fetchmail logs its operations. Note that the logfile must exist before fetchmail is run, you can use the touch command with the filename as its sole argument to create it. - poll outlook.office365.com protocol IMAP port 993: This tells fetchmail to poll the IMAP server of
outlook.office365.comon port 993 for secure communication. - auth oauthbearer username “[email protected]”: This specifies that OAuth2 authentication will be used, with the username being
"[email protected]". - passwordfile “/etc/fetchmail/.fetchmail-token”: This specifies the file that contains the OAuth2 access token to authenticate the user.
- folders INBOX: This tells fetchmail to only poll the INBOX folder for new emails, ignoring other folders.
- no fetchall: This tells fetchmail to only fetch new emails, ignoring previously retrieved ones.
- no rewrite: This disables the rewrite feature, meaning fetchmail will not alter the
Fromheader of emails. - keep: This keeps the emails on the server after they are fetched, rather than deleting them.
- ssl: This enables SSL/TLS encryption for the connection to the mail server.
- mda “/etc/fetchmail/bin/rt-mailgate –url https://rt.kifarunix.com –no-verify-ssl –queue General –action correspond –debug”: This specifies the Mail Delivery Agent (MDA) to handle the fetched emails, sending them to the Request Tracker (RT) system with debug output enabled.
Read more on the documentation page.
Again, if you have multiple Queues with different ticketing email accounts as mentioned before, you have to duplicate the poll configuration section for each respective email account representing a specific RT queue.
For example, to add another configuration for the second mail, the general configuration would look like;
set daemon 60
set postmaster "kifarunix"
set no syslog
set logfile "/var/log/fetchmail.log"
poll outlook.office365.com protocol IMAP port 993
auth oauthbearer username "[email protected]"
passwordfile "/etc/fetchmail/.fetchmail-token"
folders INBOX
no fetchall
no rewrite
limit 0
keep
tlsmode wrapped sslcertck
mda "/opt/rt5/bin/rt-mailgate --url https://rt.kifarunix.com --no-verify-ssl --queue General --action correspond --debug"
# Second mailbox
poll outlook.office365.com protocol IMAP port 993
auth oauthbearer username "helpdesk@domain"
passwordfile "/etc/fetchmail/.fetchmail-token-helpdesk"
folders INBOX
no fetchall
no rewrite
limit 0
keep
tlsmode wrapped sslcertck
mda "/opt/rt5/bin/rt-mailgate --url https://rt.kifarunix.com --no-verify-ssl --queue Helpdesk --action correspond --debug"Update the permissions of the file:
chmod 0700 /etc/fetchmail/.fetchmailrcRun Fetchmail against the configuration file to see if it can fetch mails from your tickets inbox;
fetchmail -f /etc/fetchmail/.fetchmailrc -l 5 -NSample output;
Mar 18 13:56:25 fetchmail: WARNING: Running as root is discouraged.
The nodetach option is in effect, ignoring logfile option.
Mar 18 13:56:25 fetchmail: 3 messages (3 seen) for [email protected] at outlook.office365.com (folder INBOX).That confirms the Fetchmail is able to see messages on the mailbox.
Update the ownership of the Fetchmail configurations:
chown -R fetchmail: /etc/fetchmailCreate the Fetchmail Log file:
touch /var/log/fetchmail.logchown fetchmail: /var/log/fetchmail.logCreate Systemd Service Unit for Fetchmail
As you can see above, WARNING: Running as root is discouraged. Now, let’s create a systemd service unit. Below is the contents of our Fechmail service unit, /etc/systemd/system/fetchmail.service.
cat /etc/systemd/system/fetchmail.service[Unit]
Description=Fetchmail Daemon
Documentation=man:fetchmail(1)
[Service]
User=fetchmail
Group=fetchmail
ExecStart=fetchmail -f /etc/fetchmail/.fetchmailrc
ExecStop=fetchmail --quit
Restart=on-failure
[Install]
WantedBy=default.targetReload Systemd and start the service.
systemctl daemon-reload systemctl enable --now fetchmailCheck status of the service;
systemctl status fetchmail.service* fetchmail.service - Fetchmail Daemon
Loaded: loaded (/etc/systemd/system/fetchmail.service; enabled; preset: enabled)
Active: active (running) since Tue 2025-03-18 17:10:41 UTC; 12s ago
Docs: man:fetchmail(1)
Main PID: 40518 (fetchmail)
Tasks: 1 (limit: 4656)
Memory: 2.0M (peak: 2.3M)
CPU: 44ms
CGroup: /system.slice/fetchmail.service
`-40518 fetchmail -f /etc/fetchmail/.fetchmailrc
Mar 18 17:10:41 rt.kifarunix.com systemd[1]: Started fetchmail.service - Fetchmail Daemon.
You can monitor the logs;
tail -f /var/log/fetchmail.logVerify Request Tracker Tickets Delivery to the Queues
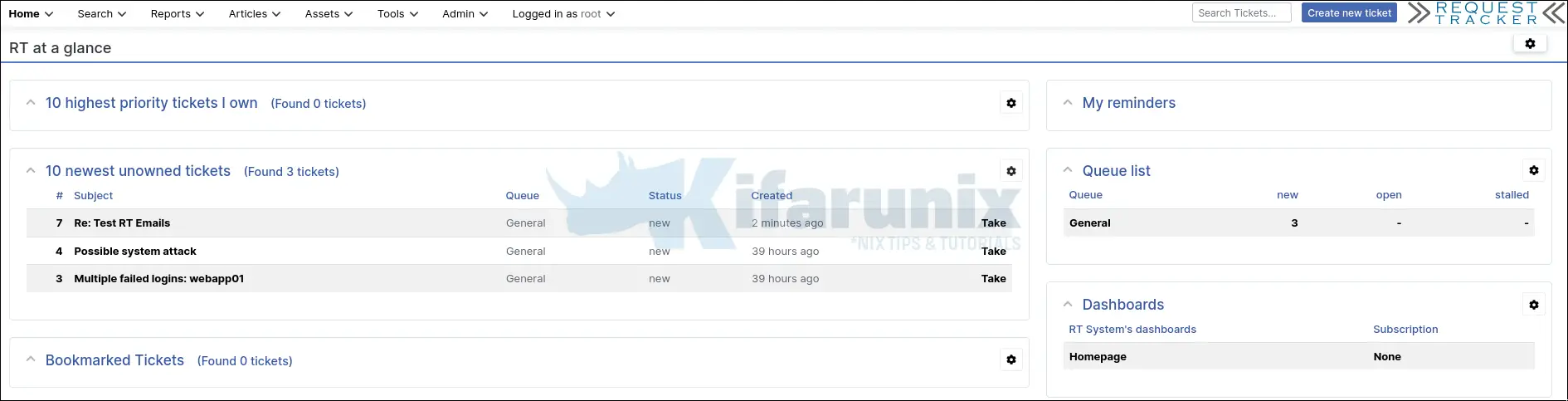
Now, try to send a test mail to the respective ticketing mail and confirm that the ticket is delivered to the respective queue.
See my test ticket on general queue sent 2 minutes ago.
Sample Fetchmail logs;
tail -f /var/log/fetchmail.logMar 20 12:18:02 fetchmail: 8 messages (7 seen) for email@domain at outlook.office365.com (folder INBOX).
/opt/rt5/bin/rt-mailgate: temp file is '/tmp/_B55_Vaqyg/GYE4XIVLv7'
/opt/rt5/bin/rt-mailgate: connecting to http://rt.kifarunix.com/REST/1.0/NoAuth/mail-gateway
ok
Mar 20 12:18:02 fetchmail: reading message email@[email protected]:8 of 8 (10018 header octets) (958 body octets) not flushed
Mar 20 12:19:03 fetchmail: 8 messages (8 seen) for email@domain at outlook.office365.com (folder INBOX).
Mar 20 12:20:01 fetchmail: awakened by User defined signal 1
fetchmail: background fetchmail at 42144 awakened.
Mar 20 12:20:02 fetchmail: 8 messages (8 seen) for email@domain at outlook.office365.com (folder INBOX).
That confirms that the Request Tracker is able to read ticket mails from the mail box and deliver them the respective queues.
Configure Request Tracker to Send Ticket updates to Recipients
You can check the guide below on how to configure RT to send ticket updates to respective recipients.
Configure Request Tracker (RT) to send Mails using MSMTP via Office 365 Relay
Conclusion
The Fetchmail is now installed and configured to use OAuth2 to connect to secured mailbox, read new ticker mails and deliver them to respective queues. That marks the close of our guide.

