In this blog post, you’ll learn how to automate RHEL OS upgrades using Ansible infra.leapp playbooks, simplifying the upgrade process for Red Hat Enterprise Linux systems with minimal effort. We will see how to upgrade RHEL 7 to 8, RHEL 8 to 9 and RHEL 9 to 10 using infra.leapp playbooks. The Red Hat Community of Practice (CoP) offers community-driven infra.leapp Ansible collection, which provides a solid foundation for Leapp-based upgrades, which is the Red Hat’s recommended solution for in-place OS upgrades. By leveraging these playbooks, you can automate and streamline the upgrade workflow, ensuring consistency, reducing errors, and speeding up the process across your infrastructure.
Table of Contents
Automate RHEL OS Upgrades using Ansible infra.leapp Playbooks
Why Automation Matters for Enterprise RHEL Upgrades
Traditional in-place upgrades involve dozens of manual checks: verifying subscriptions, ensuring repositories are available, cleaning up obsolete packages, running Leapp manually, and handling reboots. Doing this across tens or hundreds of servers is not only tedious but also introduces risk.
By automating this process using Ansible with the infra.leapp collection, you are able to:
- Standardize the upgrade workflow.
- Eliminate human error by codifying each step.
- Integrate Satellite, activation keys, and repo management.
- Scale to fleets of servers with Ansible Automation Platform (AAP), AWX or even vanilla Ansible CLI.
As such, enterprise organizations require a systematic approach to manage the complexities of RHEL OS upgrades, including tasks like system pre-upgrade preparation, package management, dependency resolution, and upgrade orchestration. This approach should also ensure comprehensive logging and error handling, helping to maintain consistency and minimize risks throughout the upgrade process, whether using Red Hat Satellite, direct Red Hat CDN, or other subscription management solutions.
This is where the Red Hat CoP infra.leapp Ansible collections come in, offering a robust and automated solution for managing the upgrade process.
In our previous guides, we provided step by step guides on how to upgrade RHEL 8 to 9 and RHEL 9 to 10:
Upgrade RHEL 8 to RHEL 9 using LEAPP with Satellite Server Integration
Upgrade RHEL 9 to RHEL 10 using LEAPP Tool
Understanding the infra.leapp Ansible Collection
The infra.leapp Ansible Collection is a set of roles and playbooks designed to automate RHEL in-place upgrades using the Leapp framework or RUT (Red Hat Upgrade Tool), developed as part of Red Hat’s Cloud Operating Platform (CoP). Aimed at large-scale environments, the collection simplifies complex upgrade processes, ensuring they are repeatable and consistent across your RHEL estate.
It supports multiple upgrade paths:
- RHEL 6 to RHEL 7: Utilizing RUT.
- RHEL 7 to RHEL 8: Leveraging the Leapp framework for in-place upgrades.
- RHEL 8 to RHEL 9: Also leverages Leapp.
- RHEL 9 to RHEL 10: This also utilizes Leapp framework.
The collection includes five essential roles:
- analysis: Executes the Leapp pre-upgrade phase analysis
- common: Handles system log files to aid in debugging playbooks, such as analysis and upgrade. It also includes a mutex locking mechanism to prevent running multiple playbook jobs on the same host simultaneously. Additionally, it defines common variables that are shared between the analysis and upgrade roles.
- parse_leapp_report: used by the analysis or upgrade roles to check the Leapp pre-upgrade report for inhibitors.
- upgrade: Performs the actual OS upgrade
- remediate: Assists in the remediation of systems by addressing inhibitors discovered during the pre-upgrade analysis.
The collection also provides four default playbooks to orchestrate the upgrade process:
- analysis.yml: Runs the Leapp pre-upgrade scan to generate reports of inhibitors and potential issues.
- remediate.yml: Applies remediation steps based on the Leapp analysis results.
- upgrade.yml: Executes the actual OS upgrade using Leapp, handling reboots, migrations, and logging.
- rolling_upgrade_ha_cluster.yml: Targets high-availability clusters, enabling rolling upgrades without full downtime.
While these roles provide excellent foundational capabilities, enterprise deployments require customization to address specific infrastructure requirements, satellite integration, and organizational policies.
Install and Customize the infra.leapp Ansible Collection
While the infra.leapp collection from the Red Hat Community of Practice (CoP) provides excellent foundational capabilities, enterprise deployments almost always require customization to address specific infrastructure requirements, Satellite integration details, and organizational policies.
This guide presents two methods for managing the collection:
- Option 1 (Simple): Install, Create a Copy and Customize – Best for quick tests or minimal changes.
- Option 2 (Recommended for Enterprise): Fork and Manage – The professional standard for long-term, scalable, and maintainable automation.
Option 1: Install, Create a Copy and Customize the Collection
To install the collection, you can use the ansible-galaxy command-line tool.
- For system-wide installations of Ansible, simply execute the command directly in your terminal:
ansible-galaxy collection install redhat-cop.infra.leapp - If you’re using a virtual environment (which is recommended for managing dependencies in isolated environments), first ensure that your virtual environment is activated. You can activate it by running:
Once the virtual environment is active, run the following command to install the collection:source /path/to/your/venv/bin/activateansible-galaxy collection install redhat-cop.infra.leapp
This way, you can ensure that you’re installing the collection in the appropriate context based on whether you’re working in a virtual environment or using a system-wide installation of Ansible.
The infra.leapp collection has dependencies on several other collections, which need to be installed before using it. These required collections include:
- ansible.posix
- community.general
- fedora.linux_system_roles (or redhat.rhel_system_roles for Red Hat-based systems)
To check if these collections are already installed, you can list your installed collections using the following command:
- For system-wide installations, you can run the command directly.
- For virtual environments, ensure that your virtual environment is activated first, as shown earlier, to access the
ansible-galaxycommand.
ansible-galaxy collection list | grep -iE "posix|general|linux_system_roles"This will show you whether the necessary collections are already present in your environment.
Sample command output;
fedora.linux_system_roles 1.108.6
ansible.posix 1.5.4
community.general 8.1.0
If any collections are missing, install them using these commands:
ansible-galaxy collection install ansible.posixansible-galaxy collection install community.generalansible-galaxy collection install fedora.linux_system_rolesCopy and Customize the infra.leapp Ansible Collection
Now that you have installed the collection, you can copy them to your custom directory and customize them to suite your needs. Copying the collection into your custom directory works best when you want to do one-off tests or proof-of-concept projects or if you are certain you will not need to incorporate future updates from the original collection.
To achieve this:
- Create a dedicated directory for example, /home/kifarunix/ansible-env/infra.leapp on your Ansible server. Replace the paths accordingly.
mkdir ~/ansible-env/infra.leapp - Copy the default collection into the custom directory created above:
You can remove some other files you deem unnecessary such as README files and the likes.rsync -avP ~/.ansible/collections/ansible_collections/infra/leapp/ ~/ansible-env/infra.leapp/ - Reconfigure the collection in the custom directory to avoid referencing the default system collection (by removing infra.leapp from the fully qualified collection names (FQCN) of the collection roles). For example, consider the analysis.yml playbook, we renamed it from:
to---
- name: Analysis
hosts: all
strategy: free
gather_facts: true
become: true
force_handlers: true
...
...
tasks:
- name: Generate preupgrade analysis report
ansible.builtin.import_role:
name: infra.leapp.analysis
You can do this recursively using the command below:---
- name: Analysis
hosts: all
strategy: free
gather_facts: true
become: true
force_handlers: true
...
...
tasks:
- name: Generate preupgrade analysis report
ansible.builtin.import_role:
name: analysisgrep -irl infra.leapp | xargs -I {} sed -i 's/infra.leapp.//g' {}
- Create an
ansible.cfgfile in the custom directory to specify the path to your custominfra.leapproles directory, ensuring that Ansible uses your customized roles instead of the default ones when running againstinfra.leappplaybooks. This is how we have defined the path to the custom roles in the Ansible config file.cat ansible.cfg
[defaults] roles_path = /home/kifarunix/ansible-env/infra.leapp/role
- By default, the remediation main task is configured to support RHEL 7 and 8 only. Let’s customize it to support RHEL 9.
This is how it looks by default:cat ~/ansible-env/infra.leapp/roles/remediate/tasks/main.yml
This is how we have updated it to add support for RHEL 9:---
# tasks file for remediations
- name: Check if the system is RHEL 7 or 8
ansible.builtin.assert:
that: ansible_distribution == 'RedHat' and ( ansible_distribution_major_version|int == 8 or ansible_distribution_major_version|int == 7 )
msg: "This role is only applicable to RHEL 7 or 8"
tags: remediate
...---
# tasks file for remediations
- name: Check if the system is RHEL 7, 8 or 9
ansible.builtin.assert:
that: ansible_distribution == 'RedHat' and ( ansible_distribution_major_version|int == 8 or ansible_distribution_major_version|int == 7 or ansible_distribution_major_version|int == 9 )
msg: "This role is only applicable to RHEL 7, 8 or 9"
tags: remediate
... - We also customized the remediation task (
~/ansible-env/infra.leapp/roles/remediate/tasks/leapp_remote_using_root.yml) to address inhibitors related to SSH root login and password-based authentication. By default, this task disables both SSH root login (PermitRootLogin) and password-based authentication (PasswordAuthentication). However, since we rely on password-based authentication, we modified the task to only disable SSH root login while keeping password-based authentication enabled. Specifically, we changed the task from:
To this (commented the PasswordAuthentication line):...
loop:
- {key: "PermitRootLogin", value: "prohibit-password"}
- {key: "PasswordAuthentication", value: "no"}
notify:
- Restart sshd...
loop:
- {key: "PermitRootLogin", value: "prohibit-password"}
# - {key: "PasswordAuthentication", value: "no"}
notify:
- Restart sshd - We have also updated the remediation playbook, ~/ansible-env/infra.leapp/playbooks/remediate.yml, to handle additional common inhibitors encountered during the upgrade process. Specifically, we have added more remediation tasks that are available under the
roles/remediate/tasks/directory to address a broader range of issues.
Before:
After:--- - name: Remediate hosts: all strategy: free become: true force_handlers: true vars: remediation_todo: - leapp_firewalld_allowzonedrifting - leapp_missing_pkg tasks: - name: Perform remediations on the system ansible.builtin.import_role: name: remediate ...--- - name: Remediate hosts: all strategy: free become: true force_handlers: true vars: remediation_todo: - leapp_firewalld_allowzonedrifting - leapp_missing_pkg - leapp_vdo_check_needed - leapp_remote_using_root - leapp_nfs_detected - leapp_vdo_check_needed - leapp_partitions_with_noexec - leapp_rpms_with_rsa_sha1_detected - leapp_custom_network_scripts_detected tasks: - name: Perform remediations on the system ansible.builtin.import_role: name: remediate ... - This modification adds tasks to address additional inhibitors, including checks for VDO configuration, NFS filesystems detection, partitions with noexec, and RPMs with outdated RSA SHA-1 signatures. These tasks addresses the most common inhibitors/errors encountered during the RHEL OS upgrades ensuring that the system is fully prepared for a successful Leapp upgrade.
Introducing a Playbook to Resolve the Unsupported Network Configuration Inhibitor
During the pre-upgrade analysis for one of our RHEL 7 servers (targeting RHEL 8), we encountered a Leapp inhibitor related to unsupported network interface naming:
RUNNING HANDLER [infra.leapp.analysis : Display inhibitors] ********************
ok: [192.168.112.113] => {
"results_inhibitors.stdout_lines": [
"Risk Factor: high (inhibitor)",
"Title: Unsupported network configuration",
"Summary: Detected multiple physical network interfaces where one or more use kernel naming (e.g. eth0). Upgrade process can not continue because stability of names can not be guaranteed. Please read the article at https://access.redhat.com/solutions/4067471 for more information.",
"Related links:",
" - How to perform an in-place upgrade to RHEL 8 when using kernel NIC names on RHEL 7: https://access.redhat.com/solutions/4067471",
" - RHEL 8 to RHEL 9: inplace upgrade fails at \\"Network configuration for unsupported device types detected\\": https://access.redhat.com/solutions/7009239",
"Remediation: [hint] Rename all ethX network interfaces following the attached KB solution article.",
"Key: d3050d265759a79ce895e64f45e9c56e49b3a953",
"----------------------------------------"
]
}
This issue occurs when interfaces use kernel-based names like eth0, eth1, which are not persistent or predictable across RHEL upgrades. Red Hat recommends using predictable network interface names such as ens*, enp*, ensetc.
While the infra.leapp Ansible collection provides automation for many common inhibitors, it seems like it does not currently include remediation for this specific network configuration issue.
Fortunately, Red Hat provides an official Ansible playbook to assist with renaming interfaces in line with predictable naming conventions. This playbook is referenced in Red Hat Solution 4067471, and the source can be downloaded directly from here.
We downloaded and slightly modified the official playbook to fit our environment. Our modified playbook addresses eth0 and eth1, ensuring they are renamed to persistent names based on system BIOS or PCI slot information.
We saved the modified playbook under roles/remediate/tasks/leapp_unsupported_network_configuration.yml:
Here are the contents:
cat roles/remediate/tasks/leapp_unsupported_network_configuration.yml---
- name: leapp_unsupported_network_configuration | Rename kernel named interfaces to predictable names
vars:
src_prefix: "eth"
dst_prefix: "em"
osnet_conf: "/etc/os-net-config/config.json"
src_interfaces: "{{ ansible_interfaces | select('match', src_prefix ~ '.*') | sort | list }}"
undercloud_conf: "~/undercloud.conf"
block:
- name: leapp_unsupported_network_configuration | Debug interfaces to rename
ansible.builtin.debug:
msg: "{{ src_interfaces }}"
- name: leapp_unsupported_network_configuration | Update udev rules
ansible.builtin.lineinfile:
line: >
SUBSYSTEM=="net",
ACTION=="add",
DRIVERS=="?*",
ATTR{address}=="{{ ansible_facts[item]['perm_macaddress'] | default(ansible_facts[item]['macaddress']) }}",
NAME="{{ item | replace(src_prefix, dst_prefix) }}"
path: /etc/udev/rules.d/70-rhosp-persistent-net.rules
create: true
loop: "{{ src_interfaces | reject('match', '^.*\\..*$') | list }}"
- name: leapp_unsupported_network_configuration | Check that src_prefix files exists
ansible.builtin.stat:
path: /etc/sysconfig/network-scripts/ifcfg-{{ item }}
register: nic_result
loop: "{{ src_interfaces }}"
- name: leapp_unsupported_network_configuration | Copy ifcfg files using dst_prefix
ansible.builtin.copy:
remote_src: true
src: "{{ item.stat.path }}"
dest: "{{ item.stat.path | replace(src_prefix, dst_prefix) }}"
loop: "{{ nic_result.results }}"
when: item.stat.exists
loop_control:
label: "{{ item.item }}"
- name: leapp_unsupported_network_configuration | Edit NAME in new network-script files
ansible.builtin.lineinfile:
regexp: "^NAME=.*"
line: "NAME={{ item.item | replace(src_prefix, dst_prefix) }}"
path: "{{ item.stat.path | replace(src_prefix, dst_prefix) }}"
loop: "{{ nic_result.results }}"
when: item.stat.exists
loop_control:
label: "{{ item.item }}"
- name: leapp_unsupported_network_configuration | Edit DEVICE in new network-script files
ansible.builtin.lineinfile:
regexp: "^DEVICE=.*"
line: "DEVICE={{ item.item | replace(src_prefix, dst_prefix) }}"
path: "{{ item.stat.path | replace(src_prefix, dst_prefix) }}"
loop: "{{ nic_result.results }}"
when: item.stat.exists
loop_control:
label: "{{ item.item }}"
- name: leapp_unsupported_network_configuration | Backup old ifcfg network-script files
ansible.builtin.copy:
remote_src: true
src: "{{ item.stat.path }}"
dest: "{{ item.stat.path }}.bak"
loop: "{{ nic_result.results }}"
when: item.stat.exists
loop_control:
label: "{{ item.item }}"
- name: leapp_unsupported_network_configuration | Remove old ifcfg network-script files
ansible.builtin.file:
path: "{{ item.stat.path }}"
state: absent
loop: "{{ nic_result.results }}"
when: item.stat.exists
loop_control:
label: "{{ item.item }}"
- name: leapp_unsupported_network_configuration | Check that route files exists
ansible.builtin.stat:
path: /etc/sysconfig/network-scripts/route-{{ item }}
register: route_result
loop: "{{ src_interfaces }}"
- name: leapp_unsupported_network_configuration | Copy route files using dst_prefix
ansible.builtin.copy:
remote_src: true
src: "{{ item.stat.path }}"
dest: "{{ item.stat.path | replace(src_prefix, dst_prefix) }}"
loop: "{{ route_result.results }}"
when: item.stat.exists
loop_control:
label: "{{ item.item }}"
- name: leapp_unsupported_network_configuration | Update dst_prefix in route files that use IP command arguments format
ansible.builtin.replace:
regexp: "{{ src_prefix }}"
replace: "{{ dst_prefix }}"
path: "{{ item.stat.path | replace(src_prefix, dst_prefix) }}"
loop: "{{ route_result.results }}"
when: item.stat.exists
loop_control:
label: "{{ item.item }}"
- name: leapp_unsupported_network_configuration | Backup old route files
ansible.builtin.copy:
remote_src: true
src: "{{ item.stat.path }}"
dest: "{{ item.stat.path }}.bak"
loop: "{{ route_result.results }}"
when: item.stat.exists
loop_control:
label: "{{ item.item }}"
- name: leapp_unsupported_network_configuration | Remove old route files
ansible.builtin.file:
path: "{{ item.stat.path }}"
state: absent
loop: "{{ route_result.results }}"
when: item.stat.exists
loop_control:
label: "{{ item.item }}"
- name: leapp_unsupported_network_configuration | Get a list of all ifcfg files
ansible.builtin.find:
paths: /etc/sysconfig/network-scripts/
patterns: 'ifcfg-*'
excludes: '*.bak'
register: ifcfg_files
- name: leapp_unsupported_network_configuration | Perform final regex on ifcfg files
ansible.builtin.replace:
path: "{{ item[0].path }}"
regexp: "{{ item[1] }}"
replace: "{{ item[1] | replace(src_prefix, dst_prefix) }}"
with_nested:
- "{{ ifcfg_files.files }}"
- "{{ src_interfaces }}"
loop_control:
label: "{{ item[1] }} -> {{ item[0].path }}"
- name: leapp_unsupported_network_configuration | Check if undercloud.conf exists
ansible.builtin.stat:
path: "{{ undercloud_conf }}"
register: undercloud_conf_stat
- name: leapp_unsupported_network_configuration | Replace interface name in undercloud.conf
ansible.builtin.replace:
path: "{{ undercloud_conf }}"
regexp: "{{ item }}"
replace: "{{ item | replace(src_prefix, dst_prefix) }}"
when: undercloud_conf_stat.stat.exists
loop: "{{ src_interfaces }}"
- name: leapp_unsupported_network_configuration | Check if os-net-config's config.json exists
ansible.builtin.stat:
path: "{{ osnet_conf }}"
register: osnet_conf_stat
- name: leapp_unsupported_network_configuration | Replace interface name in config.json
ansible.builtin.replace:
path: "{{ osnet_conf }}"
regexp: "{{ item }}"
replace: "{{ item | replace(src_prefix, dst_prefix) }}"
when: osnet_conf_stat.stat.exists
loop: "{{ src_interfaces }}"
- name: leapp_unsupported_network_configuration | Reboot system to apply network interface changes
ansible.builtin.reboot:
reboot_timeout: "{{ reboot_timeout }}"
post_reboot_delay: "{{ post_reboot_delay }}"
timeout: "{{ reboot_timeout }}"
when: src_interfaces | length > 0
...
To integrate this task into the existing remediation workflow:
- Add the playbook name to
roles/remediate/defaults/main.yml:--- # defaults file for remedations reboot_timeout: 7200 post_reboot_delay: 120 leapp_report_location: /var/log/leapp/leapp-report.json remediation_playbooks: - leapp_cifs_detected - leapp_corrupted_grubenv_file - leapp_custom_network_scripts_detected - leapp_deprecated_sshd_directive - leapp_firewalld_allowzonedrifting - leapp_firewalld_unsupported_tftp_client - leapp_loaded_removed_kernel_drivers - leapp_missing_efibootmgr - leapp_missing_pkg - leapp_missing_yum_plugins - leapp_multiple_kernels - leapp_newest_kernel_not_in_use - leapp_nfs_detected - leapp_non_persistent_partitions - leapp_non_standard_openssl_config - leapp_old_postgresql_data - leapp_pam_tally2 - leapp_partitions_with_noexec - leapp_relative_symlinks - leapp_remote_using_root - leapp_rpms_with_rsa_sha1_detected - leapp_unavailable_kde - leapp_vdo_check_needed - leapp_unsupported_network_configuration remediation_todo: [] ...
- Include the playbook in the main remediation playbook (
playbooks/remediate.yml):--- - name: Remediate hosts: all strategy: free become: true force_handlers: true vars: remediation_todo: - leapp_firewalld_allowzonedrifting - leapp_missing_pkg - leapp_vdo_check_needed - leapp_remote_using_root - leapp_nfs_detected - leapp_vdo_check_needed - leapp_partitions_with_noexec - leapp_rpms_with_rsa_sha1_detected - leapp_custom_network_scripts_detected - leapp_unsupported_network_configuration tasks: - name: Perform remediations on the system ansible.builtin.import_role: name: remediate ...
This ensures that any system encountering this inhibitor will automatically have the necessary network configuration corrected prior to attempting the OS upgrade.
Create Hosts Inventory
We have created a directory containing hosts inventory file:
tree inventory/inventory
└── rhel
1 directory, 1 fileThe inventory file looks like:
cat inventory/rhel[rhel7]
192.168.122.113
[rhel8]
192.168.122.114
[rhel9]
192.168.122.115
[all:children]
rhel7
rhel8
rhel9
[all:vars]
ansible_user=USERNAME
ansible_password=ChangeME
ansible_become=true
ansible_become_method=sudo
ansible_become_password=ChangeMEChange the values of the user and password accordingly.
If you are using AAP or AWX, there is no need to define the credentials on the inventory file. You can easily set them on the application itself.
Create Centralized Variables File
To improve scalability and manageability, you can create a centralized variables file that holds configuration details for your environment. We have created a group_vars directory under the hosts inventory directory containing all variables that we require in our upgrade activity. We will specifically update the analysis and upgrade playbooks to use some of the variables defined below.
The group variables in my environment:
cat inventory/group_vars/all.yml---
satellite_hostname: satellite.kifarunix.com
satellite_url: "http://{{ satellite_hostname }}"
satellite_katello_rpm: "{{ satellite_url }}/pub/katello-ca-consumer-latest.noarch.rpm"
satellite_organization: Kifarunix
selinux_mode: permissive
update_grub_to_grub_2: true
leapp_answerfile: |
[remove_pam_pkcs11_module_check]
confirm = True
os_config:
"7":
satellite_activation_key: rhel7_uat
satellite_activation_key_leapp: rhel7_uat_leapp
satellite_activation_key_post_leapp: rhel8_uat
"8":
satellite_activation_key: rhel8_uat
satellite_activation_key_leapp: rhel8_uat_leapp
satellite_activation_key_post_leapp: rhel9_uat
"9":
satellite_activation_key: rhel9_uat
satellite_activation_key_leapp: rhel9_uat_leapp
satellite_activation_key_post_leapp: rhel10_uatHere is the summary of the configs used above:
- General Satellite Configuration:
satellite_hostname: The hostname for the Satellite server.satellite_url: Dynamically created URL for the Satellite server.satellite_katello_rpm: URL to download the Katello Consumer RPMsatellite_organization: The Satellite organization name.
- General Leapp Configuration:
selinux_mode: Configures SELinux mode. Setting it to “permissive” mode.update_grub_to_grub_2: This is for the 7 to 8 upgrade path. It forces the system to update the GRUB bootloader to GRUB2, which is required for RHEL 8 and later versions.
- Answerfile for issues that don’t have a remediation or just need confirmation: Used in the Leapp upgrade process to automatically confirm that certain checks (like removing the
pam_pkcs11_module_check) should be performed. - OS Version-Specific Configuration: Configuration settings for upgrading between different RHEL versions.
"7": Defines settings specific to RHEL 7, including activation keys for pre-upgrade, during the upgrade, and post-upgrade phases."8": Defines settings for RHEL 8, similar to the structure above for RHEL 7."9": Defines settings for RHEL 9, structured the same as RHEL 7 and 8.
If you want, you can also define the leapp_preupg_opts variable to specify the target OS version you intend to upgrade.
Now that we have defined our variables in a central place, let’s further customize analysis and upgrade playbooks to include the tasks that set the correct OS config variables defined above;
Customized analysis.yml playbook
This is how our customized analysis.yml playbook finally looks like:
cat playbooks/analysis.yml---
- name: Analysis
hosts: all
strategy: free
gather_facts: true
become: true
force_handlers: true
tasks:
- name: Set OS-specific variables for Leapp upgrade
ansible.builtin.set_fact:
satellite_activation_key: "{{ os_config[ansible_distribution_major_version]['satellite_activation_key'] | default(omit) }}"
satellite_activation_key_leapp: "{{ os_config[ansible_distribution_major_version]['satellite_activation_key_leapp'] | default(omit) }}"
satellite_activation_key_post_leapp: "{{ os_config[ansible_distribution_major_version]['satellite_activation_key_post_leapp'] | default(omit) }}"
leapp_upgrade_opts: "{{ os_config[ansible_distribution_major_version]['leapp_upgrade_opts'] | default(omit) }}"
when: ansible_distribution_major_version in os_config
- name: Generate preupgrade analysis report
ansible.builtin.import_role:
name: analysisCustomized upgrade.yml playbook
This is how our customized upgrade.yml playbook finally looks like:
cat playbooks/upgrade.yml---
- name: Upgrade
hosts: all
strategy: free
become: true
force_handlers: true
tasks:
- name: Set OS-specific variables for Leapp upgrade
ansible.builtin.set_fact:
satellite_activation_key: "{{ os_config[ansible_distribution_major_version]['satellite_activation_key'] | default(omit) }}"
satellite_activation_key_leapp: "{{ os_config[ansible_distribution_major_version]['satellite_activation_key_leapp'] | default(omit) }}"
satellite_activation_key_post_leapp: "{{ os_config[ansible_distribution_major_version]['satellite_activation_key_post_leapp'] | default(omit) }}"
leapp_upgrade_opts: "{{ os_config[ansible_distribution_major_version]['leapp_upgrade_opts'] | default(omit) }}"
when: ansible_distribution_major_version in os_config
- name: Perform OS upgrade
ansible.builtin.import_role:
name: upgradeThe custom collection directory now looks like:
ls -1 ~/ansible-env/infra.leapp/ansible.cfg
inventory
meta
playbooks
plugins
README.md
rolesCreate Custom Preflight Playbook
Here, we are introducing a custom preflight playbook that ensures the system is fully prepared before running the preupgrade analysis. This includes ensuring the system is fully patched to the latest minor release of its current major version (e.g., RHEL 7.9) before it can be upgraded to the next major version (e.g., RHEL 8.10) among other tasks.
We have placed the playbook under the playbooks directory. Below is the configuration of the preflight.yml file:
cat playbooks/preflight.yml---
- name: Prepare Hosts for Leapp Upgrade
hosts: all
gather_facts: true
become: true
tasks:
- name: Verify Satellite server connectivity
uri:
url: "{{ satellite_katello_rpm }}"
method: HEAD
return_content: no
status_code: 200
validate_certs: false
register: satellite_check
failed_when: satellite_check.status != 200
- name: Unregister the host for fresh registration to Satellite
shell: |
yum clean all || true
rm -rf /var/cache/dnf/* /var/cache/yum/* || true
subscription-manager remove --all || true
subscription-manager unregister || true
subscription-manager clean || true
rm -rf /etc/pki/consumer /etc/pki/entitlement || true
changed_when: true
- name: Remove any katello consumer packages
shell: |
rpm -qa | grep '^katello-ca-consumer' | xargs -r yum remove -y
changed_when: true
ignore_errors: false
- name: Backup any existing custom repo files
command: |
find /etc/yum.repos.d/ -name "*.repo" ! -name "redhat.repo"
-exec mv {} {}.pre-upgrade.{{ ansible_date_time.date }} \;
- name: Install fresh katello consumer agent
package:
name: "{{ satellite_katello_rpm }}"
state: present
disable_gpg_check: true
- name: Register host to Satellite with normal update activation key
community.general.redhat_subscription:
state: present
activationkey: "{{ os_config[ansible_distribution_major_version].satellite_activation_key }}"
org_id: "{{ satellite_organization }}"
force_register: true
register: sub_result
failed_when: sub_result.failed and 'already registered' not in sub_result.msg
- name: Clear yum versionlock configuration
shell: |
yum versionlock clear || true
changed_when: true
- name: Remove releasever set in subscription-manager
command:
cmd: subscription-manager release --unset
changed_when: true
failed_when: false
- name: Get the list of enabled repos
command: yum repolist enabled
register: enabled_repos
changed_when: false
- name: Show enabled repos
debug:
var: enabled_repos.stdout_lines
- name: Install additional package utilities
package:
name: yum-utils
state: present
update_cache: true
- name: Update all packages to latest (RHEL 7)
yum:
name: '*'
state: latest
update_cache: true
when: ansible_facts['distribution_major_version'] == '7'
register: update_result_7
- name: Update all packages to latest (RHEL 8+)
dnf:
name: '*'
state: latest
update_cache: true
allowerasing: true
when: ansible_facts['distribution_major_version'] | int > 7
register: update_result_8
- name: Get removed packages from system logs (RHEL 7+)
shell: >
{{
'grep "Erased" /var/log/yum.log || true'
if (ansible_facts['distribution_major_version'] | int) <= 7
else 'grep "Removed" /var/log/dnf.log || true'
}}
register: removed_packages
changed_when: false
- name: Show removed packages
debug:
var: removed_packages.stdout_lines
- name: Check if server reboot is required
command: needs-restarting -r
register: needs_restarting
changed_when: needs_restarting.rc == 1
failed_when: false
- name: Reboot the server (if required)
reboot:
reboot_timeout: 3600
when: needs_restarting.rc == 1
In summary, the preflight playbook does the following:
- Verifies connectivity to the Satellite server to ensure it can reach the necessary repositories for fresh updates.
- Unregisters the host from Satellite and cleans up any previous configurations to ensure a fresh start.
- Re-registers the system to Satellite.
- Backs up any existing custom repository files.
- Updates all installed packages to the latest available versions, ensuring the system is fully patched before the upgrade.
- Checks if a reboot is required and performs a reboot if necessary to apply any updates.
By customizing the infra.leapp collection and utilizing this preflight playbook, we ensure that the upgrade process is smoother and more tailored to the specific needs of our environment.
We left the rest of the roles/playbooks with the default configurations.
This is how our general customized infra.leapp collection directory now look like:
tree ..
├── ansible.cfg
├── inventory
│ ├── group_vars
│ │ └── all.yml
│ └── rhel
├── meta
│ └── runtime.yml
├── playbooks
│ ├── analysis.yml
│ ├── prelight.yml
│ ├── remediate.yml
│ ├── rolling_upgrade_ha_cluster.yml
│ └── upgrade.yml
├── plugins
├── README.md
└── roles
├── analysis
│ ├── defaults
│ │ └── main.yml
│ ├── files
│ │ └── check-inodes.sh
│ ├── handlers
│ │ └── main.yml
│ ├── meta
│ │ └── main.yml
│ ├── README.md
│ ├── tasks
│ │ ├── analysis-leapp.yml
│ │ ├── analysis-preupg.yml
│ │ ├── check-results-file.yml
│ │ └── main.yml
│ ├── templates
│ ├── tests
│ │ ├── inventory
│ │ └── test.yml
│ └── vars
│ └── main.yml
├── common
│ ├── defaults
│ │ └── main.yml
│ ├── files
│ ├── handlers
│ │ └── main.yml
│ ├── meta
│ │ └── main.yml
│ ├── README.md
│ ├── tasks
│ │ ├── custom_local_repos.yml
│ │ └── main.yml
│ ├── templates
│ ├── tests
│ │ ├── inventory
│ │ └── test.yml
│ └── vars
│ └── main.yml
├── parse_leapp_report
│ ├── defaults
│ │ └── main.yml
│ ├── files
│ ├── handlers
│ │ └── main.yml
│ ├── meta
│ │ └── main.yml
│ ├── README.md
│ ├── tasks
│ │ └── main.yml
│ ├── templates
│ ├── tests
│ │ ├── inventory
│ │ └── test.yml
│ └── vars
│ └── main.yml
├── remediate
│ ├── defaults
│ │ └── main.yml
│ ├── handlers
│ │ └── main.yml
│ ├── meta
│ │ └── main.yml
│ ├── README.md
│ ├── tasks
│ │ ├── leapp_cifs_detected.yml
│ │ ├── leapp_corrupted_grubenv_file.yml
│ │ ├── leapp_custom_network_scripts_detected.yml
│ │ ├── leapp_deprecated_sshd_directive.yml
│ │ ├── leapp_firewalld_allowzonedrifting.yml
│ │ ├── leapp_firewalld_unsupported_tftp_client.yml
│ │ ├── leapp_loaded_removed_kernel_drivers.yml
│ │ ├── leapp_missing_efibootmgr.yml
│ │ ├── leapp_missing_pkg.yml
│ │ ├── leapp_missing_yum_plugins.yml
│ │ ├── leapp_multiple_kernels.yml
│ │ ├── leapp_newest_kernel_not_in_use.yml
│ │ ├── leapp_nfs_detected.yml
│ │ ├── leapp_non_persistent_partitions.yml
│ │ ├── leapp_non_standard_openssl_config.yml
│ │ ├── leapp_old_postgresql_data.yml
│ │ ├── leapp_pam_tally2.yml
│ │ ├── leapp_partitions_with_noexec.yml
│ │ ├── leapp_relative_symlinks.yml
│ │ ├── leapp_remote_using_root.yml
│ │ ├── leapp_rpms_with_rsa_sha1_detected.yml
│ │ ├── leapp_unavailable_kde.yml
│ │ ├── leapp_vdo_check_needed.yml
│ │ └── main.yml
│ ├── templates
│ ├── tests
│ │ ├── inventory
│ │ └── test.yml
│ └── vars
│ └── main.yml
└── upgrade
├── defaults
│ └── main.yml
├── handlers
│ └── main.yml
├── meta
│ ├── argument_spec.yml
│ ├── collection-requirements.yml
│ └── main.yml
├── README.md
├── tasks
│ ├── disable-previous-repo-files.yml
│ ├── grub2-upgrade.yml
│ ├── handle-old-packages.yml
│ ├── leapp-post-upgrade-crypto.yml
│ ├── leapp-post-upgrade-selinux.yml
│ ├── leapp-post-upgrade.yml
│ ├── leapp-upgrade-validation.yml
│ ├── leapp-upgrade.yml
│ ├── main.yml
│ ├── redhat-upgrade-tool-post-upgrade.yml
│ ├── redhat-upgrade-tool-upgrade.yml
│ ├── rmmod-kernel-modules.yml
│ ├── update-and-reboot.yml
│ └── upgrade-validation.yml
├── templates
│ └── etc_default_grub.j2
├── tests
│ ├── inventory
│ └── test.yml
└── vars
└── main.yml
50 directories, 94 files
Option 2: Fork the Collection and Customize
This is the strategy I would recommend for a serious, long-term automation project. By forking the collection's Git repository, you create your own manageable version while retaining a link to the original project. This gives you the power to customize safely and the ability to pull in upstream updates.
You will need to have an account on GitHub to fork the repository. It is also possible to fork it into your local GitLab repository, but we wont cover that over this guide.
Fork the infra.leapp project:
- Login to your GitHub account.
- Then go to the official RedHat CoP infra.leapp GitHub repository.
- Click the Fork button at the top-right of the page to create a copy of the repo with your preferred name under your account.
- After forking, the new repository will be located at https://github.com/yourusername/projectname. We named ours as infra.leapp.fork.
- Next, clone your forked repository to your local machine:
git clone https://github.com/yourusername/projectname.git - Make your desired changes. NOTE: Only modify the forked repository when you need to change how a playbook/role behaves internally specifically when its default behavior does not align with or breaks your environment's requirements. For example, in my tests, I found out that RHEL 9 was not supported by the remediation role and also, some remediation task was disabling SSH password-based authentication which is crucial for my environment and as such, these are the only changes we will make in our forked infra.leapp repository (You should not add your personal inventory, group_vars, or custom playbooks here):
- Updated the main remediation role task (
roles/remediate/tasks/main.yml) to support RHEL 9:---
# tasks file for remediations
- name: Check if the system is RHEL 7 or 8 or 9
ansible.builtin.assert:
that: ansible_distribution == 'RedHat' and ( ansible_distribution_major_version|int == 8 or ansible_distribution_major_version|int == 7 or ansible_distribution_major_version|int == 9 )
msg: "This role is only applicable to RHEL 7 or 8 or 9"
tags: remediate
- name: Remediate the system
ansible.builtin.include_tasks: "{{ remediation_item }}.yml"
loop: "{{ remediation_playbooks }}"
loop_control:
loop_var: remediation_item
when: remediation_item in remediation_todo
... - Modified the
roles/remediate/tasks/leapp_remote_using_root.ymlremediation task to disable SSH root login while preserving password-based authentication:---
- name: leapp_remote_using_root | Fix potential issues with remote login using root
block:
- name: leapp_remote_using_root | Configure sshd to prohibit-passwords on root login
ansible.builtin.lineinfile:
path: "/etc/ssh/sshd_config"
regex: "^(#)?{{ item.key }}"
line: "{{ item.key }} {{ item.value }}"
state: present
loop:
- {key: "PermitRootLogin", value: "prohibit-password"}
# - {key: "PasswordAuthentication", value: "no"}
notify:
- Restart sshd
... - Add the new playbook to remediate the unsupported network configuration inhibitor as demonstrated above. Ensure it is included in the default list of remediation playbooks, found in:
roles/remediate/defaults/main.ymlunder theremediation_playbooks. - You can go through the playbooks, run the tests if you want and make further customization that align with your environment.
- See our customized forked repository status:
Sample output:git statusOn branch main
Your branch is up to date with 'origin/main'.
Changes not staged for commit:
(use "git add..." to update what will be committed)
(use "git restore..." to discard changes in working directory)
modified: roles/remediate/defaults/main.yml
modified: roles/remediate/tasks/leapp_remote_using_root.yml
modified: roles/remediate/tasks/main.yml
Untracked files:
(use "git add..." to include in what will be committed)
roles/remediate/tasks/leapp_unsupported_network_configuration.yml
no changes added to commit (use "git add" and/or "git commit -a")
- Updated the main remediation role task (
- Once you have made enough changes as per your liking, commit them and push them back to your forked repository.
Stage changes for the next commit:
Commit the changes:git add roles/remediate/defaults/main.yml \ roles/remediate/tasks/leapp_unsupported_network_configuration.yml \ roles/remediate/tasks/leapp_remote_using_root.yml \ roles/remediate/tasks/main.yml
Push the commits to the remote repository:git commit -m "feat: updated remediation tasks - Updated remediate main task to support RHEL 9 - Modified leapp_remote_using_root task to disable SSH root login while preserving password-based auth - Added new task: leapp_unsupported_network_configuration.yml to handle NIC naming issues (e.g. eth0, eth1) - Updated remediation defaults to include new playbook"git push
Building the Main Leapp Upgrade Ansible Project
Now, to build on top of the forked repository, this project introduces its own structure and logic while preserving upstream functionality. The forked infra.leapp collection serves as the base, and on top of that, we will add our project-specific customization such as a dedicated inventory/ directory, environment-specific variables under group_vars/, and new playbooks that reflect our infrastructure and upgrade policies.
These additions are layered non-invasively, meaning the original roles and logic remain intact. This approach allows us to:
- Extend functionality without breaking upstream compatibility
- Customize upgrade workflows and remediation logic for our specific use cases
- Maintain a clean separation between upstream-provided content and locally managed automation
Over time, this structure enables easier maintenance and rebasing when upstream changes are pulled in, while still supporting flexible, environment-specific automation.
Thus, on your localhost, create your main RHEL OS upgrade project directory. You can use any name of your liking for the main project directory.:
mkdir ~/ansible-env/rhel-in-place-leapp-upgradeWithin this directory:
- We have created our inventory directory (like we did above) containing:
- rhel hosts file.
- group_vars/all.yml group-level variables.
- Created the custom
playbooksdirectory containing (Note: we keep the fully qualified collection names):- preflight.yml playbook like the one we have above.
- analysis.yml playbook:
---
- name: Analysis
hosts: all
strategy: free
gather_facts: true
become: true
force_handlers: true
tasks:
- name: Set OS-specific variables for Leapp upgrade
ansible.builtin.set_fact:
satellite_activation_key: "{{ os_config[ansible_distribution_major_version]['satellite_activation_key'] | default(omit) }}"
satellite_activation_key_leapp: "{{ os_config[ansible_distribution_major_version]['satellite_activation_key_leapp'] | default(omit) }}"
satellite_activation_key_post_leapp: "{{ os_config[ansible_distribution_major_version]['satellite_activation_key_post_leapp'] | default(omit) }}"
leapp_upgrade_opts: "{{ os_config[ansible_distribution_major_version]['leapp_upgrade_opts'] | default(omit) }}"
when: ansible_distribution_major_version in os_config
- name: Generate preupgrade analysis report
ansible.builtin.import_role:
name: infra.leapp.analysis
... - upgrade.yml playbook:
---
- name: Upgrade
hosts: all
strategy: free
become: true
force_handlers: true
tasks:
- name: Set OS-specific variables for Leapp upgrade
ansible.builtin.set_fact:
satellite_activation_key: "{{ os_config[ansible_distribution_major_version]['satellite_activation_key'] | default(omit) }}"
satellite_activation_key_leapp: "{{ os_config[ansible_distribution_major_version]['satellite_activation_key_leapp'] | default(omit) }}"
satellite_activation_key_post_leapp: "{{ os_config[ansible_distribution_major_version]['satellite_activation_key_post_leapp'] | default(omit) }}"
leapp_upgrade_opts: "{{ os_config[ansible_distribution_major_version]['leapp_upgrade_opts'] | default(omit) }}"
when: ansible_distribution_major_version in os_config
- name: Perform OS upgrade
ansible.builtin.import_role:
name: infra.leapp.upgrade
... - remediate.yml playbook:
--- - name: Remediate hosts: all strategy: free become: true force_handlers: true vars: remediation_todo: - leapp_firewalld_allowzonedrifting - leapp_missing_pkg - leapp_vdo_check_needed - leapp_remote_using_root - leapp_nfs_detected - leapp_vdo_check_needed - leapp_partitions_with_noexec - leapp_rpms_with_rsa_sha1_detected - leapp_custom_network_scripts_detected - leapp_unsupported_network_configuration tasks: - name: Perform remediations on the system ansible.builtin.import_role: name: infra.leapp.remediate
- Next, we need to install and use the forked infra.leapp collection. Therefore, create a
requirements.ymlfile in your main project directory that tells Ansible to install the collection from your Git repository, and not from Ansible Galaxy. Note, we have also included the dependent collections:
Replace the path to your forked Git repository project accordingly.cat requirements.yml---
collections:
- name: https://github.com/yourusername/project-name.git
type: git
- name: ansible.posix
version: ">=1.5.1"
- name: community.general
version: ">=6.6.0"
- name: fedora.linux_system_roles # or redhat.rhel_system_roles see upgrade readme for more details
version: ">=1.21.0"
After the customization, this is how my main Leapp Ansible project now look like:
tree ..
├── inventory
│ ├── group_vars
│ │ └── all.yml
│ └── rhel
├── playbooks
│ ├── analysis.yml
│ ├── prelight.yml
│ ├── remediate.yml
│ └── upgrade.yml
├── README.md
└── requirements.yml
4 directories, 8 filesThen, run the collection installation command:
ansible-galaxy collection install -r requirements.yml --forceYour playbooks will now use your customized version of the collection.
So, what is next?
- You can now execute your playbooks one by one from your main upgrade project to upgrade your RHEL Hosts. We will check this on our next section on implementing the complete upgrade workflow.
- Even better, you can create yet another GitHub/Gitlab project for your main Leapp upgrade Ansible project to make ti easy to integrate with automation tools such as AAP/AWX.
In our environment, we have created a GitHub repository for our main Leapp upgrade Anisble project. This makes it easy for us to use it on our automation tools; AWX/AAP.
Keeping Forked Repository Updated in Git/GitHub
When you fork a repository on GitHub, you're creating a copy of it under your own GitHub account. However, the original repository (also called the upstream) may continue to receive updates from the original maintainers (e.g., Red Hat CoP in this example). If you want to benefit from those updates: bug fixes, new features, etc. you need to sync your fork with the upstream repository.
To keep the forked repository up-to-date with upstream repository:
- Clone Your Fork (If Not Already Done)
git clone https://github.com/yourusername/projectname.git - Add the original/upstream RedHat CoP infra.leapp repository as a remote to your forked repository to tell Git where the original source lives so you can fetch updates from it.
Navigate into your local forked repo directory:
Then add upstream repository as a remote:cd projectname
You can check that it was added correctly with:git remote add upstream https://github.com/redhat-cop/infra.leapp.git
You should see bothgit remote -vorigin(your fork) andupstream(the original repository) listed. - Fetch the latest commits and branches from the original/upstream RedHat CoP repository:
This pulls in the changes from upstream but doesn’t apply the changes/bug fixes to your forked repository.git fetch upstream - Next, apply the upstream changes to your local branch using two methods:
- Merge: The merge method fetches the changes from the upstream repository and merge them into your local forked branch. This creates a merge commit, which records the combination of both histories and shows that two branches were joined.
git checkout main
git merge upstream/main - Rebase: The rebase method fetches the changes from upstream and reapply your local forked repository commits on top of them. This does not create a merge commit, but instead creates a clean, linear history by rewriting your local commits as if they were made after the upstream changes.
You can also sync a feature branch if you need.git checkout main
git rebase upstream/main
- Merge: The merge method fetches the changes from the upstream repository and merge them into your local forked branch. This creates a merge commit, which records the combination of both histories and shows that two branches were joined.
- After merging or rebasing, you can push the changes back to your GitHub fork:
This updates your forked repository on GitHub to match the latest changes from the original repository.git push origin main - The last step is to pull the updates into your main automation project. You can do this by reinstalling the collection.
Navigate to your main project:
And reinstall the collection from your updated forked repository:cd ~/ansible-env/rhel-in-place-leapp-upgradeansible-galaxy collection install -r requirements.yml --force
Of course, you can automate this process via Github actions, scripts, e.t.c.
Supported OS Upgrade Paths
Before executing the workflow, it’s important to understand the supported RHEL upgrade paths:
Make sure your system is on the latest minor version to ensure a smooth upgrade to the next major release. In our custom playbooks, the preflight.yml will ensure the OS is patched/updated to the latest minor version before the upgrade.
Below are our test RHEL nodes current OS release versions:
[kifarunix@db01 ~]$ cat /etc/redhat-release
Red Hat Enterprise Linux Server release 7.9 (Maipo)[kifarunix@app01 ~]$ cat /etc/redhat-release
Red Hat Enterprise Linux release 8.10 (Ootpa)[kifarunix@lb01 ~]$ cat /etc/redhat-release
Red Hat Enterprise Linux release 9.4 (Plow)RHEL OS Upgrade Prerequisites
For a successful RHEL OS upgrade, it's important to consider several key factors that ensure the upgrade process is safe, supported, and effective. These considerations help reduce the risk of upgrade failure.
Here are the most important factors to consider:
- Supported Upgrade Path: Confirm that you're upgrading between Red Hat-supported versions. Refer above the supported upgrade paths.
- System Backup/Snapshot: Take a full backup of the system, including application data, configurations, and databases. This allows you to recover quickly in case of failure.
- Sufficient Disk Space: Make sure there's enough free disk space on Core OS partitions such as
/,/boot, and/varto accommodate the upgrade.
Ideally, ensure:- /boot: 100-250 MB free (recommended 500 MB-1 GB total) for new kernels and initramfs (~50-100 MB each).
- / (root): 1-3 GB free (recommended 5-10 GB total) for temporary files and system updates; more if /usr or /var are not separate.
- /usr: 1-3 GB free if separate, especially for XFS ftype=0 systems with older Leapp versions (pre-0.16).
- /var: Up to 4 GB for preupgrade, 5-10+ GB for full upgrade (more for overlays or many packages in /var/lib/leapp).
- /tmp: 1-2 GB free if separate, for general temporary files.
Pre-upgrade will anyway give you a report if some partitions have less disk space.
- If the system has been previously upgraded, ensure that all required post-upgrade steps have been completed.
- Shared Library Paths: Verify correct paths for critical system-managed shared libraries (e.g., OpenSSL, glibc, ld.so) to prevent severe failures like kernel panics.
Implementing the Complete Upgrade Workflow
As a demo, you can execute the playbooks directly from the Ansible command line interface (CLI), providing a simple and efficient way to manage the upgrade process. Alternatively, for more robust automation and scaling, you can use Ansible Automation Platform (AAP) or AWX to run the playbooks. These platforms offer a more enterprise-ready approach with features such as centralized management, job scheduling, and enhanced logging.
The upgrade workflow consists of four sequential playbooks that must be executed in order:
- preflight.yml
- analysis.yml
- remediate.yml
- [Optional] Rerun analysis.yml again
- upgrade.yml
To begin with, let's navigate ~/ansible-env/infra.leapp or our custom main project directory using forked infra.leapp collections.
cd ~/ansible-env/infra.leappOr:
cd ~/ansible-env/rhel-in-place-leapp-upgrade1. System Preparation
Our preflight.yml palybook handles Satellite connectivity verification, subscription management, repository configuration, and essential package updates required before initiating Leapp operations.
ansible-playbook -i inventory/rhel playbooks/preflight.ymlHere is the sample output of the preparation playbook:
ansible-playbook -i inventory/rhel playbooks/preflight.yml
PLAY [Prepare Hosts for Leapp Upgrade] ***********************************************************************************************************************************************************************
TASK [Gathering Facts] ***************************************************************************************************************************************************************************************
ok: [192.168.122.115]
ok: [192.168.122.113]
ok: [192.168.122.114]
TASK [Verify Satellite server connectivity] ******************************************************************************************************************************************************************
ok: [192.168.122.115]
ok: [192.168.122.114]
ok: [192.168.122.113]
TASK [Unregister the host for fresh registration to Satellite] ***********************************************************************************************************************************************
changed: [192.168.122.113]
changed: [192.168.122.114]
changed: [192.168.122.115]
TASK [Remove any katello consumer packages] ******************************************************************************************************************************************************************
changed: [192.168.122.115]
changed: [192.168.122.113]
changed: [192.168.122.114]
TASK [Backup any existing custom repo files] *****************************************************************************************************************************************************************
changed: [192.168.122.115]
changed: [192.168.122.114]
changed: [192.168.122.113]
TASK [Install fresh katello consumer agent] ******************************************************************************************************************************************************************
changed: [192.168.122.113]
changed: [192.168.122.115]
changed: [192.168.122.114]
TASK [Register host to Satellite with normal update activation key] ******************************************************************************************************************************************
changed: [192.168.122.113]
changed: [192.168.122.115]
changed: [192.168.122.114]
TASK [Clear yum versionlock configuration] *******************************************************************************************************************************************************************
changed: [192.168.122.115]
changed: [192.168.122.114]
changed: [192.168.122.113]
TASK [Remove releasever set in subscription-manager] *********************************************************************************************************************************************************
changed: [192.168.122.115]
changed: [192.168.122.114]
changed: [192.168.122.113]
TASK [Get the list of enabled repos] *************************************************************************************************************************************************************************
ok: [192.168.122.115]
ok: [192.168.122.114]
ok: [192.168.122.113]
TASK [Show enabled repos] ************************************************************************************************************************************************************************************
ok: [192.168.122.113] => {
"enabled_repos.stdout_lines": [
"Loaded plugins: product-id, search-disabled-repos, subscription-manager",
"repo id repo name status",
"!rhel-7-server-extras-rpms/x86_64 Red Hat Enterprise Linux 7 Server - Ex 1,491",
"!rhel-7-server-rpms/7Server/x86_64 Red Hat Enterprise Linux 7 Server (RPM 34,484",
"repolist: 35,975"
]
}
ok: [192.168.122.114] => {
"enabled_repos.stdout_lines": [
"Updating Subscription Management repositories.",
"repo id repo name",
"rhel-8-for-x86_64-appstream-rpms Red Hat Enterprise Linux 8 for x86_64 - AppStream (RPMs)",
"rhel-8-for-x86_64-baseos-rpms Red Hat Enterprise Linux 8 for x86_64 - BaseOS (RPMs)"
]
}
ok: [192.168.122.115] => {
"enabled_repos.stdout_lines": [
"Updating Subscription Management repositories.",
"repo id repo name",
"rhel-9-for-x86_64-appstream-rpms Red Hat Enterprise Linux 9 for x86_64 - AppStream (RPMs)",
"rhel-9-for-x86_64-baseos-rpms Red Hat Enterprise Linux 9 for x86_64 - BaseOS (RPMs)",
"satellite-capsule-6.16-for-rhel-9-x86_64-rpms Red Hat Satellite Capsule 6.16 for RHEL 9 x86_64 (RPMs)"
]
}
TASK [Install additional package utilities] ******************************************************************************************************************************************************************
ok: [192.168.122.113]
changed: [192.168.122.115]
ok: [192.168.122.114]
TASK [Update all packages to latest (RHEL 7)] ****************************************************************************************************************************************************************
skipping: [192.168.122.114]
skipping: [192.168.122.115]
changed: [192.168.122.113]
TASK [Update all packages to latest (RHEL 8+)] ***************************************************************************************************************************************************************
skipping: [192.168.122.113]
changed: [192.168.122.114]
changed: [192.168.122.115]
TASK [Get removed packages from system logs (RHEL 7+)] *******************************************************************************************************************************************************
ok: [192.168.122.115]
ok: [192.168.122.114]
ok: [192.168.122.113]
TASK [Show removed packages] *********************************************************************************************************************************************************************************
ok: [192.168.122.113] => {
"removed_packages.stdout_lines": [
"Sep 11 05:51:33 Erased: katello-ca-consumer-satellite.kifarunix.com-1.0-1.noarch"
]
}
ok: [192.168.122.114] => {
"removed_packages.stdout_lines": [
"2025-09-11T05:58:19-0400 DEBUG Removed: containerd.io-1.6.32-3.1.el8.x86_64",
"2025-09-11T05:58:19-0400 DEBUG Removed: docker-ce-3:26.1.3-1.el8.x86_64",
"2025-09-11T05:58:19-0400 DEBUG Removed: docker-ce-rootless-extras-26.1.3-1.el8.x86_64"
]
}
ok: [192.168.122.115] => {
"removed_packages.stdout_lines": []
}
TASK [Check if server reboot is required] ********************************************************************************************************************************************************************
changed: [192.168.122.113]
changed: [192.168.122.115]
changed: [192.168.122.114]
TASK [Reboot the server (if required)] ***********************************************************************************************************************************************************************
changed: [192.168.122.115]
changed: [192.168.122.113]
changed: [192.168.122.114]
PLAY RECAP ***************************************************************************************************************************************************************************************************
192.168.122.113 : ok=17 changed=10 unreachable=0 failed=0 skipped=1 rescued=0 ignored=0
192.168.122.114 : ok=17 changed=10 unreachable=0 failed=0 skipped=1 rescued=0 ignored=0
192.168.122.115 : ok=17 changed=11 unreachable=0 failed=0 skipped=1 rescued=0 ignored=0
The systems have been registered to the repository server, updated and rebooted. We also have information of packages removed on each server.
2. Pre-Upgrade Analysis
The analysis playbook leverages the infra.leapp analysis role to perform comprehensive system assessment, identifying potential upgrade errors/inhibitors and generating detailed reports.
This step will run what you would do with leapp preupgrade.
ansible-playbook -i inventory/rhel playbooks/analysis.ymlSample pre-upgrade analysis report:
PLAY [Analysis] **********************************************************************************************************************************************************************************************
TASK [Gathering Facts] ***************************************************************************************************************************************************************************************
ok: [192.168.122.114]
ok: [192.168.122.115]
TASK [Set OS-specific variables for Leapp upgrade] ***********************************************************************************************************************************************************
ok: [192.168.122.114]
ok: [192.168.122.115]
TASK [Gathering Facts] ***************************************************************************************************************************************************************************************
ok: [192.168.122.113]
TASK [Set OS-specific variables for Leapp upgrade] ***********************************************************************************************************************************************************
ok: [192.168.122.113]
TASK [infra.leapp.common : Log directory exists] *************************************************************************************************************************************************************
ok: [192.168.122.115]
ok: [192.168.122.114]
ok: [192.168.122.113]
TASK [infra.leapp.common : Check for existing log file] ******************************************************************************************************************************************************
ok: [192.168.122.114]
ok: [192.168.122.115]
TASK [infra.leapp.common : Fail if log file already exists] **************************************************************************************************************************************************
skipping: [192.168.122.114]
skipping: [192.168.122.115]
TASK [infra.leapp.common : Check for existing log file] ******************************************************************************************************************************************************
ok: [192.168.122.113]
TASK [infra.leapp.common : Fail if log file already exists] **************************************************************************************************************************************************
skipping: [192.168.122.113]
TASK [infra.leapp.common : Create new log file] **************************************************************************************************************************************************************
changed: [192.168.122.115]
changed: [192.168.122.114]
changed: [192.168.122.113]
TASK [infra.leapp.common : /etc/ansible/facts.d directory exists] ********************************************************************************************************************************************
ok: [192.168.122.115]
ok: [192.168.122.114]
ok: [192.168.122.113]
TASK [infra.leapp.common : Capture current ansible_facts for validation after upgrade] ***********************************************************************************************************************
changed: [192.168.122.115]
changed: [192.168.122.114]
changed: [192.168.122.113]
TASK [infra.leapp.common : Capture a list of non-rhel versioned packages] ************************************************************************************************************************************
ok: [192.168.122.115]
TASK [infra.leapp.common : Create fact with the non-rhel versioned packages list] ****************************************************************************************************************************
ok: [192.168.122.115]
TASK [infra.leapp.common : Capture the list of non-rhel versioned packages in a separate fact file] **********************************************************************************************************
ok: [192.168.122.115]
TASK [infra.leapp.analysis : Include tasks for preupg assistant analysis] ************************************************************************************************************************************
skipping: [192.168.122.115]
TASK [infra.leapp.analysis : Include tasks for leapp preupgrade analysis] ************************************************************************************************************************************
included: /home/kifarunix/.ansible/collections/ansible_collections/infra/leapp/roles/analysis/tasks/analysis-leapp.yml for 192.168.122.115
TASK [infra.leapp.common : Capture a list of non-rhel versioned packages] ************************************************************************************************************************************
ok: [192.168.122.114]
TASK [infra.leapp.common : Create fact with the non-rhel versioned packages list] ****************************************************************************************************************************
ok: [192.168.122.114]
TASK [infra.leapp.common : Capture a list of non-rhel versioned packages] ************************************************************************************************************************************
ok: [192.168.122.113]
TASK [infra.leapp.common : Create fact with the non-rhel versioned packages list] ****************************************************************************************************************************
ok: [192.168.122.113]
TASK [infra.leapp.common : Capture the list of non-rhel versioned packages in a separate fact file] **********************************************************************************************************
ok: [192.168.122.114]
TASK [infra.leapp.analysis : Include tasks for preupg assistant analysis] ************************************************************************************************************************************
skipping: [192.168.122.114]
TASK [infra.leapp.analysis : Include tasks for leapp preupgrade analysis] ************************************************************************************************************************************
included: /home/kifarunix/.ansible/collections/ansible_collections/infra/leapp/roles/analysis/tasks/analysis-leapp.yml for 192.168.122.114
TASK [infra.leapp.common : Capture the list of non-rhel versioned packages in a separate fact file] **********************************************************************************************************
ok: [192.168.122.113]
TASK [infra.leapp.analysis : Include tasks for preupg assistant analysis] ************************************************************************************************************************************
skipping: [192.168.122.113]
TASK [infra.leapp.analysis : Include tasks for leapp preupgrade analysis] ************************************************************************************************************************************
included: /home/kifarunix/.ansible/collections/ansible_collections/infra/leapp/roles/analysis/tasks/analysis-leapp.yml for 192.168.122.113
TASK [infra.leapp.analysis : analysis-leapp | Register to leapp activation key] ******************************************************************************************************************************
changed: [192.168.122.115]
TASK [analysis-leapp | Include custom_local_repos for local_repos_pre_leapp] *********************************************************************************************************************************
skipping: [192.168.122.115]
TASK [infra.leapp.analysis : analysis-leapp | Install packages for preupgrade analysis on RHEL 7] ************************************************************************************************************
skipping: [192.168.122.115]
TASK [infra.leapp.analysis : analysis-leapp | Install packages for preupgrade analysis on RHEL 8] ************************************************************************************************************
skipping: [192.168.122.115]
TASK [infra.leapp.analysis : analysis-leapp | Register to leapp activation key] ******************************************************************************************************************************
changed: [192.168.122.113]
TASK [analysis-leapp | Include custom_local_repos for local_repos_pre_leapp] *********************************************************************************************************************************
skipping: [192.168.122.113]
TASK [infra.leapp.analysis : analysis-leapp | Register to leapp activation key] ******************************************************************************************************************************
changed: [192.168.122.114]
TASK [analysis-leapp | Include custom_local_repos for local_repos_pre_leapp] *********************************************************************************************************************************
skipping: [192.168.122.114]
TASK [infra.leapp.analysis : analysis-leapp | Install packages for preupgrade analysis on RHEL 7] ************************************************************************************************************
skipping: [192.168.122.114]
TASK [infra.leapp.analysis : analysis-leapp | Install packages for preupgrade analysis on RHEL 9] ************************************************************************************************************
changed: [192.168.122.115]
TASK [infra.leapp.analysis : analysis-leapp | Ensure leapp log directory exists] *****************************************************************************************************************************
ok: [192.168.122.115]
TASK [infra.leapp.analysis : analysis-leapp | Populate leapp_answers file] ***********************************************************************************************************************************
changed: [192.168.122.115]
TASK [analysis-leapp | Create /etc/leapp/files/leapp_upgrade_repositories.repo] ******************************************************************************************************************************
skipping: [192.168.122.115]
TASK [infra.leapp.analysis : analysis-leapp | Install packages for preupgrade analysis on RHEL 8] ************************************************************************************************************
ok: [192.168.122.114]
TASK [infra.leapp.analysis : analysis-leapp | Install packages for preupgrade analysis on RHEL 9] ************************************************************************************************************
skipping: [192.168.122.114]
TASK [infra.leapp.analysis : analysis-leapp | Ensure leapp log directory exists] *****************************************************************************************************************************
ok: [192.168.122.114]
TASK [infra.leapp.analysis : analysis-leapp | Populate leapp_answers file] ***********************************************************************************************************************************
changed: [192.168.122.114]
TASK [analysis-leapp | Create /etc/leapp/files/leapp_upgrade_repositories.repo] ******************************************************************************************************************************
skipping: [192.168.122.114]
TASK [infra.leapp.analysis : analysis-leapp | Install packages for preupgrade analysis on RHEL 7] ************************************************************************************************************
changed: [192.168.122.113]
TASK [infra.leapp.analysis : analysis-leapp | Install packages for preupgrade analysis on RHEL 8] ************************************************************************************************************
skipping: [192.168.122.113]
TASK [infra.leapp.analysis : analysis-leapp | Install packages for preupgrade analysis on RHEL 9] ************************************************************************************************************
skipping: [192.168.122.113]
TASK [infra.leapp.analysis : analysis-leapp | Ensure leapp log directory exists] *****************************************************************************************************************************
ok: [192.168.122.113]
TASK [infra.leapp.analysis : analysis-leapp | Populate leapp_answers file] ***********************************************************************************************************************************
changed: [192.168.122.113]
TASK [analysis-leapp | Create /etc/leapp/files/leapp_upgrade_repositories.repo] ******************************************************************************************************************************
skipping: [192.168.122.113]
ASYNC POLL on 192.168.122.115: jid=j836712890705.9679 started=1 finished=0
ASYNC POLL on 192.168.122.114: jid=j128030620146.10214 started=1 finished=0
ASYNC POLL on 192.168.122.113: jid=j811384996191.10510 started=1 finished=0
ASYNC POLL on 192.168.122.115: jid=j836712890705.9679 started=1 finished=0
ASYNC FAILED on 192.168.122.114: jid=j128030620146.10214
TASK [infra.leapp.analysis : analysis-leapp | Leapp preupgrade report] ***************************************************************************************************************************************
changed: [192.168.122.114]
TASK [analysis-leapp | Include custom_local_repos for local_repos_post_analysis] *****************************************************************************************************************************
skipping: [192.168.122.114]
TASK [infra.leapp.analysis : analysis-leapp | Include check-results-file.yml] ********************************************************************************************************************************
included: /home/kifarunix/.ansible/collections/ansible_collections/infra/leapp/roles/analysis/tasks/check-results-file.yml for 192.168.122.114
TASK [infra.leapp.analysis : check-results-file | Result file status] ****************************************************************************************************************************************
ok: [192.168.122.114]
TASK [infra.leapp.analysis : check-results-file | Check that result file exists] *****************************************************************************************************************************
ok: [192.168.122.114] => {
"changed": false,
"msg": "All assertions passed"
}
TASK [analysis-leapp | Include the parse_leapp_report role to check for inhibitors] **************************************************************************************************************************
TASK [infra.leapp.parse_leapp_report : Default upgrade_inhibited to false] ***********************************************************************************************************************************
ok: [192.168.122.114]
TASK [infra.leapp.parse_leapp_report : Collect human readable report results] ********************************************************************************************************************************
ok: [192.168.122.114]
TASK [infra.leapp.parse_leapp_report : Collect JSON report results] ******************************************************************************************************************************************
ok: [192.168.122.114]
TASK [infra.leapp.parse_leapp_report : Parse report results] *************************************************************************************************************************************************
ok: [192.168.122.114]
TASK [infra.leapp.parse_leapp_report : Check for inhibitors] *************************************************************************************************************************************************
skipping: [192.168.122.114] => (item={'audience': 'sysadmin', 'detail': {'remediations': [{'context': 'If some of excluded repositories are still required to be used during the upgrade, execute leapp with the --enablerepo option with the repoid of the repository required to be enabled as an argument (the option can be used multiple times).', 'type': 'hint'}]}, 'groups': ['repository', 'failure'], 'key': '1b9132cb2362ae7830e48eee7811be9527747de8', 'severity': 'info', 'summary': 'The following repositories are not supported by Red Hat and are excluded from the list of repositories used during the upgrade.\n- codeready-builder-beta-for-rhel-9-x86_64-rpms\n- codeready-builder-beta-for-rhel-9-aarch64-rpms\n- codeready-builder-for-rhel-9-aarch64-eus-rpms\n- rhui-codeready-builder-for-rhel-9-aarch64-rhui-rpms\n- codeready-builder-beta-for-rhel-9-s390x-rpms\n- codeready-builder-for-rhel-9-rhui-rpms\n- codeready-builder-for-rhel-9-ppc64le-rpms\n- codeready-builder-for-rhel-9-x86_64-eus-rpms\n- codeready-builder-beta-for-rhel-9-ppc64le-rpms\n- codeready-builder-for-rhel-9-ppc64le-eus-rpms\n- codeready-builder-for-rhel-9-x86_64-rhui-rpms\n- codeready-builder-for-rhel-9-x86_64-rpms\n- rhui-codeready-builder-for-rhel-9-x86_64-rhui-rpms\n- codeready-builder-for-rhel-9-aarch64-rpms\n- codeready-builder-for-rhel-9-s390x-eus-rpms\n- codeready-builder-for-rhel-9-s390x-rpms', 'title': 'Excluded target system repositories', 'timeStamp': '2025-09-14T19:05:26.043394Z', 'hostname': 'app01.kifarunix.com', 'actor': 'repositories_blacklist', 'id': 'a09f821d262b79436575a05730f92bb04e849378c9223fae4c955f5d0f11eda5'})
skipping: [192.168.122.114] => (item={'audience': 'sysadmin', 'groups': ['boot'], 'key': 'ac7030e05d2ee248d34f08a9fa040b352bc410a3', 'severity': 'high', 'summary': 'On legacy (BIOS) systems, GRUB2 core (located in the gap between the MBR and the first partition) cannot be updated during the rpm transaction and Leapp has to initiate the update running "grub2-install" after the transaction. No action is needed before the upgrade. After the upgrade, it is recommended to check the GRUB configuration.', 'title': 'GRUB2 core will be automatically updated during the upgrade', 'timeStamp': '2025-09-14T19:05:36.887091Z', 'hostname': 'app01.kifarunix.com', 'actor': 'check_grub_core', 'id': 'b3502b5d6b2885f591a946892d9d6d8e55b832395ada5b02593f0d5a0c4f5ec3'})
skipping: [192.168.122.114] => (item={'audience': 'sysadmin', 'groups': ['kernel', 'drivers'], 'key': 'b03c306f274b33b4cf3c7cd3764366c599681481', 'severity': 'high', 'summary': 'The following RHEL 8 device drivers are no longer maintained RHEL 9:\n - ip_set\n', 'title': 'Leapp detected loaded kernel drivers which are no longer maintained in RHEL 9.', 'timeStamp': '2025-09-14T19:05:38.025716Z', 'hostname': 'app01.kifarunix.com', 'actor': 'check_detected_devices_and_drivers', 'id': '44b1b382f69da71a93bdb28907bff17db461538ae093bb69849130670ee18a6c'})
skipping: [192.168.122.114] => (item={'audience': 'sysadmin', 'groups': ['services'], 'key': '693963253195f418526f045b6d630a1f4c7a193d', 'severity': 'info', 'summary': "After the upgrade, this system will be automatically registered into Red Hat Insights. To skip the automatic registration, use the '--no-insights-register' command line option or set the LEAPP_NO_INSIGHTS_REGISTER environment variable.", 'title': 'Automatic registration into Red Hat Insights', 'timeStamp': '2025-09-14T19:05:38.519741Z', 'hostname': 'app01.kifarunix.com', 'actor': 'check_insights_auto_register', 'id': '9eb4184eb1a350d6e35a18f43cb4fe3d1463a2f75a429d1022318c38e86d5651'})
skipping: [192.168.122.114] => (item={'audience': 'sysadmin', 'detail': {'external': [{'title': 'Handling the migration of your custom and third-party applications', 'url': 'https://red.ht/customize-rhel-upgrade-actors'}], 'remediations': [{'context': 'The most simple solution that does not require additional knowledge about the upgrade process is the uninstallation of such packages before the upgrade and installing these (or their newer versions compatible with the target system) back after the upgrade. Also you can just try to upgrade the system on a testing machine (or after the full system backup) to see the result.\nHowever, it is common use case to migrate or upgrade installed third party packages together with the system during the in-place upgrade process. To examine how to customize the process to deal with such packages, follow the documentation in the attached link for more details.', 'type': 'hint'}]}, 'groups': ['sanity'], 'key': '13f0791ae5f19f50e7d0d606fb6501f91b1efb2c', 'severity': 'high', 'summary': 'The following packages have not been signed by Red Hat and may be removed during the upgrade process in case Red Hat-signed packages to be removed during the upgrade depend on them:\n- docker-buildx-plugin\n- docker-ce-cli\n- docker-compose-plugin', 'title': 'Packages not signed by Red Hat found on the system', 'timeStamp': '2025-09-14T19:05:38.596490Z', 'hostname': 'app01.kifarunix.com', 'actor': 'red_hat_signed_rpm_check', 'id': '78a1f4f1bfdc02527e386d0f1a3b7358fba1592ee4ae5ce7b99acc58561a5851'})
ok: [192.168.122.114] => (item={'audience': 'sysadmin', 'detail': {'external': [{'title': 'Why Leapp Preupgrade for RHEL 8 to 9 getting "Possible problems with remote login using root account" ?', 'url': 'https://access.redhat.com/solutions/7003083'}], 'related_resources': [{'scheme': 'package', 'title': 'openssh-server'}, {'scheme': 'file', 'title': '/etc/ssh/sshd_config'}], 'remediations': [{'context': 'If you depend on remote root logins using passwords, consider setting up a different user for remote administration or adding a comment into the sshd_config next to the "PermitRootLogin yes" directive to prevent rpm replacing it during the upgrade.', 'type': 'hint'}]}, 'groups': ['authentication', 'security', 'network', 'services', 'inhibitor'], 'key': '3d21e8cc9e1c09dc60429de7716165787e99515f', 'severity': 'high', 'summary': 'OpenSSH configuration file will get updated to RHEL9 version, no longer allowing root login with password. It is a good practice to use non-root administrative user and non-password authentications, but if you rely on the remote root login, this change can lock you out of this system.', 'title': 'Possible problems with remote login using root account', 'timeStamp': '2025-09-14T19:05:39.703699Z', 'hostname': 'app01.kifarunix.com', 'actor': 'openssh_permit_root_login', 'id': 'd395c016d16d65386835be02ce83705ecdc9eb38913cf68a98e1318d884d05c0'})
skipping: [192.168.122.114] => (item={'audience': 'sysadmin', 'detail': {'related_resources': [{'scheme': 'package', 'title': 'openssh-server'}, {'scheme': 'file', 'title': '/etc/ssh/sshd_config'}], 'remediations': [{'context': 'If you depend on remote root logins using passwords, consider setting up a different user for remote administration. Otherwise you can ignore this message.', 'type': 'hint'}]}, 'groups': ['authentication', 'security', 'network', 'services'], 'key': 'e738f78bc8f3a84411a4210e3b609057139d1855', 'severity': 'high', 'summary': 'RHEL9 no longer allows remote root logins, but the server configuration explicitly overrides this default. The configuration file will not be updated and root is still going to be allowed to login with password. This is not recommended and considered as a security risk.', 'title': 'Remote root logins globally allowed using password', 'timeStamp': '2025-09-14T19:05:39.705497Z', 'hostname': 'app01.kifarunix.com', 'actor': 'openssh_permit_root_login', 'id': '206f047e53bad8e749086b50e844bfc63593b406a3d52644d1c97fea26768430'})
skipping: [192.168.122.114] => (item={'audience': 'sysadmin', 'groups': ['selinux', 'security'], 'key': '8fb81863f8413bd617c2a55b69b8e10ff03d7c72', 'severity': 'info', 'summary': 'SElinux relabeling will be scheduled as the status is permissive/enforcing.', 'title': 'SElinux relabeling will be scheduled', 'timeStamp': '2025-09-14T19:05:40.301828Z', 'hostname': 'app01.kifarunix.com', 'actor': 'check_se_linux', 'id': 'b3c51ebc4ab4cecabed84b188aa4b415c02279b9f808b45e1b2ddced7fceda9a'})
TASK [infra.leapp.parse_leapp_report : Collect inhibitors] ***************************************************************************************************************************************************
ok: [192.168.122.114]
TASK [infra.leapp.parse_leapp_report : Collect high errors] **************************************************************************************************************************************************
ok: [192.168.122.114]
TASK [infra.leapp.analysis : Set stats for leapp_inhibitors] *************************************************************************************************************************************************
ok: [192.168.122.114]
TASK [infra.leapp.analysis : Notify analysis report is done handler] *****************************************************************************************************************************************
changed: [192.168.122.114]
RUNNING HANDLER [infra.leapp.common : Add end time to log file] **********************************************************************************************************************************************
changed: [192.168.122.114]
RUNNING HANDLER [infra.leapp.common : Slurp ripu.log file] ***************************************************************************************************************************************************
ok: [192.168.122.114]
RUNNING HANDLER [infra.leapp.common : Decode ripu.log file] **************************************************************************************************************************************************
ok: [192.168.122.114]
RUNNING HANDLER [infra.leapp.common : Rename log file] *******************************************************************************************************************************************************
changed: [192.168.122.114]
RUNNING HANDLER [infra.leapp.analysis : Register to pre leapp activation key] ********************************************************************************************************************************
skipping: [192.168.122.114]
RUNNING HANDLER [infra.leapp.analysis : Display inhibitors] **************************************************************************************************************************************************
ok: [192.168.122.114] => {
"results_inhibitors.stdout_lines": [
"Risk Factor: high (inhibitor)",
"Title: Possible problems with remote login using root account",
"Summary: OpenSSH configuration file will get updated to RHEL9 version, no longer allowing root login with password. It is a good practice to use non-root administrative user and non-password authentications, but if you rely on the remote root login, this change can lock you out of this system.",
"Related links:",
" - Why Leapp Preupgrade for RHEL 8 to 9 getting \"Possible problems with remote login using root account\" ?: https://access.redhat.com/solutions/7003083",
"Remediation: [hint] If you depend on remote root logins using passwords, consider setting up a different user for remote administration or adding a comment into the sshd_config next to the \"PermitRootLogin yes\" directive to prevent rpm replacing it during the upgrade.",
"Key: 3d21e8cc9e1c09dc60429de7716165787e99515f",
"----------------------------------------"
]
}
RUNNING HANDLER [infra.leapp.analysis : Display errors] ******************************************************************************************************************************************************
skipping: [192.168.122.114]
RUNNING HANDLER [infra.leapp.analysis : Preupgrade analysis report is done] **********************************************************************************************************************************
ok: [192.168.122.114] => {
"msg": "The preupgrade analysis report generation is now complete. WARNING: Inhibitors found. Review the tasks above or the result file at /var/log/leapp/leapp-report.txt."
}
ASYNC FAILED on 192.168.122.113: jid=j811384996191.10510
TASK [infra.leapp.analysis : analysis-leapp | Leapp preupgrade report] ***************************************************************************************************************************************
changed: [192.168.122.113]
TASK [analysis-leapp | Include custom_local_repos for local_repos_post_analysis] *****************************************************************************************************************************
skipping: [192.168.122.113]
TASK [infra.leapp.analysis : analysis-leapp | Include check-results-file.yml] ********************************************************************************************************************************
included: /home/kifarunix/.ansible/collections/ansible_collections/infra/leapp/roles/analysis/tasks/check-results-file.yml for 192.168.122.113
TASK [infra.leapp.analysis : check-results-file | Result file status] ****************************************************************************************************************************************
ok: [192.168.122.113]
TASK [infra.leapp.analysis : check-results-file | Check that result file exists] *****************************************************************************************************************************
ok: [192.168.122.113] => {
"changed": false,
"msg": "All assertions passed"
}
TASK [analysis-leapp | Include the parse_leapp_report role to check for inhibitors] **************************************************************************************************************************
TASK [infra.leapp.parse_leapp_report : Default upgrade_inhibited to false] ***********************************************************************************************************************************
ok: [192.168.122.113]
TASK [infra.leapp.parse_leapp_report : Collect human readable report results] ********************************************************************************************************************************
ok: [192.168.122.113]
TASK [infra.leapp.parse_leapp_report : Collect JSON report results] ******************************************************************************************************************************************
ok: [192.168.122.113]
TASK [infra.leapp.parse_leapp_report : Parse report results] *************************************************************************************************************************************************
ok: [192.168.122.113]
TASK [infra.leapp.parse_leapp_report : Check for inhibitors] *************************************************************************************************************************************************
ok: [192.168.122.113] => (item={'groups': ['network', 'inhibitor'], 'title': 'Unsupported network configuration', 'timeStamp': '2025-09-14T19:05:16.373921Z', 'hostname': 'db01.kifarunix.com', 'detail': {'external': [{'url': 'https://access.redhat.com/solutions/4067471', 'title': 'How to perform an in-place upgrade to RHEL 8 when using kernel NIC names on RHEL 7'}, {'url': 'https://access.redhat.com/solutions/7009239', 'title': 'RHEL 8 to RHEL 9: inplace upgrade fails at "Network configuration for unsupported device types detected"'}], 'remediations': [{'type': 'hint', 'context': 'Rename all ethX network interfaces following the attached KB solution article.'}]}, 'actor': 'persistentnetnamesdisable', 'summary': 'Detected multiple physical network interfaces where one or more use kernel naming (e.g. eth0). Upgrade process can not continue because stability of names can not be guaranteed. Please read the article at https://access.redhat.com/solutions/4067471 for more information.', 'audience': 'sysadmin', 'key': 'd3050d265759a79ce895e64f45e9c56e49b3a953', 'id': '713dbc223571ebf608d752e56cf94c92846b0ccde9442bccf499d6dd11703ab0', 'severity': 'high'})
skipping: [192.168.122.113] => (item={'groups': ['repository', 'failure'], 'title': 'Excluded target system repositories', 'timeStamp': '2025-09-14T19:05:16.440845Z', 'hostname': 'db01.kifarunix.com', 'detail': {'remediations': [{'type': 'hint', 'context': 'If some of excluded repositories are still required to be used during the upgrade, execute leapp with the --enablerepo option with the repoid of the repository required to be enabled as an argument (the option can be used multiple times).'}]}, 'actor': 'repositories_blacklist', 'summary': 'The following repositories are not supported by Red Hat and are excluded from the list of repositories used during the upgrade.\n- codeready-builder-beta-for-rhel-8-s390x-rpms\n- codeready-builder-beta-for-rhel-8-ppc64le-rpms\n- rhui-codeready-builder-for-rhel-8-x86_64-rhui-rpms\n- codeready-builder-for-rhel-8-aarch64-eus-rpms\n- codeready-builder-for-rhel-8-ppc64le-eus-rpms\n- codeready-builder-beta-for-rhel-8-x86_64-rpms\n- codeready-builder-for-rhel-8-aarch64-rpms\n- codeready-builder-for-rhel-8-s390x-rpms\n- codeready-builder-for-rhel-8-s390x-eus-rpms\n- codeready-builder-for-rhel-8-x86_64-eus-rpms\n- rhui-codeready-builder-for-rhel-8-aarch64-rhui-rpms\n- codeready-builder-beta-for-rhel-8-aarch64-rpms\n- codeready-builder-for-rhel-8-rhui-rpms\n- codeready-builder-for-rhel-8-x86_64-rhui-rpms\n- codeready-builder-for-rhel-8-x86_64-rpms\n- codeready-builder-for-rhel-8-x86_64-eus-rhui-rpms\n- codeready-builder-for-rhel-8-ppc64le-rpms', 'audience': 'sysadmin', 'key': '1b9132cb2362ae7830e48eee7811be9527747de8', 'id': 'df101d8c2318a3155aaddb9389b2770465b064eb7af40f1f1b2a95c3c324ac2c', 'severity': 'info'})
skipping: [192.168.122.113] => (item={'groups': ['repository'], 'title': 'Packages available in excluded repositories will not be installed', 'timeStamp': '2025-09-14T19:05:26.230023Z', 'hostname': 'db01.kifarunix.com', 'detail': {'related_resources': [{'scheme': 'package', 'title': 'python3-pyxattr'}, {'scheme': 'package', 'title': 'rpcgen'}]}, 'actor': 'pes_events_scanner', 'summary': '2 packages will be skipped because they are available only in target system repositories that are intentionally excluded from the list of repositories used during the upgrade. See the report message titled "Excluded target system repositories" for details.\nThe list of these packages:\n- python3-pyxattr (repoid: codeready-builder-for-rhel-8-x86_64-rpms)\n- rpcgen (repoid: codeready-builder-for-rhel-8-x86_64-rpms)', 'audience': 'sysadmin', 'key': '2437e204808f987477c0e9be8e4c95b3a87a9f3e', 'id': '180cbb8d679af19b3ce7bb52416361329fbdee530ef3908e7a5c80dcc326751a', 'severity': 'high'})
skipping: [192.168.122.113] => (item={'groups': ['services', 'email'], 'title': 'Postfix has incompatible changes in the next major version', 'timeStamp': '2025-09-14T19:05:28.915211Z', 'hostname': 'db01.kifarunix.com', 'detail': {'related_resources': [{'scheme': 'package', 'title': 'postfix'}]}, 'actor': 'check_postfix', 'summary': 'Postfix 3.x has so called "compatibility safety net" that runs Postfix programs with backwards-compatible default settings. It will log a warning whenever backwards-compatible default setting may be required for continuity of service. Based on this logging the system administrator can decide if any backwards-compatible settings need to be made permanent in main.cf or master.cf, before turning off the backwards-compatibility safety net.\nThe backward compatibility safety net is by default turned off in Red Hat Enterprise Linux 8.\nIt can be turned on by running: "postconf -e compatibility_level=0\nIt can be turned off by running: "postconf -e compatibility_level=2\n\nIn the Postfix MySQL database client, the default "option_group" value has changed to "client", i.e. it now reads options from the [client] group from the MySQL configuration file. To disable it, set "option_group" to the empty string.\n\nThe postqueue command no longer forces all message arrival times to be reported in UTC. To get the old behavior, set TZ=UTC in main.cf:import_environment.\n\nPostfix 3.2 enables elliptic curve negotiation. This changes the default smtpd_tls_eecdh_grade setting to "auto", and introduces a new parameter "tls_eecdh_auto_curves" with the names of curves that may be negotiated.\n\nThe "master.cf" chroot default value has changed from "y" (yes) to "n" (no). This applies to master.cf services where chroot field is not explicitly specified.\n\nThe "append_dot_mydomain" default value has changed from "yes" to "no". You may need changing it to "yes" if senders cannot use complete domain names in e-mail addresses.\n\nThe "relay_domains" default value has changed from "$mydestination" to the empty value. This could result in unexpected "Relay access denied" errors or ETRN errors, because now will postfix by default relay only for the localhost.\n\nThe "mynetworks_style" default value has changed from "subnet" to "host". This parameter is used to implement the "permit_mynetworks" feature. The change could result in unexpected "access denied" errors, because postfix will now by default trust only the local machine, not the remote SMTP clients on the same IP subnetwork.\n\nPostfix now supports dynamically loaded database plugins. Plugins are shipped in individual RPM sub-packages. Correct database plugins have to be installed, otherwise the specific database client will not work. For example for PostgreSQL map to work, the postfix-pgsql RPM package has to be installed.\n', 'audience': 'sysadmin', 'key': '5721e0a07a67d82cf7e5ea6f17662cd4f82e0a33', 'id': '458db741f010f9f794baaade24bd1dbb0c148582cba09d101ede50e8631036bd', 'severity': 'low'})
skipping: [192.168.122.113] => (item={'groups': ['authentication', 'security', 'tools'], 'title': 'Current PAM and nsswitch.conf configuration will be kept.', 'timeStamp': '2025-09-14T19:05:29.244997Z', 'hostname': 'db01.kifarunix.com', 'detail': {'related_resources': [{'scheme': 'package', 'title': 'authselect'}, {'scheme': 'package', 'title': 'authconfig'}, {'scheme': 'file', 'title': '/etc/nsswitch.conf'}]}, 'actor': 'authselect_check', 'summary': 'There is a new tool called authselect in RHEL8 that replaced authconfig. The upgrade process was unable to find an authselect profile that would be equivalent to your current configuration. Therefore your configuration will be left intact.', 'audience': 'sysadmin', 'key': '40c4ab1da4a30dc1ca40e543f6385e1336d8810c', 'id': 'be1cd7747e9b75de9fb3e3f312000bae551aeb4e3f3fefa81abd23c95173931e', 'severity': 'info'})
skipping: [192.168.122.113] => (item={'groups': ['selinux', 'security'], 'title': 'SElinux relabeling will be scheduled', 'timeStamp': '2025-09-14T19:05:29.846483Z', 'hostname': 'db01.kifarunix.com', 'actor': 'check_se_linux', 'summary': 'SElinux relabeling will be scheduled as the status is permissive/enforcing.', 'audience': 'sysadmin', 'key': '8fb81863f8413bd617c2a55b69b8e10ff03d7c72', 'id': '691e774f3d6024008baf68459dd0eae6fca877ee7080877f62156e5d199e6116', 'severity': 'info'})
skipping: [192.168.122.113] => (item={'groups': ['selinux', 'security'], 'title': 'SElinux will be set to permissive mode', 'timeStamp': '2025-09-14T19:05:29.849799Z', 'hostname': 'db01.kifarunix.com', 'detail': {'remediations': [{'type': 'hint', 'context': 'Make sure there are no SElinux related warnings after the upgrade and enable SElinux manually afterwards. Notice: You can ignore the "/root/tmp_leapp_py3" SElinux warnings.'}]}, 'actor': 'check_se_linux', 'summary': 'SElinux will be set to permissive mode. Current mode: enforcing. This action is required by the upgrade process to make sure the upgraded system can boot without beinig blocked by SElinux rules.', 'audience': 'sysadmin', 'key': '39d7183dafba798aa4bbb1e70b0ef2bbe5b1772f', 'id': '37c825a748e1ff17630f5fb5763a66d7d3d5b13e371fc92f781301356f2e61f4', 'severity': 'low'})
skipping: [192.168.122.113] => (item={'groups': ['tools'], 'title': 'Grep has incompatible changes in the next major version', 'timeStamp': '2025-09-14T19:05:30.037961Z', 'hostname': 'db01.kifarunix.com', 'detail': {'related_resources': [{'scheme': 'package', 'title': 'grep'}], 'remediations': [{'type': 'hint', 'context': 'Please update your scripts to be compatible with the changes.'}]}, 'actor': 'checkgrep', 'summary': 'If a file contains data improperly encoded for the current locale, and this is discovered before any of the file\'s contents are output, grep now treats the file as binary.\nThe \'grep -P\' no longer reports an error and exits when given invalid UTF-8 data. Instead, it considers the data to be non-matching.\nIn locales with multibyte character encodings other than UTF-8, grep -P now reports an error and exits instead of misbehaving.\nWhen searching binary data, grep now may treat non-text bytes as line terminators. This can boost performance significantly.\nThe \'grep -z\' no longer automatically treats the byte \'\\200\' as binary data.\nContext no longer excludes selected lines omitted because of -m. For example, \'grep "^" -m1 -A1\' now outputs the first two input lines, not just the first line.\n', 'audience': 'sysadmin', 'key': '94665a499e2eeee35eca3e7093a7abe183384b16', 'id': '784d95461b6f29da836440f95e2a32c8a62f08f19539cee7c3a37d3e0eeb9a10', 'severity': 'low'})
skipping: [192.168.122.113] => (item={'groups': ['services', 'time management'], 'title': 'chrony using default configuration', 'timeStamp': '2025-09-14T19:05:31.352819Z', 'hostname': 'db01.kifarunix.com', 'detail': {'related_resources': [{'scheme': 'package', 'title': 'ntpd'}, {'scheme': 'package', 'title': 'chrony'}, {'scheme': 'file', 'title': '/etc/chrony.conf'}]}, 'actor': 'check_chrony', 'summary': 'default chrony configuration in RHEL8 uses leapsectz directive, which cannot be used with leap smearing NTP servers, and uses a single pool directive instead of four server directives', 'audience': 'sysadmin', 'key': 'c4222ebd18730a76f6bc7b3b66df898b106e6554', 'id': '871c92c073d90f50aeb7eca8823feef633757cae1a37bbcf454fe87a45e7e7ab', 'severity': 'medium'})
skipping: [192.168.122.113] => (item={'groups': ['services'], 'title': 'Automatic registration into Red Hat Insights', 'timeStamp': '2025-09-14T19:05:31.657640Z', 'hostname': 'db01.kifarunix.com', 'actor': 'check_insights_auto_register', 'summary': "After the upgrade, this system will be automatically registered into Red Hat Insights. The 'insights-client' package required for the registration will be installed during the upgrade. To skip the automatic registration, use the '--no-insights-register' command line option or set the LEAPP_NO_INSIGHTS_REGISTER environment variable.", 'audience': 'sysadmin', 'key': '693963253195f418526f045b6d630a1f4c7a193d', 'id': '01e8e642f1919afeb175f21ae47f2806848d7971fe8970e5248124f896596f95', 'severity': 'info'})
skipping: [192.168.122.113] => (item={'groups': ['authentication', 'security', 'tools'], 'title': 'Module pam_pkcs11 will be removed from PAM configuration', 'timeStamp': '2025-09-14T19:05:31.703394Z', 'hostname': 'db01.kifarunix.com', 'detail': {'related_resources': [{'scheme': 'package', 'title': 'sssd'}], 'remediations': [{'type': 'hint', 'context': 'Configure SSSD to replace pam_pkcs11'}]}, 'actor': 'removed_pam_modules_check', 'summary': 'Module pam_pkcs11 was surpassed by SSSD and therefore it was removed from RHEL-8. Keeping it in PAM configuration may lock out the system thus it will be automatically removed from PAM configuration before upgrading to RHEL-8. Please switch to SSSD to recover the functionality of pam_pkcs11.', 'audience': 'sysadmin', 'key': 'bf47e7305d6805e8bbeaa7593cf01e38030c23f3', 'id': 'b9e5d0ac7d1a88b226abf1a17ce7ee777e87d1cb6cd207b1bd09d22443640015', 'severity': 'medium'})
skipping: [192.168.122.113] => (item={'groups': ['sanity'], 'title': 'Packages not signed by Red Hat found on the system', 'timeStamp': '2025-09-14T19:05:31.975841Z', 'hostname': 'db01.kifarunix.com', 'actor': 'red_hat_signed_rpm_check', 'summary': 'The following packages have not been signed by Red Hat and may be removed during the upgrade process in case Red Hat-signed packages to be removed during the upgrade depend on them:\n- containerd.io\n- docker-buildx-plugin\n- docker-ce\n- docker-ce-cli\n- docker-ce-rootless-extras\n- docker-compose-plugin\n- fuse-overlayfs\n- fuse3-libs\n- slirp4netns', 'audience': 'sysadmin', 'key': '13f0791ae5f19f50e7d0d606fb6501f91b1efb2c', 'id': 'c6e9383c684ff011c5ba35c316ef8f372129868bd4c6c53f32b5f2ee79707dbe', 'severity': 'high'})
skipping: [192.168.122.113] => (item={'groups': ['python'], 'title': 'Difference in Python versions and support in RHEL 8', 'timeStamp': '2025-09-14T19:05:32.383202Z', 'hostname': 'db01.kifarunix.com', 'detail': {'related_resources': [{'scheme': 'package', 'title': 'python'}, {'scheme': 'package', 'title': 'python2'}, {'scheme': 'package', 'title': 'python3'}], 'external': [{'url': 'https://red.ht/rhel-8-python', 'title': 'Difference in Python versions and support in RHEL 8'}], 'remediations': [{'type': 'hint', 'context': 'Please run "alternatives --set python /usr/bin/python3" after upgrade'}]}, 'actor': 'python_inform_user', 'summary': "In RHEL 8, there is no 'python' command. Python 3 (backward incompatible) is the primary Python version and Python 2 is available with limited support and limited set of packages. If you no longer require Python 2 packages following the upgrade, please remove them. Read more here: https://red.ht/rhel-8-python", 'audience': 'developer', 'key': '0c98585b1d8d252eb540bf61560094f3495351f5', 'id': '3d0d02f72396ff7fd871e7609413b84443ce2ca9bd21b1f27856e80ed5720a05', 'severity': 'high'})
skipping: [192.168.122.113] => (item={'groups': ['boot'], 'title': 'GRUB2 core will be automatically updated during the upgrade', 'timeStamp': '2025-09-14T19:05:33.027098Z', 'hostname': 'db01.kifarunix.com', 'actor': 'check_grub_core', 'summary': 'On legacy (BIOS) systems, GRUB2 core (located in the gap between the MBR and the first partition) cannot be updated during the rpm transaction and Leapp has to initiate the update running "grub2-install" after the transaction. No action is needed before the upgrade. After the upgrade, it is recommended to check the GRUB configuration.', 'audience': 'sysadmin', 'key': 'ac7030e05d2ee248d34f08a9fa040b352bc410a3', 'id': '4a78ee397dc2f8eb59f229f79f925774f9ca6b3b8294af2d037fcf471582307e', 'severity': 'high'})
TASK [infra.leapp.parse_leapp_report : Collect inhibitors] ***************************************************************************************************************************************************
ok: [192.168.122.113]
TASK [infra.leapp.parse_leapp_report : Collect high errors] **************************************************************************************************************************************************
ok: [192.168.122.113]
TASK [infra.leapp.analysis : Set stats for leapp_inhibitors] *************************************************************************************************************************************************
ok: [192.168.122.113]
TASK [infra.leapp.analysis : Notify analysis report is done handler] *****************************************************************************************************************************************
changed: [192.168.122.113]
RUNNING HANDLER [infra.leapp.common : Add end time to log file] **********************************************************************************************************************************************
changed: [192.168.122.113]
RUNNING HANDLER [infra.leapp.common : Slurp ripu.log file] ***************************************************************************************************************************************************
ok: [192.168.122.113]
RUNNING HANDLER [infra.leapp.common : Decode ripu.log file] **************************************************************************************************************************************************
ok: [192.168.122.113]
RUNNING HANDLER [infra.leapp.common : Rename log file] *******************************************************************************************************************************************************
changed: [192.168.122.113]
RUNNING HANDLER [infra.leapp.analysis : Register to pre leapp activation key] ********************************************************************************************************************************
skipping: [192.168.122.113]
RUNNING HANDLER [infra.leapp.analysis : Display inhibitors] **************************************************************************************************************************************************
ok: [192.168.122.113] => {
"results_inhibitors.stdout_lines": [
"Risk Factor: high (inhibitor)",
"Title: Unsupported network configuration",
"Summary: Detected multiple physical network interfaces where one or more use kernel naming (e.g. eth0). Upgrade process can not continue because stability of names can not be guaranteed. Please read the article at https://access.redhat.com/solutions/4067471 for more information.",
"Related links:",
" - How to perform an in-place upgrade to RHEL 8 when using kernel NIC names on RHEL 7: https://access.redhat.com/solutions/4067471",
" - RHEL 8 to RHEL 9: inplace upgrade fails at \"Network configuration for unsupported device types detected\": https://access.redhat.com/solutions/7009239",
"Remediation: [hint] Rename all ethX network interfaces following the attached KB solution article.",
"Key: d3050d265759a79ce895e64f45e9c56e49b3a953",
"----------------------------------------"
]
}
RUNNING HANDLER [infra.leapp.analysis : Display errors] ******************************************************************************************************************************************************
skipping: [192.168.122.113]
RUNNING HANDLER [infra.leapp.analysis : Preupgrade analysis report is done] **********************************************************************************************************************************
ok: [192.168.122.113] => {
"msg": "The preupgrade analysis report generation is now complete. WARNING: Inhibitors found. Review the tasks above or the result file at /var/log/leapp/leapp-report.txt."
}
ASYNC OK on 192.168.122.115: jid=j836712890705.9679
TASK [infra.leapp.analysis : analysis-leapp | Leapp preupgrade report] ***************************************************************************************************************************************
changed: [192.168.122.115]
TASK [analysis-leapp | Include custom_local_repos for local_repos_post_analysis] *****************************************************************************************************************************
skipping: [192.168.122.115]
TASK [infra.leapp.analysis : analysis-leapp | Include check-results-file.yml] ********************************************************************************************************************************
included: /home/kifarunix/.ansible/collections/ansible_collections/infra/leapp/roles/analysis/tasks/check-results-file.yml for 192.168.122.115
TASK [infra.leapp.analysis : check-results-file | Result file status] ****************************************************************************************************************************************
ok: [192.168.122.115]
TASK [infra.leapp.analysis : check-results-file | Check that result file exists] *****************************************************************************************************************************
ok: [192.168.122.115] => {
"changed": false,
"msg": "All assertions passed"
}
TASK [analysis-leapp | Include the parse_leapp_report role to check for inhibitors] **************************************************************************************************************************
TASK [infra.leapp.parse_leapp_report : Default upgrade_inhibited to false] ***********************************************************************************************************************************
ok: [192.168.122.115]
TASK [infra.leapp.parse_leapp_report : Collect human readable report results] ********************************************************************************************************************************
ok: [192.168.122.115]
TASK [infra.leapp.parse_leapp_report : Collect JSON report results] ******************************************************************************************************************************************
ok: [192.168.122.115]
TASK [infra.leapp.parse_leapp_report : Parse report results] *************************************************************************************************************************************************
ok: [192.168.122.115]
TASK [infra.leapp.parse_leapp_report : Check for inhibitors] *************************************************************************************************************************************************
skipping: [192.168.122.115] => (item={'audience': 'sysadmin', 'detail': {'remediations': [{'context': 'If some of excluded repositories are still required to be used during the upgrade, execute leapp with the --enablerepo option with the repoid of the repository required to be enabled as an argument (the option can be used multiple times).', 'type': 'hint'}]}, 'groups': ['repository', 'failure'], 'key': '1b9132cb2362ae7830e48eee7811be9527747de8', 'severity': 'info', 'summary': 'The following repositories are not supported by Red Hat and are excluded from the list of repositories used during the upgrade.\n- codeready-builder-beta-for-rhel-10-aarch64-rpms\n- codeready-builder-beta-for-rhel-10-s390x-rpms\n- codeready-builder-beta-for-rhel-10-x86_64-rpms\n- codeready-builder-for-rhel-10-ppc64le-rpms\n- codeready-builder-for-rhel-10-x86_64-rpms\n- codeready-builder-for-rhel-10-s390x-rpms\n- codeready-builder-for-rhel-10-aarch64-rpms\n- codeready-builder-beta-for-rhel-10-ppc64le-rpms', 'title': 'Excluded target system repositories', 'timeStamp': '2025-09-14T19:04:57.308998Z', 'hostname': 'lb01.kifarunix.com', 'actor': 'repositories_blacklist', 'id': '94cb08515dd797e3824939aafcd44322253d77bda9563cb60936db9a17e3b0f4'})
skipping: [192.168.122.115] => (item={'audience': 'sysadmin', 'groups': ['kernel', 'drivers'], 'key': 'fbb11ae5828d624c4e4c91e73d766c8e27b066d9', 'severity': 'high', 'summary': 'The following RHEL 9 device drivers are no longer maintained RHEL 10:\n - ip_set\n', 'title': 'Leapp detected loaded kernel drivers which are no longer maintained in RHEL 10.', 'timeStamp': '2025-09-14T19:04:58.449749Z', 'hostname': 'lb01.kifarunix.com', 'actor': 'check_detected_devices_and_drivers', 'id': 'ddf847575c9a0f4eb44a6b8a19aedbf3d5cebd20e46a26ce28f125c9f669844d'})
skipping: [192.168.122.115] => (item={'audience': 'sysadmin', 'groups': ['selinux', 'security'], 'key': '8fb81863f8413bd617c2a55b69b8e10ff03d7c72', 'severity': 'info', 'summary': 'SElinux relabeling will be scheduled as the status is permissive/enforcing.', 'title': 'SElinux relabeling will be scheduled', 'timeStamp': '2025-09-14T19:04:59.028065Z', 'hostname': 'lb01.kifarunix.com', 'actor': 'check_se_linux', 'id': '54dfab25f907a9d4bea10bf9461e53638e906d473b5808fbe6ef6057331d9e7b'})
skipping: [192.168.122.115] => (item={'audience': 'sysadmin', 'detail': {'remediations': [{'context': 'Make sure there are no SElinux related warnings after the upgrade and enable SElinux manually afterwards. Notice: You can ignore the "/root/tmp_leapp_py3" SElinux warnings.', 'type': 'hint'}]}, 'groups': ['selinux', 'security'], 'key': '39d7183dafba798aa4bbb1e70b0ef2bbe5b1772f', 'severity': 'low', 'summary': 'SElinux will be set to permissive mode. Current mode: enforcing. This action is required by the upgrade process to make sure the upgraded system can boot without beinig blocked by SElinux rules.', 'title': 'SElinux will be set to permissive mode', 'timeStamp': '2025-09-14T19:04:59.030734Z', 'hostname': 'lb01.kifarunix.com', 'actor': 'check_se_linux', 'id': '1ca609e1e14e87602f941729ee1d3ba56f34982b8e8ce7c934bbb68a47481bb2'})
skipping: [192.168.122.115] => (item={'audience': 'sysadmin', 'detail': {'external': [{'title': 'Migrating to a RHEL 10 without libdb', 'url': 'https://access.redhat.com/articles/7099256'}], 'related_resources': [{'scheme': 'package', 'title': 'libdb'}], 'remediations': [{'context': 'Back up your data before proceeding with the data upgrade/migration. For the conversion, the tool db_converter from the libdb-utils rpm could be used. This database format conversion must be performed before the system upgrade. The db_converter is not available in RHEL 10 systems. For more information, see the provided article.', 'type': 'hint'}]}, 'groups': ['services'], 'key': 'fdc8f5b084e95922a4f59485a807a92cae2fc738', 'severity': 'medium', 'summary': 'Libdb was marked as deprecated in RHEL-9 and in RHEL-10 is not included anymore. There are a couple of alternatives in RHEL-10; the applications that depend on libdb will not work. Such applications must implement another type of backend storage. And migrate existing data to the new database format.', 'title': 'Berkeley DB (libdb) has been detected on your system', 'timeStamp': '2025-09-14T19:04:59.229329Z', 'hostname': 'lb01.kifarunix.com', 'actor': 'libdb_check', 'id': 'f2a126c7bdce24bbb8031837dc463f131b0eb2736e639166a57da88d3028bccc'})
skipping: [192.168.122.115] => (item={'audience': 'sysadmin', 'groups': ['boot'], 'key': 'ac7030e05d2ee248d34f08a9fa040b352bc410a3', 'severity': 'high', 'summary': 'On legacy (BIOS) systems, GRUB2 core (located in the gap between the MBR and the first partition) cannot be updated during the rpm transaction and Leapp has to initiate the update running "grub2-install" after the transaction. No action is needed before the upgrade. After the upgrade, it is recommended to check the GRUB configuration.', 'title': 'GRUB2 core will be automatically updated during the upgrade', 'timeStamp': '2025-09-14T19:05:00.125578Z', 'hostname': 'lb01.kifarunix.com', 'actor': 'check_grub_core', 'id': '5613d43f82bf326a4e990921b24cc01530cc9dba95aacb7a4b35b70ebcfe40a3'})
skipping: [192.168.122.115] => (item={'audience': 'sysadmin', 'groups': ['services'], 'key': '693963253195f418526f045b6d630a1f4c7a193d', 'severity': 'info', 'summary': "After the upgrade, this system will be automatically registered into Red Hat Insights. To skip the automatic registration, use the '--no-insights-register' command line option or set the LEAPP_NO_INSIGHTS_REGISTER environment variable.", 'title': 'Automatic registration into Red Hat Insights', 'timeStamp': '2025-09-14T19:05:00.441653Z', 'hostname': 'lb01.kifarunix.com', 'actor': 'check_insights_auto_register', 'id': 'b41968c7998227420b259fd9d04966ad28a9322bc3ba3a9c9fa4ae84c049a531'})
skipping: [192.168.122.115] => (item={'audience': 'sysadmin', 'detail': {'related_resources': [{'scheme': 'package', 'title': 'subscription-manager'}], 'remediations': [{'context': 'If you wish to receive updates for the latest released version of the target system, run `subscription-manager release --unset` after the upgrade.', 'type': 'hint'}]}, 'groups': ['upgrade process'], 'key': '747a4ca25303eda17d1891bb85eeb226be14f252', 'severity': 'low', 'summary': 'After the upgrade has completed the release of the subscription-manager will be set to 10.0. This will ensure that you will receive and keep the version you choose to upgrade to.', 'title': 'The subscription-manager release is going to be set after the upgrade', 'timeStamp': '2025-09-14T19:06:39.027540Z', 'hostname': 'lb01.kifarunix.com', 'actor': 'report_set_target_release', 'id': 'f7aadf3f8580b7bc6a4bcc79b86342a8ac043114e10d060222378c04a6221e1b'})
skipping: [192.168.122.115]
TASK [infra.leapp.parse_leapp_report : Collect inhibitors] ***************************************************************************************************************************************************
ok: [192.168.122.115]
TASK [infra.leapp.parse_leapp_report : Collect high errors] **************************************************************************************************************************************************
ok: [192.168.122.115]
TASK [infra.leapp.analysis : Set stats for leapp_inhibitors] *************************************************************************************************************************************************
ok: [192.168.122.115]
TASK [infra.leapp.analysis : Notify analysis report is done handler] *****************************************************************************************************************************************
changed: [192.168.122.115]
RUNNING HANDLER [infra.leapp.common : Add end time to log file] **********************************************************************************************************************************************
changed: [192.168.122.115]
RUNNING HANDLER [infra.leapp.common : Slurp ripu.log file] ***************************************************************************************************************************************************
ok: [192.168.122.115]
RUNNING HANDLER [infra.leapp.common : Decode ripu.log file] **************************************************************************************************************************************************
ok: [192.168.122.115]
RUNNING HANDLER [infra.leapp.common : Rename log file] *******************************************************************************************************************************************************
changed: [192.168.122.115]
RUNNING HANDLER [infra.leapp.analysis : Register to pre leapp activation key] ********************************************************************************************************************************
skipping: [192.168.122.115]
RUNNING HANDLER [infra.leapp.analysis : Display inhibitors] **************************************************************************************************************************************************
skipping: [192.168.122.115]
RUNNING HANDLER [infra.leapp.analysis : Display errors] ******************************************************************************************************************************************************
skipping: [192.168.122.115]
RUNNING HANDLER [infra.leapp.analysis : Preupgrade analysis report is done] **********************************************************************************************************************************
ok: [192.168.122.115] => {
"msg": "The preupgrade analysis report generation is now complete. SUCCESS: No inhibitors found. Review the tasks above or the result file at /var/log/leapp/leapp-report.txt."
}
PLAY RECAP ***************************************************************************************************************************************************************************************************
192.168.122.113 : ok=34 changed=9 unreachable=0 failed=0 skipped=9 rescued=0 ignored=0
192.168.122.114 : ok=34 changed=8 unreachable=0 failed=0 skipped=9 rescued=0 ignored=0
192.168.122.115 : ok=32 changed=9 unreachable=0 failed=0 skipped=11 rescued=0 ignored=0
3. System Remediation
The remediation step utilizes the infra.leapp remediate role to automatically resolve common inhibitors and configuration conflicts discovered during the analysis phase.
This is the step where you would login to every server and fix identified pre-upgrade errors and inhibitors.
ansible-playbook -i inventory/rhel playbooks/remediate.ymlSample output;
PLAY [Remediate] *********************************************************************************************************************************************************************************************
TASK [Gathering Facts] ***************************************************************************************************************************************************************************************
ok: [192.168.122.115]
TASK [infra.leapp.remediate : Check if the system is RHEL 7 or 8 or 9] ***************************************************************************************************************************************
ok: [192.168.122.115] => {
"changed": false,
"msg": "All assertions passed"
}
TASK [Gathering Facts] ***************************************************************************************************************************************************************************************
ok: [192.168.122.114]
TASK [infra.leapp.remediate : Remediate the system] **********************************************************************************************************************************************************
skipping: [192.168.122.115] => (item=leapp_cifs_detected)
skipping: [192.168.122.115] => (item=leapp_corrupted_grubenv_file)
skipping: [192.168.122.115] => (item=leapp_deprecated_sshd_directive)
skipping: [192.168.122.115] => (item=leapp_firewalld_unsupported_tftp_client)
skipping: [192.168.122.115] => (item=leapp_loaded_removed_kernel_drivers)
skipping: [192.168.122.115] => (item=leapp_missing_efibootmgr)
skipping: [192.168.122.115] => (item=leapp_missing_yum_plugins)
skipping: [192.168.122.115] => (item=leapp_multiple_kernels)
skipping: [192.168.122.115] => (item=leapp_newest_kernel_not_in_use)
skipping: [192.168.122.115] => (item=leapp_non_persistent_partitions)
skipping: [192.168.122.115] => (item=leapp_non_standard_openssl_config)
skipping: [192.168.122.115] => (item=leapp_old_postgresql_data)
skipping: [192.168.122.115] => (item=leapp_pam_tally2)
skipping: [192.168.122.115] => (item=leapp_relative_symlinks)
skipping: [192.168.122.115] => (item=leapp_unavailable_kde)
included: /home/kifarunix/.ansible/collections/ansible_collections/infra/leapp/roles/remediate/tasks/leapp_custom_network_scripts_detected.yml for 192.168.122.115 => (item=leapp_custom_network_scripts_detected)
included: /home/kifarunix/.ansible/collections/ansible_collections/infra/leapp/roles/remediate/tasks/leapp_firewalld_allowzonedrifting.yml for 192.168.122.115 => (item=leapp_firewalld_allowzonedrifting)
included: /home/kifarunix/.ansible/collections/ansible_collections/infra/leapp/roles/remediate/tasks/leapp_missing_pkg.yml for 192.168.122.115 => (item=leapp_missing_pkg)
included: /home/kifarunix/.ansible/collections/ansible_collections/infra/leapp/roles/remediate/tasks/leapp_nfs_detected.yml for 192.168.122.115 => (item=leapp_nfs_detected)
included: /home/kifarunix/.ansible/collections/ansible_collections/infra/leapp/roles/remediate/tasks/leapp_partitions_with_noexec.yml for 192.168.122.115 => (item=leapp_partitions_with_noexec)
included: /home/kifarunix/.ansible/collections/ansible_collections/infra/leapp/roles/remediate/tasks/leapp_remote_using_root.yml for 192.168.122.115 => (item=leapp_remote_using_root)
included: /home/kifarunix/.ansible/collections/ansible_collections/infra/leapp/roles/remediate/tasks/leapp_rpms_with_rsa_sha1_detected.yml for 192.168.122.115 => (item=leapp_rpms_with_rsa_sha1_detected)
included: /home/kifarunix/.ansible/collections/ansible_collections/infra/leapp/roles/remediate/tasks/leapp_vdo_check_needed.yml for 192.168.122.115 => (item=leapp_vdo_check_needed)
included: /home/kifarunix/.ansible/collections/ansible_collections/infra/leapp/roles/remediate/tasks/leapp_unsupported_network_configuration.yml for 192.168.122.115 => (item=leapp_unsupported_network_configuration)
TASK [infra.leapp.remediate : Check if the system is RHEL 7 or 8 or 9] ***************************************************************************************************************************************
ok: [192.168.122.114] => {
"changed": false,
"msg": "All assertions passed"
}
TASK [infra.leapp.remediate : Remediate the system] **********************************************************************************************************************************************************
skipping: [192.168.122.114] => (item=leapp_cifs_detected)
skipping: [192.168.122.114] => (item=leapp_corrupted_grubenv_file)
TASK [infra.leapp.remediate : leapp_custom_network_scripts_detected | Check if pre up script exists] *********************************************************************************************************
skipping: [192.168.122.115]
TASK [infra.leapp.remediate : Remediate the system] **********************************************************************************************************************************************************
skipping: [192.168.122.114] => (item=leapp_deprecated_sshd_directive)
skipping: [192.168.122.114] => (item=leapp_firewalld_unsupported_tftp_client)
skipping: [192.168.122.114] => (item=leapp_loaded_removed_kernel_drivers)
skipping: [192.168.122.114] => (item=leapp_missing_efibootmgr)
skipping: [192.168.122.114] => (item=leapp_missing_yum_plugins)
skipping: [192.168.122.114] => (item=leapp_multiple_kernels)
skipping: [192.168.122.114] => (item=leapp_newest_kernel_not_in_use)
skipping: [192.168.122.114] => (item=leapp_non_persistent_partitions)
skipping: [192.168.122.114] => (item=leapp_non_standard_openssl_config)
skipping: [192.168.122.114] => (item=leapp_old_postgresql_data)
skipping: [192.168.122.114] => (item=leapp_pam_tally2)
skipping: [192.168.122.114] => (item=leapp_relative_symlinks)
skipping: [192.168.122.114] => (item=leapp_unavailable_kde)
TASK [infra.leapp.remediate : leapp_custom_network_scripts_detected | Check if pre down script exists] *******************************************************************************************************
skipping: [192.168.122.115]
TASK [infra.leapp.remediate : Remediate the system] **********************************************************************************************************************************************************
included: /home/kifarunix/.ansible/collections/ansible_collections/infra/leapp/roles/remediate/tasks/leapp_custom_network_scripts_detected.yml for 192.168.122.114 => (item=leapp_custom_network_scripts_detected)
included: /home/kifarunix/.ansible/collections/ansible_collections/infra/leapp/roles/remediate/tasks/leapp_firewalld_allowzonedrifting.yml for 192.168.122.114 => (item=leapp_firewalld_allowzonedrifting)
included: /home/kifarunix/.ansible/collections/ansible_collections/infra/leapp/roles/remediate/tasks/leapp_missing_pkg.yml for 192.168.122.114 => (item=leapp_missing_pkg)
included: /home/kifarunix/.ansible/collections/ansible_collections/infra/leapp/roles/remediate/tasks/leapp_nfs_detected.yml for 192.168.122.114 => (item=leapp_nfs_detected)
included: /home/kifarunix/.ansible/collections/ansible_collections/infra/leapp/roles/remediate/tasks/leapp_partitions_with_noexec.yml for 192.168.122.114 => (item=leapp_partitions_with_noexec)
included: /home/kifarunix/.ansible/collections/ansible_collections/infra/leapp/roles/remediate/tasks/leapp_remote_using_root.yml for 192.168.122.114 => (item=leapp_remote_using_root)
included: /home/kifarunix/.ansible/collections/ansible_collections/infra/leapp/roles/remediate/tasks/leapp_rpms_with_rsa_sha1_detected.yml for 192.168.122.114 => (item=leapp_rpms_with_rsa_sha1_detected)
included: /home/kifarunix/.ansible/collections/ansible_collections/infra/leapp/roles/remediate/tasks/leapp_vdo_check_needed.yml for 192.168.122.114 => (item=leapp_vdo_check_needed)
included: /home/kifarunix/.ansible/collections/ansible_collections/infra/leapp/roles/remediate/tasks/leapp_unsupported_network_configuration.yml for 192.168.122.114 => (item=leapp_unsupported_network_configuration)
TASK [Gathering Facts] ***************************************************************************************************************************************************************************************
ok: [192.168.122.113]
TASK [infra.leapp.remediate : leapp_custom_network_scripts_detected | Skip playbook if no custom scripts are found] ******************************************************************************************
skipping: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_custom_network_scripts_detected | Create /opt/network-scripts/ directory if it does not exist] ***************************************************************************
skipping: [192.168.122.115]
TASK [infra.leapp.remediate : Check if the system is RHEL 7 or 8 or 9] ***************************************************************************************************************************************
ok: [192.168.122.113] => {
"changed": false,
"msg": "All assertions passed"
}
TASK [infra.leapp.remediate : leapp_custom_network_scripts_detected | Move scripts in /sbin to /opt/network-scripts/, end playbook if this fails] ************************************************************
skipping: [192.168.122.115]
TASK [infra.leapp.remediate : Remediate the system] **********************************************************************************************************************************************************
skipping: [192.168.122.113] => (item=leapp_cifs_detected)
skipping: [192.168.122.113] => (item=leapp_corrupted_grubenv_file)
skipping: [192.168.122.113] => (item=leapp_deprecated_sshd_directive)
skipping: [192.168.122.113] => (item=leapp_firewalld_unsupported_tftp_client)
skipping: [192.168.122.113] => (item=leapp_loaded_removed_kernel_drivers)
skipping: [192.168.122.113] => (item=leapp_missing_efibootmgr)
skipping: [192.168.122.113] => (item=leapp_missing_yum_plugins)
skipping: [192.168.122.113] => (item=leapp_multiple_kernels)
skipping: [192.168.122.113] => (item=leapp_newest_kernel_not_in_use)
skipping: [192.168.122.113] => (item=leapp_non_persistent_partitions)
TASK [infra.leapp.remediate : leapp_custom_network_scripts_detected | Create /etc/NetworkManager/dispatcher.d/20-if-local] ***********************************************************************************
skipping: [192.168.122.115]
TASK [infra.leapp.remediate : Remediate the system] **********************************************************************************************************************************************************
skipping: [192.168.122.113] => (item=leapp_non_standard_openssl_config)
skipping: [192.168.122.113] => (item=leapp_old_postgresql_data)
skipping: [192.168.122.113] => (item=leapp_pam_tally2)
skipping: [192.168.122.113] => (item=leapp_relative_symlinks)
skipping: [192.168.122.113] => (item=leapp_unavailable_kde)
included: /home/kifarunix/.ansible/collections/ansible_collections/infra/leapp/roles/remediate/tasks/leapp_custom_network_scripts_detected.yml for 192.168.122.113 => (item=leapp_custom_network_scripts_detected)
included: /home/kifarunix/.ansible/collections/ansible_collections/infra/leapp/roles/remediate/tasks/leapp_firewalld_allowzonedrifting.yml for 192.168.122.113 => (item=leapp_firewalld_allowzonedrifting)
included: /home/kifarunix/.ansible/collections/ansible_collections/infra/leapp/roles/remediate/tasks/leapp_missing_pkg.yml for 192.168.122.113 => (item=leapp_missing_pkg)
included: /home/kifarunix/.ansible/collections/ansible_collections/infra/leapp/roles/remediate/tasks/leapp_nfs_detected.yml for 192.168.122.113 => (item=leapp_nfs_detected)
included: /home/kifarunix/.ansible/collections/ansible_collections/infra/leapp/roles/remediate/tasks/leapp_partitions_with_noexec.yml for 192.168.122.113 => (item=leapp_partitions_with_noexec)
included: /home/kifarunix/.ansible/collections/ansible_collections/infra/leapp/roles/remediate/tasks/leapp_remote_using_root.yml for 192.168.122.113 => (item=leapp_remote_using_root)
included: /home/kifarunix/.ansible/collections/ansible_collections/infra/leapp/roles/remediate/tasks/leapp_rpms_with_rsa_sha1_detected.yml for 192.168.122.113 => (item=leapp_rpms_with_rsa_sha1_detected)
included: /home/kifarunix/.ansible/collections/ansible_collections/infra/leapp/roles/remediate/tasks/leapp_vdo_check_needed.yml for 192.168.122.113 => (item=leapp_vdo_check_needed)
included: /home/kifarunix/.ansible/collections/ansible_collections/infra/leapp/roles/remediate/tasks/leapp_unsupported_network_configuration.yml for 192.168.122.113 => (item=leapp_unsupported_network_configuration)
TASK [infra.leapp.remediate : leapp_custom_network_scripts_detected | Set permissions on /etc/NetworkManager/dispatcher.d/20-if-local] ***********************************************************************
skipping: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_custom_network_scripts_detected | Check if pre up script exists] *********************************************************************************************************
skipping: [192.168.122.113]
TASK [infra.leapp.remediate : leapp_custom_network_scripts_detected | Restore SELinux context on /etc/NetworkManager/dispatcher.d/20-if-local] ***************************************************************
skipping: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_custom_network_scripts_detected | Check if pre down script exists] *******************************************************************************************************
skipping: [192.168.122.113]
TASK [infra.leapp.remediate : leapp_custom_network_scripts_detected | If pre up script exists, create symbolic link] *****************************************************************************************
skipping: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_custom_network_scripts_detected | Skip playbook if no custom scripts are found] ******************************************************************************************
skipping: [192.168.122.113]
TASK [infra.leapp.remediate : leapp_custom_network_scripts_detected | If pre down script exists, create symbolic link] ***************************************************************************************
skipping: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_custom_network_scripts_detected | Create /opt/network-scripts/ directory if it does not exist] ***************************************************************************
skipping: [192.168.122.113]
TASK [infra.leapp.remediate : leapp_firewalld_allowzonedrifting | Set the "AllowZoneDrifting" in firewalld.conf to "no"] *************************************************************************************
skipping: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_custom_network_scripts_detected | Move scripts in /sbin to /opt/network-scripts/, end playbook if this fails] ************************************************************
skipping: [192.168.122.113]
TASK [infra.leapp.remediate : leapp_custom_network_scripts_detected | Create /etc/NetworkManager/dispatcher.d/20-if-local] ***********************************************************************************
skipping: [192.168.122.113]
TASK [infra.leapp.remediate : leapp_custom_network_scripts_detected | Set permissions on /etc/NetworkManager/dispatcher.d/20-if-local] ***********************************************************************
skipping: [192.168.122.113]
TASK [infra.leapp.remediate : leapp_custom_network_scripts_detected | Restore SELinux context on /etc/NetworkManager/dispatcher.d/20-if-local] ***************************************************************
skipping: [192.168.122.113]
TASK [infra.leapp.remediate : leapp_custom_network_scripts_detected | If pre up script exists, create symbolic link] *****************************************************************************************
skipping: [192.168.122.113]
TASK [infra.leapp.remediate : leapp_custom_network_scripts_detected | Check if pre up script exists] *********************************************************************************************************
ok: [192.168.122.114]
TASK [infra.leapp.remediate : leapp_custom_network_scripts_detected | If pre down script exists, create symbolic link] ***************************************************************************************
skipping: [192.168.122.113]
TASK [infra.leapp.remediate : leapp_firewalld_allowzonedrifting | Set the "AllowZoneDrifting" in firewalld.conf to "no"] *************************************************************************************
skipping: [192.168.122.113]
TASK [infra.leapp.remediate : leapp_missing_pkg | Check that the leapp-report.json exists] *******************************************************************************************************************
ok: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_missing_pkg | End play if no leapp report exists] ************************************************************************************************************************
skipping: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_custom_network_scripts_detected | Check if pre down script exists] *******************************************************************************************************
ok: [192.168.122.114]
TASK [infra.leapp.remediate : leapp_custom_network_scripts_detected | Skip playbook if no custom scripts are found] ******************************************************************************************
fatal: [192.168.122.114]: FAILED! => {"ansible_facts": {"leapp_report_missing": true}, "changed": false, "failed_when_result": true}
TASK [infra.leapp.remediate : leapp_custom_network_scripts_detected | Continue when no custom scripts are found] *********************************************************************************************
skipping: [192.168.122.114]
TASK [infra.leapp.remediate : leapp_missing_pkg | Check that the leapp-report.json exists] *******************************************************************************************************************
ok: [192.168.122.113]
TASK [infra.leapp.remediate : leapp_missing_pkg | End play if no leapp report exists] ************************************************************************************************************************
skipping: [192.168.122.113]
TASK [infra.leapp.remediate : leapp_missing_pkg | Read leapp report] *****************************************************************************************************************************************
ok: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_missing_pkg | Parse leapp report to json] ********************************************************************************************************************************
ok: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_missing_pkg | Find matching entries] *************************************************************************************************************************************
skipping: [192.168.122.115] => (item={'audience': 'sysadmin', 'detail': {'remediations': [{'context': 'If some of excluded repositories are still required to be used during the upgrade, execute leapp with the --enablerepo option with the repoid of the repository required to be enabled as an argument (the option can be used multiple times).', 'type': 'hint'}]}, 'groups': ['repository', 'failure'], 'key': '1b9132cb2362ae7830e48eee7811be9527747de8', 'severity': 'info', 'summary': 'The following repositories are not supported by Red Hat and are excluded from the list of repositories used during the upgrade.\n- codeready-builder-beta-for-rhel-10-aarch64-rpms\n- codeready-builder-beta-for-rhel-10-s390x-rpms\n- codeready-builder-beta-for-rhel-10-x86_64-rpms\n- codeready-builder-for-rhel-10-ppc64le-rpms\n- codeready-builder-for-rhel-10-x86_64-rpms\n- codeready-builder-for-rhel-10-s390x-rpms\n- codeready-builder-for-rhel-10-aarch64-rpms\n- codeready-builder-beta-for-rhel-10-ppc64le-rpms', 'title': 'Excluded target system repositories', 'timeStamp': '2025-09-14T19:04:57.308998Z', 'hostname': 'lb01.kifarunix.com', 'actor': 'repositories_blacklist', 'id': '94cb08515dd797e3824939aafcd44322253d77bda9563cb60936db9a17e3b0f4'})
skipping: [192.168.122.115] => (item={'audience': 'sysadmin', 'groups': ['kernel', 'drivers'], 'key': 'fbb11ae5828d624c4e4c91e73d766c8e27b066d9', 'severity': 'high', 'summary': 'The following RHEL 9 device drivers are no longer maintained RHEL 10:\n - ip_set\n', 'title': 'Leapp detected loaded kernel drivers which are no longer maintained in RHEL 10.', 'timeStamp': '2025-09-14T19:04:58.449749Z', 'hostname': 'lb01.kifarunix.com', 'actor': 'check_detected_devices_and_drivers', 'id': 'ddf847575c9a0f4eb44a6b8a19aedbf3d5cebd20e46a26ce28f125c9f669844d'})
skipping: [192.168.122.115] => (item={'audience': 'sysadmin', 'groups': ['selinux', 'security'], 'key': '8fb81863f8413bd617c2a55b69b8e10ff03d7c72', 'severity': 'info', 'summary': 'SElinux relabeling will be scheduled as the status is permissive/enforcing.', 'title': 'SElinux relabeling will be scheduled', 'timeStamp': '2025-09-14T19:04:59.028065Z', 'hostname': 'lb01.kifarunix.com', 'actor': 'check_se_linux', 'id': '54dfab25f907a9d4bea10bf9461e53638e906d473b5808fbe6ef6057331d9e7b'})
skipping: [192.168.122.115] => (item={'audience': 'sysadmin', 'detail': {'remediations': [{'context': 'Make sure there are no SElinux related warnings after the upgrade and enable SElinux manually afterwards. Notice: You can ignore the "/root/tmp_leapp_py3" SElinux warnings.', 'type': 'hint'}]}, 'groups': ['selinux', 'security'], 'key': '39d7183dafba798aa4bbb1e70b0ef2bbe5b1772f', 'severity': 'low', 'summary': 'SElinux will be set to permissive mode. Current mode: enforcing. This action is required by the upgrade process to make sure the upgraded system can boot without beinig blocked by SElinux rules.', 'title': 'SElinux will be set to permissive mode', 'timeStamp': '2025-09-14T19:04:59.030734Z', 'hostname': 'lb01.kifarunix.com', 'actor': 'check_se_linux', 'id': '1ca609e1e14e87602f941729ee1d3ba56f34982b8e8ce7c934bbb68a47481bb2'})
skipping: [192.168.122.115] => (item={'audience': 'sysadmin', 'detail': {'external': [{'title': 'Migrating to a RHEL 10 without libdb', 'url': 'https://access.redhat.com/articles/7099256'}], 'related_resources': [{'scheme': 'package', 'title': 'libdb'}], 'remediations': [{'context': 'Back up your data before proceeding with the data upgrade/migration. For the conversion, the tool db_converter from the libdb-utils rpm could be used. This database format conversion must be performed before the system upgrade. The db_converter is not available in RHEL 10 systems. For more information, see the provided article.', 'type': 'hint'}]}, 'groups': ['services'], 'key': 'fdc8f5b084e95922a4f59485a807a92cae2fc738', 'severity': 'medium', 'summary': 'Libdb was marked as deprecated in RHEL-9 and in RHEL-10 is not included anymore. There are a couple of alternatives in RHEL-10; the applications that depend on libdb will not work. Such applications must implement another type of backend storage. And migrate existing data to the new database format.', 'title': 'Berkeley DB (libdb) has been detected on your system', 'timeStamp': '2025-09-14T19:04:59.229329Z', 'hostname': 'lb01.kifarunix.com', 'actor': 'libdb_check', 'id': 'f2a126c7bdce24bbb8031837dc463f131b0eb2736e639166a57da88d3028bccc'})
skipping: [192.168.122.115] => (item={'audience': 'sysadmin', 'groups': ['boot'], 'key': 'ac7030e05d2ee248d34f08a9fa040b352bc410a3', 'severity': 'high', 'summary': 'On legacy (BIOS) systems, GRUB2 core (located in the gap between the MBR and the first partition) cannot be updated during the rpm transaction and Leapp has to initiate the update running "grub2-install" after the transaction. No action is needed before the upgrade. After the upgrade, it is recommended to check the GRUB configuration.', 'title': 'GRUB2 core will be automatically updated during the upgrade', 'timeStamp': '2025-09-14T19:05:00.125578Z', 'hostname': 'lb01.kifarunix.com', 'actor': 'check_grub_core', 'id': '5613d43f82bf326a4e990921b24cc01530cc9dba95aacb7a4b35b70ebcfe40a3'})
skipping: [192.168.122.115] => (item={'audience': 'sysadmin', 'groups': ['services'], 'key': '693963253195f418526f045b6d630a1f4c7a193d', 'severity': 'info', 'summary': "After the upgrade, this system will be automatically registered into Red Hat Insights. To skip the automatic registration, use the '--no-insights-register' command line option or set the LEAPP_NO_INSIGHTS_REGISTER environment variable.", 'title': 'Automatic registration into Red Hat Insights', 'timeStamp': '2025-09-14T19:05:00.441653Z', 'hostname': 'lb01.kifarunix.com', 'actor': 'check_insights_auto_register', 'id': 'b41968c7998227420b259fd9d04966ad28a9322bc3ba3a9c9fa4ae84c049a531'})
skipping: [192.168.122.115] => (item={'audience': 'sysadmin', 'detail': {'related_resources': [{'scheme': 'package', 'title': 'subscription-manager'}], 'remediations': [{'context': 'If you wish to receive updates for the latest released version of the target system, run `subscription-manager release --unset` after the upgrade.', 'type': 'hint'}]}, 'groups': ['upgrade process'], 'key': '747a4ca25303eda17d1891bb85eeb226be14f252', 'severity': 'low', 'summary': 'After the upgrade has completed the release of the subscription-manager will be set to 10.0. This will ensure that you will receive and keep the version you choose to upgrade to.', 'title': 'The subscription-manager release is going to be set after the upgrade', 'timeStamp': '2025-09-14T19:06:39.027540Z', 'hostname': 'lb01.kifarunix.com', 'actor': 'report_set_target_release', 'id': 'f7aadf3f8580b7bc6a4bcc79b86342a8ac043114e10d060222378c04a6221e1b'})
skipping: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_missing_pkg | End execution of playbook if no entry found in leapp report] ***********************************************************************************************
fatal: [192.168.122.115]: FAILED! => {"ansible_facts": {"leapp_report_missing": true}, "changed": false, "failed_when_result": true}
TASK [infra.leapp.remediate : leapp_missing_pkg | Continue when leapp report is missing] *********************************************************************************************************************
skipping: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_firewalld_allowzonedrifting | Set the "AllowZoneDrifting" in firewalld.conf to "no"] *************************************************************************************
ok: [192.168.122.114]
TASK [infra.leapp.remediate : leapp_missing_pkg | Read leapp report] *****************************************************************************************************************************************
ok: [192.168.122.113]
TASK [infra.leapp.remediate : leapp_missing_pkg | Parse leapp report to json] ********************************************************************************************************************************
ok: [192.168.122.113]
TASK [infra.leapp.remediate : leapp_missing_pkg | Find matching entries] *************************************************************************************************************************************
skipping: [192.168.122.113] => (item={'groups': ['network', 'inhibitor'], 'title': 'Unsupported network configuration', 'timeStamp': '2025-09-14T19:05:16.373921Z', 'hostname': 'db01.kifarunix.com', 'detail': {'external': [{'url': 'https://access.redhat.com/solutions/4067471', 'title': 'How to perform an in-place upgrade to RHEL 8 when using kernel NIC names on RHEL 7'}, {'url': 'https://access.redhat.com/solutions/7009239', 'title': 'RHEL 8 to RHEL 9: inplace upgrade fails at "Network configuration for unsupported device types detected"'}], 'remediations': [{'type': 'hint', 'context': 'Rename all ethX network interfaces following the attached KB solution article.'}]}, 'actor': 'persistentnetnamesdisable', 'summary': 'Detected multiple physical network interfaces where one or more use kernel naming (e.g. eth0). Upgrade process can not continue because stability of names can not be guaranteed. Please read the article at https://access.redhat.com/solutions/4067471 for more information.', 'audience': 'sysadmin', 'key': 'd3050d265759a79ce895e64f45e9c56e49b3a953', 'id': '713dbc223571ebf608d752e56cf94c92846b0ccde9442bccf499d6dd11703ab0', 'severity': 'high'})
skipping: [192.168.122.113] => (item={'groups': ['repository', 'failure'], 'title': 'Excluded target system repositories', 'timeStamp': '2025-09-14T19:05:16.440845Z', 'hostname': 'db01.kifarunix.com', 'detail': {'remediations': [{'type': 'hint', 'context': 'If some of excluded repositories are still required to be used during the upgrade, execute leapp with the --enablerepo option with the repoid of the repository required to be enabled as an argument (the option can be used multiple times).'}]}, 'actor': 'repositories_blacklist', 'summary': 'The following repositories are not supported by Red Hat and are excluded from the list of repositories used during the upgrade.\n- codeready-builder-beta-for-rhel-8-s390x-rpms\n- codeready-builder-beta-for-rhel-8-ppc64le-rpms\n- rhui-codeready-builder-for-rhel-8-x86_64-rhui-rpms\n- codeready-builder-for-rhel-8-aarch64-eus-rpms\n- codeready-builder-for-rhel-8-ppc64le-eus-rpms\n- codeready-builder-beta-for-rhel-8-x86_64-rpms\n- codeready-builder-for-rhel-8-aarch64-rpms\n- codeready-builder-for-rhel-8-s390x-rpms\n- codeready-builder-for-rhel-8-s390x-eus-rpms\n- codeready-builder-for-rhel-8-x86_64-eus-rpms\n- rhui-codeready-builder-for-rhel-8-aarch64-rhui-rpms\n- codeready-builder-beta-for-rhel-8-aarch64-rpms\n- codeready-builder-for-rhel-8-rhui-rpms\n- codeready-builder-for-rhel-8-x86_64-rhui-rpms\n- codeready-builder-for-rhel-8-x86_64-rpms\n- codeready-builder-for-rhel-8-x86_64-eus-rhui-rpms\n- codeready-builder-for-rhel-8-ppc64le-rpms', 'audience': 'sysadmin', 'key': '1b9132cb2362ae7830e48eee7811be9527747de8', 'id': 'df101d8c2318a3155aaddb9389b2770465b064eb7af40f1f1b2a95c3c324ac2c', 'severity': 'info'})
skipping: [192.168.122.113] => (item={'groups': ['repository'], 'title': 'Packages available in excluded repositories will not be installed', 'timeStamp': '2025-09-14T19:05:26.230023Z', 'hostname': 'db01.kifarunix.com', 'detail': {'related_resources': [{'scheme': 'package', 'title': 'python3-pyxattr'}, {'scheme': 'package', 'title': 'rpcgen'}]}, 'actor': 'pes_events_scanner', 'summary': '2 packages will be skipped because they are available only in target system repositories that are intentionally excluded from the list of repositories used during the upgrade. See the report message titled "Excluded target system repositories" for details.\nThe list of these packages:\n- python3-pyxattr (repoid: codeready-builder-for-rhel-8-x86_64-rpms)\n- rpcgen (repoid: codeready-builder-for-rhel-8-x86_64-rpms)', 'audience': 'sysadmin', 'key': '2437e204808f987477c0e9be8e4c95b3a87a9f3e', 'id': '180cbb8d679af19b3ce7bb52416361329fbdee530ef3908e7a5c80dcc326751a', 'severity': 'high'})
skipping: [192.168.122.113] => (item={'groups': ['services', 'email'], 'title': 'Postfix has incompatible changes in the next major version', 'timeStamp': '2025-09-14T19:05:28.915211Z', 'hostname': 'db01.kifarunix.com', 'detail': {'related_resources': [{'scheme': 'package', 'title': 'postfix'}]}, 'actor': 'check_postfix', 'summary': 'Postfix 3.x has so called "compatibility safety net" that runs Postfix programs with backwards-compatible default settings. It will log a warning whenever backwards-compatible default setting may be required for continuity of service. Based on this logging the system administrator can decide if any backwards-compatible settings need to be made permanent in main.cf or master.cf, before turning off the backwards-compatibility safety net.\nThe backward compatibility safety net is by default turned off in Red Hat Enterprise Linux 8.\nIt can be turned on by running: "postconf -e compatibility_level=0\nIt can be turned off by running: "postconf -e compatibility_level=2\n\nIn the Postfix MySQL database client, the default "option_group" value has changed to "client", i.e. it now reads options from the [client] group from the MySQL configuration file. To disable it, set "option_group" to the empty string.\n\nThe postqueue command no longer forces all message arrival times to be reported in UTC. To get the old behavior, set TZ=UTC in main.cf:import_environment.\n\nPostfix 3.2 enables elliptic curve negotiation. This changes the default smtpd_tls_eecdh_grade setting to "auto", and introduces a new parameter "tls_eecdh_auto_curves" with the names of curves that may be negotiated.\n\nThe "master.cf" chroot default value has changed from "y" (yes) to "n" (no). This applies to master.cf services where chroot field is not explicitly specified.\n\nThe "append_dot_mydomain" default value has changed from "yes" to "no". You may need changing it to "yes" if senders cannot use complete domain names in e-mail addresses.\n\nThe "relay_domains" default value has changed from "$mydestination" to the empty value. This could result in unexpected "Relay access denied" errors or ETRN errors, because now will postfix by default relay only for the localhost.\n\nThe "mynetworks_style" default value has changed from "subnet" to "host". This parameter is used to implement the "permit_mynetworks" feature. The change could result in unexpected "access denied" errors, because postfix will now by default trust only the local machine, not the remote SMTP clients on the same IP subnetwork.\n\nPostfix now supports dynamically loaded database plugins. Plugins are shipped in individual RPM sub-packages. Correct database plugins have to be installed, otherwise the specific database client will not work. For example for PostgreSQL map to work, the postfix-pgsql RPM package has to be installed.\n', 'audience': 'sysadmin', 'key': '5721e0a07a67d82cf7e5ea6f17662cd4f82e0a33', 'id': '458db741f010f9f794baaade24bd1dbb0c148582cba09d101ede50e8631036bd', 'severity': 'low'})
skipping: [192.168.122.113] => (item={'groups': ['authentication', 'security', 'tools'], 'title': 'Current PAM and nsswitch.conf configuration will be kept.', 'timeStamp': '2025-09-14T19:05:29.244997Z', 'hostname': 'db01.kifarunix.com', 'detail': {'related_resources': [{'scheme': 'package', 'title': 'authselect'}, {'scheme': 'package', 'title': 'authconfig'}, {'scheme': 'file', 'title': '/etc/nsswitch.conf'}]}, 'actor': 'authselect_check', 'summary': 'There is a new tool called authselect in RHEL8 that replaced authconfig. The upgrade process was unable to find an authselect profile that would be equivalent to your current configuration. Therefore your configuration will be left intact.', 'audience': 'sysadmin', 'key': '40c4ab1da4a30dc1ca40e543f6385e1336d8810c', 'id': 'be1cd7747e9b75de9fb3e3f312000bae551aeb4e3f3fefa81abd23c95173931e', 'severity': 'info'})
skipping: [192.168.122.113] => (item={'groups': ['selinux', 'security'], 'title': 'SElinux relabeling will be scheduled', 'timeStamp': '2025-09-14T19:05:29.846483Z', 'hostname': 'db01.kifarunix.com', 'actor': 'check_se_linux', 'summary': 'SElinux relabeling will be scheduled as the status is permissive/enforcing.', 'audience': 'sysadmin', 'key': '8fb81863f8413bd617c2a55b69b8e10ff03d7c72', 'id': '691e774f3d6024008baf68459dd0eae6fca877ee7080877f62156e5d199e6116', 'severity': 'info'})
skipping: [192.168.122.113] => (item={'groups': ['selinux', 'security'], 'title': 'SElinux will be set to permissive mode', 'timeStamp': '2025-09-14T19:05:29.849799Z', 'hostname': 'db01.kifarunix.com', 'detail': {'remediations': [{'type': 'hint', 'context': 'Make sure there are no SElinux related warnings after the upgrade and enable SElinux manually afterwards. Notice: You can ignore the "/root/tmp_leapp_py3" SElinux warnings.'}]}, 'actor': 'check_se_linux', 'summary': 'SElinux will be set to permissive mode. Current mode: enforcing. This action is required by the upgrade process to make sure the upgraded system can boot without beinig blocked by SElinux rules.', 'audience': 'sysadmin', 'key': '39d7183dafba798aa4bbb1e70b0ef2bbe5b1772f', 'id': '37c825a748e1ff17630f5fb5763a66d7d3d5b13e371fc92f781301356f2e61f4', 'severity': 'low'})
skipping: [192.168.122.113] => (item={'groups': ['tools'], 'title': 'Grep has incompatible changes in the next major version', 'timeStamp': '2025-09-14T19:05:30.037961Z', 'hostname': 'db01.kifarunix.com', 'detail': {'related_resources': [{'scheme': 'package', 'title': 'grep'}], 'remediations': [{'type': 'hint', 'context': 'Please update your scripts to be compatible with the changes.'}]}, 'actor': 'checkgrep', 'summary': 'If a file contains data improperly encoded for the current locale, and this is discovered before any of the file\'s contents are output, grep now treats the file as binary.\nThe \'grep -P\' no longer reports an error and exits when given invalid UTF-8 data. Instead, it considers the data to be non-matching.\nIn locales with multibyte character encodings other than UTF-8, grep -P now reports an error and exits instead of misbehaving.\nWhen searching binary data, grep now may treat non-text bytes as line terminators. This can boost performance significantly.\nThe \'grep -z\' no longer automatically treats the byte \'\\200\' as binary data.\nContext no longer excludes selected lines omitted because of -m. For example, \'grep "^" -m1 -A1\' now outputs the first two input lines, not just the first line.\n', 'audience': 'sysadmin', 'key': '94665a499e2eeee35eca3e7093a7abe183384b16', 'id': '784d95461b6f29da836440f95e2a32c8a62f08f19539cee7c3a37d3e0eeb9a10', 'severity': 'low'})
skipping: [192.168.122.113] => (item={'groups': ['services', 'time management'], 'title': 'chrony using default configuration', 'timeStamp': '2025-09-14T19:05:31.352819Z', 'hostname': 'db01.kifarunix.com', 'detail': {'related_resources': [{'scheme': 'package', 'title': 'ntpd'}, {'scheme': 'package', 'title': 'chrony'}, {'scheme': 'file', 'title': '/etc/chrony.conf'}]}, 'actor': 'check_chrony', 'summary': 'default chrony configuration in RHEL8 uses leapsectz directive, which cannot be used with leap smearing NTP servers, and uses a single pool directive instead of four server directives', 'audience': 'sysadmin', 'key': 'c4222ebd18730a76f6bc7b3b66df898b106e6554', 'id': '871c92c073d90f50aeb7eca8823feef633757cae1a37bbcf454fe87a45e7e7ab', 'severity': 'medium'})
skipping: [192.168.122.113] => (item={'groups': ['services'], 'title': 'Automatic registration into Red Hat Insights', 'timeStamp': '2025-09-14T19:05:31.657640Z', 'hostname': 'db01.kifarunix.com', 'actor': 'check_insights_auto_register', 'summary': "After the upgrade, this system will be automatically registered into Red Hat Insights. The 'insights-client' package required for the registration will be installed during the upgrade. To skip the automatic registration, use the '--no-insights-register' command line option or set the LEAPP_NO_INSIGHTS_REGISTER environment variable.", 'audience': 'sysadmin', 'key': '693963253195f418526f045b6d630a1f4c7a193d', 'id': '01e8e642f1919afeb175f21ae47f2806848d7971fe8970e5248124f896596f95', 'severity': 'info'})
skipping: [192.168.122.113] => (item={'groups': ['authentication', 'security', 'tools'], 'title': 'Module pam_pkcs11 will be removed from PAM configuration', 'timeStamp': '2025-09-14T19:05:31.703394Z', 'hostname': 'db01.kifarunix.com', 'detail': {'related_resources': [{'scheme': 'package', 'title': 'sssd'}], 'remediations': [{'type': 'hint', 'context': 'Configure SSSD to replace pam_pkcs11'}]}, 'actor': 'removed_pam_modules_check', 'summary': 'Module pam_pkcs11 was surpassed by SSSD and therefore it was removed from RHEL-8. Keeping it in PAM configuration may lock out the system thus it will be automatically removed from PAM configuration before upgrading to RHEL-8. Please switch to SSSD to recover the functionality of pam_pkcs11.', 'audience': 'sysadmin', 'key': 'bf47e7305d6805e8bbeaa7593cf01e38030c23f3', 'id': 'b9e5d0ac7d1a88b226abf1a17ce7ee777e87d1cb6cd207b1bd09d22443640015', 'severity': 'medium'})
TASK [infra.leapp.remediate : leapp_nfs_detected | Check that the leapp-report.json exists] ******************************************************************************************************************
ok: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_missing_pkg | Find matching entries] *************************************************************************************************************************************
skipping: [192.168.122.113] => (item={'groups': ['sanity'], 'title': 'Packages not signed by Red Hat found on the system', 'timeStamp': '2025-09-14T19:05:31.975841Z', 'hostname': 'db01.kifarunix.com', 'actor': 'red_hat_signed_rpm_check', 'summary': 'The following packages have not been signed by Red Hat and may be removed during the upgrade process in case Red Hat-signed packages to be removed during the upgrade depend on them:\n- containerd.io\n- docker-buildx-plugin\n- docker-ce\n- docker-ce-cli\n- docker-ce-rootless-extras\n- docker-compose-plugin\n- fuse-overlayfs\n- fuse3-libs\n- slirp4netns', 'audience': 'sysadmin', 'key': '13f0791ae5f19f50e7d0d606fb6501f91b1efb2c', 'id': 'c6e9383c684ff011c5ba35c316ef8f372129868bd4c6c53f32b5f2ee79707dbe', 'severity': 'high'})
skipping: [192.168.122.113] => (item={'groups': ['python'], 'title': 'Difference in Python versions and support in RHEL 8', 'timeStamp': '2025-09-14T19:05:32.383202Z', 'hostname': 'db01.kifarunix.com', 'detail': {'related_resources': [{'scheme': 'package', 'title': 'python'}, {'scheme': 'package', 'title': 'python2'}, {'scheme': 'package', 'title': 'python3'}], 'external': [{'url': 'https://red.ht/rhel-8-python', 'title': 'Difference in Python versions and support in RHEL 8'}], 'remediations': [{'type': 'hint', 'context': 'Please run "alternatives --set python /usr/bin/python3" after upgrade'}]}, 'actor': 'python_inform_user', 'summary': "In RHEL 8, there is no 'python' command. Python 3 (backward incompatible) is the primary Python version and Python 2 is available with limited support and limited set of packages. If you no longer require Python 2 packages following the upgrade, please remove them. Read more here: https://red.ht/rhel-8-python", 'audience': 'developer', 'key': '0c98585b1d8d252eb540bf61560094f3495351f5', 'id': '3d0d02f72396ff7fd871e7609413b84443ce2ca9bd21b1f27856e80ed5720a05', 'severity': 'high'})
skipping: [192.168.122.113] => (item={'groups': ['boot'], 'title': 'GRUB2 core will be automatically updated during the upgrade', 'timeStamp': '2025-09-14T19:05:33.027098Z', 'hostname': 'db01.kifarunix.com', 'actor': 'check_grub_core', 'summary': 'On legacy (BIOS) systems, GRUB2 core (located in the gap between the MBR and the first partition) cannot be updated during the rpm transaction and Leapp has to initiate the update running "grub2-install" after the transaction. No action is needed before the upgrade. After the upgrade, it is recommended to check the GRUB configuration.', 'audience': 'sysadmin', 'key': 'ac7030e05d2ee248d34f08a9fa040b352bc410a3', 'id': '4a78ee397dc2f8eb59f229f79f925774f9ca6b3b8294af2d037fcf471582307e', 'severity': 'high'})
skipping: [192.168.122.113]
TASK [infra.leapp.remediate : leapp_nfs_detected | End play if no leapp report exists] ***********************************************************************************************************************
skipping: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_missing_pkg | End execution of playbook if no entry found in leapp report] ***********************************************************************************************
fatal: [192.168.122.113]: FAILED! => {"ansible_facts": {"leapp_report_missing": true}, "changed": false, "failed_when_result": true}
TASK [infra.leapp.remediate : leapp_missing_pkg | Continue when leapp report is missing] *********************************************************************************************************************
skipping: [192.168.122.113]
TASK [infra.leapp.remediate : leapp_missing_pkg | Check that the leapp-report.json exists] *******************************************************************************************************************
ok: [192.168.122.114]
TASK [infra.leapp.remediate : leapp_missing_pkg | End play if no leapp report exists] ************************************************************************************************************************
skipping: [192.168.122.114]
TASK [infra.leapp.remediate : leapp_nfs_detected | Read leapp report] ****************************************************************************************************************************************
ok: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_nfs_detected | Parse leapp report to json] *******************************************************************************************************************************
ok: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_nfs_detected | Find matching entries] ************************************************************************************************************************************
skipping: [192.168.122.115] => (item={'audience': 'sysadmin', 'detail': {'remediations': [{'context': 'If some of excluded repositories are still required to be used during the upgrade, execute leapp with the --enablerepo option with the repoid of the repository required to be enabled as an argument (the option can be used multiple times).', 'type': 'hint'}]}, 'groups': ['repository', 'failure'], 'key': '1b9132cb2362ae7830e48eee7811be9527747de8', 'severity': 'info', 'summary': 'The following repositories are not supported by Red Hat and are excluded from the list of repositories used during the upgrade.\n- codeready-builder-beta-for-rhel-10-aarch64-rpms\n- codeready-builder-beta-for-rhel-10-s390x-rpms\n- codeready-builder-beta-for-rhel-10-x86_64-rpms\n- codeready-builder-for-rhel-10-ppc64le-rpms\n- codeready-builder-for-rhel-10-x86_64-rpms\n- codeready-builder-for-rhel-10-s390x-rpms\n- codeready-builder-for-rhel-10-aarch64-rpms\n- codeready-builder-beta-for-rhel-10-ppc64le-rpms', 'title': 'Excluded target system repositories', 'timeStamp': '2025-09-14T19:04:57.308998Z', 'hostname': 'lb01.kifarunix.com', 'actor': 'repositories_blacklist', 'id': '94cb08515dd797e3824939aafcd44322253d77bda9563cb60936db9a17e3b0f4'})
skipping: [192.168.122.115] => (item={'audience': 'sysadmin', 'groups': ['kernel', 'drivers'], 'key': 'fbb11ae5828d624c4e4c91e73d766c8e27b066d9', 'severity': 'high', 'summary': 'The following RHEL 9 device drivers are no longer maintained RHEL 10:\n - ip_set\n', 'title': 'Leapp detected loaded kernel drivers which are no longer maintained in RHEL 10.', 'timeStamp': '2025-09-14T19:04:58.449749Z', 'hostname': 'lb01.kifarunix.com', 'actor': 'check_detected_devices_and_drivers', 'id': 'ddf847575c9a0f4eb44a6b8a19aedbf3d5cebd20e46a26ce28f125c9f669844d'})
skipping: [192.168.122.115] => (item={'audience': 'sysadmin', 'groups': ['selinux', 'security'], 'key': '8fb81863f8413bd617c2a55b69b8e10ff03d7c72', 'severity': 'info', 'summary': 'SElinux relabeling will be scheduled as the status is permissive/enforcing.', 'title': 'SElinux relabeling will be scheduled', 'timeStamp': '2025-09-14T19:04:59.028065Z', 'hostname': 'lb01.kifarunix.com', 'actor': 'check_se_linux', 'id': '54dfab25f907a9d4bea10bf9461e53638e906d473b5808fbe6ef6057331d9e7b'})
skipping: [192.168.122.115] => (item={'audience': 'sysadmin', 'detail': {'remediations': [{'context': 'Make sure there are no SElinux related warnings after the upgrade and enable SElinux manually afterwards. Notice: You can ignore the "/root/tmp_leapp_py3" SElinux warnings.', 'type': 'hint'}]}, 'groups': ['selinux', 'security'], 'key': '39d7183dafba798aa4bbb1e70b0ef2bbe5b1772f', 'severity': 'low', 'summary': 'SElinux will be set to permissive mode. Current mode: enforcing. This action is required by the upgrade process to make sure the upgraded system can boot without beinig blocked by SElinux rules.', 'title': 'SElinux will be set to permissive mode', 'timeStamp': '2025-09-14T19:04:59.030734Z', 'hostname': 'lb01.kifarunix.com', 'actor': 'check_se_linux', 'id': '1ca609e1e14e87602f941729ee1d3ba56f34982b8e8ce7c934bbb68a47481bb2'})
skipping: [192.168.122.115] => (item={'audience': 'sysadmin', 'detail': {'external': [{'title': 'Migrating to a RHEL 10 without libdb', 'url': 'https://access.redhat.com/articles/7099256'}], 'related_resources': [{'scheme': 'package', 'title': 'libdb'}], 'remediations': [{'context': 'Back up your data before proceeding with the data upgrade/migration. For the conversion, the tool db_converter from the libdb-utils rpm could be used. This database format conversion must be performed before the system upgrade. The db_converter is not available in RHEL 10 systems. For more information, see the provided article.', 'type': 'hint'}]}, 'groups': ['services'], 'key': 'fdc8f5b084e95922a4f59485a807a92cae2fc738', 'severity': 'medium', 'summary': 'Libdb was marked as deprecated in RHEL-9 and in RHEL-10 is not included anymore. There are a couple of alternatives in RHEL-10; the applications that depend on libdb will not work. Such applications must implement another type of backend storage. And migrate existing data to the new database format.', 'title': 'Berkeley DB (libdb) has been detected on your system', 'timeStamp': '2025-09-14T19:04:59.229329Z', 'hostname': 'lb01.kifarunix.com', 'actor': 'libdb_check', 'id': 'f2a126c7bdce24bbb8031837dc463f131b0eb2736e639166a57da88d3028bccc'})
skipping: [192.168.122.115] => (item={'audience': 'sysadmin', 'groups': ['boot'], 'key': 'ac7030e05d2ee248d34f08a9fa040b352bc410a3', 'severity': 'high', 'summary': 'On legacy (BIOS) systems, GRUB2 core (located in the gap between the MBR and the first partition) cannot be updated during the rpm transaction and Leapp has to initiate the update running "grub2-install" after the transaction. No action is needed before the upgrade. After the upgrade, it is recommended to check the GRUB configuration.', 'title': 'GRUB2 core will be automatically updated during the upgrade', 'timeStamp': '2025-09-14T19:05:00.125578Z', 'hostname': 'lb01.kifarunix.com', 'actor': 'check_grub_core', 'id': '5613d43f82bf326a4e990921b24cc01530cc9dba95aacb7a4b35b70ebcfe40a3'})
skipping: [192.168.122.115] => (item={'audience': 'sysadmin', 'groups': ['services'], 'key': '693963253195f418526f045b6d630a1f4c7a193d', 'severity': 'info', 'summary': "After the upgrade, this system will be automatically registered into Red Hat Insights. To skip the automatic registration, use the '--no-insights-register' command line option or set the LEAPP_NO_INSIGHTS_REGISTER environment variable.", 'title': 'Automatic registration into Red Hat Insights', 'timeStamp': '2025-09-14T19:05:00.441653Z', 'hostname': 'lb01.kifarunix.com', 'actor': 'check_insights_auto_register', 'id': 'b41968c7998227420b259fd9d04966ad28a9322bc3ba3a9c9fa4ae84c049a531'})
TASK [infra.leapp.remediate : leapp_missing_pkg | Read leapp report] *****************************************************************************************************************************************
ok: [192.168.122.114]
TASK [infra.leapp.remediate : leapp_nfs_detected | Find matching entries] ************************************************************************************************************************************
skipping: [192.168.122.115] => (item={'audience': 'sysadmin', 'detail': {'related_resources': [{'scheme': 'package', 'title': 'subscription-manager'}], 'remediations': [{'context': 'If you wish to receive updates for the latest released version of the target system, run `subscription-manager release --unset` after the upgrade.', 'type': 'hint'}]}, 'groups': ['upgrade process'], 'key': '747a4ca25303eda17d1891bb85eeb226be14f252', 'severity': 'low', 'summary': 'After the upgrade has completed the release of the subscription-manager will be set to 10.0. This will ensure that you will receive and keep the version you choose to upgrade to.', 'title': 'The subscription-manager release is going to be set after the upgrade', 'timeStamp': '2025-09-14T19:06:39.027540Z', 'hostname': 'lb01.kifarunix.com', 'actor': 'report_set_target_release', 'id': 'f7aadf3f8580b7bc6a4bcc79b86342a8ac043114e10d060222378c04a6221e1b'})
skipping: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_nfs_detected | End execution of playbook if no entry found in leapp report] **********************************************************************************************
fatal: [192.168.122.115]: FAILED! => {"ansible_facts": {"leapp_report_missing": true}, "changed": false, "failed_when_result": true}
TASK [infra.leapp.remediate : leapp_missing_pkg | Parse leapp report to json] ********************************************************************************************************************************
ok: [192.168.122.114]
TASK [infra.leapp.remediate : leapp_nfs_detected | Continue when leapp report is missing] ********************************************************************************************************************
skipping: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_missing_pkg | Find matching entries] *************************************************************************************************************************************
skipping: [192.168.122.114] => (item={'audience': 'sysadmin', 'detail': {'remediations': [{'context': 'If some of excluded repositories are still required to be used during the upgrade, execute leapp with the --enablerepo option with the repoid of the repository required to be enabled as an argument (the option can be used multiple times).', 'type': 'hint'}]}, 'groups': ['repository', 'failure'], 'key': '1b9132cb2362ae7830e48eee7811be9527747de8', 'severity': 'info', 'summary': 'The following repositories are not supported by Red Hat and are excluded from the list of repositories used during the upgrade.\n- codeready-builder-beta-for-rhel-9-x86_64-rpms\n- codeready-builder-beta-for-rhel-9-aarch64-rpms\n- codeready-builder-for-rhel-9-aarch64-eus-rpms\n- rhui-codeready-builder-for-rhel-9-aarch64-rhui-rpms\n- codeready-builder-beta-for-rhel-9-s390x-rpms\n- codeready-builder-for-rhel-9-rhui-rpms\n- codeready-builder-for-rhel-9-ppc64le-rpms\n- codeready-builder-for-rhel-9-x86_64-eus-rpms\n- codeready-builder-beta-for-rhel-9-ppc64le-rpms\n- codeready-builder-for-rhel-9-ppc64le-eus-rpms\n- codeready-builder-for-rhel-9-x86_64-rhui-rpms\n- codeready-builder-for-rhel-9-x86_64-rpms\n- rhui-codeready-builder-for-rhel-9-x86_64-rhui-rpms\n- codeready-builder-for-rhel-9-aarch64-rpms\n- codeready-builder-for-rhel-9-s390x-eus-rpms\n- codeready-builder-for-rhel-9-s390x-rpms', 'title': 'Excluded target system repositories', 'timeStamp': '2025-09-14T19:05:26.043394Z', 'hostname': 'app01.kifarunix.com', 'actor': 'repositories_blacklist', 'id': 'a09f821d262b79436575a05730f92bb04e849378c9223fae4c955f5d0f11eda5'})
skipping: [192.168.122.114] => (item={'audience': 'sysadmin', 'groups': ['boot'], 'key': 'ac7030e05d2ee248d34f08a9fa040b352bc410a3', 'severity': 'high', 'summary': 'On legacy (BIOS) systems, GRUB2 core (located in the gap between the MBR and the first partition) cannot be updated during the rpm transaction and Leapp has to initiate the update running "grub2-install" after the transaction. No action is needed before the upgrade. After the upgrade, it is recommended to check the GRUB configuration.', 'title': 'GRUB2 core will be automatically updated during the upgrade', 'timeStamp': '2025-09-14T19:05:36.887091Z', 'hostname': 'app01.kifarunix.com', 'actor': 'check_grub_core', 'id': 'b3502b5d6b2885f591a946892d9d6d8e55b832395ada5b02593f0d5a0c4f5ec3'})
skipping: [192.168.122.114] => (item={'audience': 'sysadmin', 'groups': ['kernel', 'drivers'], 'key': 'b03c306f274b33b4cf3c7cd3764366c599681481', 'severity': 'high', 'summary': 'The following RHEL 8 device drivers are no longer maintained RHEL 9:\n - ip_set\n', 'title': 'Leapp detected loaded kernel drivers which are no longer maintained in RHEL 9.', 'timeStamp': '2025-09-14T19:05:38.025716Z', 'hostname': 'app01.kifarunix.com', 'actor': 'check_detected_devices_and_drivers', 'id': '44b1b382f69da71a93bdb28907bff17db461538ae093bb69849130670ee18a6c'})
skipping: [192.168.122.114] => (item={'audience': 'sysadmin', 'groups': ['services'], 'key': '693963253195f418526f045b6d630a1f4c7a193d', 'severity': 'info', 'summary': "After the upgrade, this system will be automatically registered into Red Hat Insights. To skip the automatic registration, use the '--no-insights-register' command line option or set the LEAPP_NO_INSIGHTS_REGISTER environment variable.", 'title': 'Automatic registration into Red Hat Insights', 'timeStamp': '2025-09-14T19:05:38.519741Z', 'hostname': 'app01.kifarunix.com', 'actor': 'check_insights_auto_register', 'id': '9eb4184eb1a350d6e35a18f43cb4fe3d1463a2f75a429d1022318c38e86d5651'})
skipping: [192.168.122.114] => (item={'audience': 'sysadmin', 'detail': {'external': [{'title': 'Handling the migration of your custom and third-party applications', 'url': 'https://red.ht/customize-rhel-upgrade-actors'}], 'remediations': [{'context': 'The most simple solution that does not require additional knowledge about the upgrade process is the uninstallation of such packages before the upgrade and installing these (or their newer versions compatible with the target system) back after the upgrade. Also you can just try to upgrade the system on a testing machine (or after the full system backup) to see the result.\nHowever, it is common use case to migrate or upgrade installed third party packages together with the system during the in-place upgrade process. To examine how to customize the process to deal with such packages, follow the documentation in the attached link for more details.', 'type': 'hint'}]}, 'groups': ['sanity'], 'key': '13f0791ae5f19f50e7d0d606fb6501f91b1efb2c', 'severity': 'high', 'summary': 'The following packages have not been signed by Red Hat and may be removed during the upgrade process in case Red Hat-signed packages to be removed during the upgrade depend on them:\n- docker-buildx-plugin\n- docker-ce-cli\n- docker-compose-plugin', 'title': 'Packages not signed by Red Hat found on the system', 'timeStamp': '2025-09-14T19:05:38.596490Z', 'hostname': 'app01.kifarunix.com', 'actor': 'red_hat_signed_rpm_check', 'id': '78a1f4f1bfdc02527e386d0f1a3b7358fba1592ee4ae5ce7b99acc58561a5851'})
skipping: [192.168.122.114] => (item={'audience': 'sysadmin', 'detail': {'external': [{'title': 'Why Leapp Preupgrade for RHEL 8 to 9 getting "Possible problems with remote login using root account" ?', 'url': 'https://access.redhat.com/solutions/7003083'}], 'related_resources': [{'scheme': 'package', 'title': 'openssh-server'}, {'scheme': 'file', 'title': '/etc/ssh/sshd_config'}], 'remediations': [{'context': 'If you depend on remote root logins using passwords, consider setting up a different user for remote administration or adding a comment into the sshd_config next to the "PermitRootLogin yes" directive to prevent rpm replacing it during the upgrade.', 'type': 'hint'}]}, 'groups': ['authentication', 'security', 'network', 'services', 'inhibitor'], 'key': '3d21e8cc9e1c09dc60429de7716165787e99515f', 'severity': 'high', 'summary': 'OpenSSH configuration file will get updated to RHEL9 version, no longer allowing root login with password. It is a good practice to use non-root administrative user and non-password authentications, but if you rely on the remote root login, this change can lock you out of this system.', 'title': 'Possible problems with remote login using root account', 'timeStamp': '2025-09-14T19:05:39.703699Z', 'hostname': 'app01.kifarunix.com', 'actor': 'openssh_permit_root_login', 'id': 'd395c016d16d65386835be02ce83705ecdc9eb38913cf68a98e1318d884d05c0'})
TASK [infra.leapp.remediate : leapp_nfs_detected | Check that the leapp-report.json exists] ******************************************************************************************************************
ok: [192.168.122.113]
TASK [infra.leapp.remediate : leapp_missing_pkg | Find matching entries] *************************************************************************************************************************************
skipping: [192.168.122.114] => (item={'audience': 'sysadmin', 'detail': {'related_resources': [{'scheme': 'package', 'title': 'openssh-server'}, {'scheme': 'file', 'title': '/etc/ssh/sshd_config'}], 'remediations': [{'context': 'If you depend on remote root logins using passwords, consider setting up a different user for remote administration. Otherwise you can ignore this message.', 'type': 'hint'}]}, 'groups': ['authentication', 'security', 'network', 'services'], 'key': 'e738f78bc8f3a84411a4210e3b609057139d1855', 'severity': 'high', 'summary': 'RHEL9 no longer allows remote root logins, but the server configuration explicitly overrides this default. The configuration file will not be updated and root is still going to be allowed to login with password. This is not recommended and considered as a security risk.', 'title': 'Remote root logins globally allowed using password', 'timeStamp': '2025-09-14T19:05:39.705497Z', 'hostname': 'app01.kifarunix.com', 'actor': 'openssh_permit_root_login', 'id': '206f047e53bad8e749086b50e844bfc63593b406a3d52644d1c97fea26768430'})
skipping: [192.168.122.114] => (item={'audience': 'sysadmin', 'groups': ['selinux', 'security'], 'key': '8fb81863f8413bd617c2a55b69b8e10ff03d7c72', 'severity': 'info', 'summary': 'SElinux relabeling will be scheduled as the status is permissive/enforcing.', 'title': 'SElinux relabeling will be scheduled', 'timeStamp': '2025-09-14T19:05:40.301828Z', 'hostname': 'app01.kifarunix.com', 'actor': 'check_se_linux', 'id': 'b3c51ebc4ab4cecabed84b188aa4b415c02279b9f808b45e1b2ddced7fceda9a'})
skipping: [192.168.122.114]
TASK [infra.leapp.remediate : leapp_nfs_detected | End play if no leapp report exists] ***********************************************************************************************************************
skipping: [192.168.122.113]
TASK [infra.leapp.remediate : leapp_missing_pkg | End execution of playbook if no entry found in leapp report] ***********************************************************************************************
fatal: [192.168.122.114]: FAILED! => {"ansible_facts": {"leapp_report_missing": true}, "changed": false, "failed_when_result": true}
TASK [infra.leapp.remediate : leapp_missing_pkg | Continue when leapp report is missing] *********************************************************************************************************************
skipping: [192.168.122.114]
TASK [infra.leapp.remediate : leapp_partitions_with_noexec | Get all mountpoints with noexec option] *********************************************************************************************************
ok: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_partitions_with_noexec | Go through the the mountpoints and remount] *****************************************************************************************************
skipping: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_partitions_with_noexec | Modify /etc/fstab to replace the noexec option] *************************************************************************************************
skipping: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_nfs_detected | Check that the leapp-report.json exists] ******************************************************************************************************************
ok: [192.168.122.114]
TASK [infra.leapp.remediate : leapp_nfs_detected | End play if no leapp report exists] ***********************************************************************************************************************
skipping: [192.168.122.114]
TASK [infra.leapp.remediate : leapp_nfs_detected | Read leapp report] ****************************************************************************************************************************************
ok: [192.168.122.113]
TASK [infra.leapp.remediate : leapp_nfs_detected | Parse leapp report to json] *******************************************************************************************************************************
ok: [192.168.122.113]
TASK [infra.leapp.remediate : leapp_nfs_detected | Find matching entries] ************************************************************************************************************************************
skipping: [192.168.122.113] => (item={'groups': ['network', 'inhibitor'], 'title': 'Unsupported network configuration', 'timeStamp': '2025-09-14T19:05:16.373921Z', 'hostname': 'db01.kifarunix.com', 'detail': {'external': [{'url': 'https://access.redhat.com/solutions/4067471', 'title': 'How to perform an in-place upgrade to RHEL 8 when using kernel NIC names on RHEL 7'}, {'url': 'https://access.redhat.com/solutions/7009239', 'title': 'RHEL 8 to RHEL 9: inplace upgrade fails at "Network configuration for unsupported device types detected"'}], 'remediations': [{'type': 'hint', 'context': 'Rename all ethX network interfaces following the attached KB solution article.'}]}, 'actor': 'persistentnetnamesdisable', 'summary': 'Detected multiple physical network interfaces where one or more use kernel naming (e.g. eth0). Upgrade process can not continue because stability of names can not be guaranteed. Please read the article at https://access.redhat.com/solutions/4067471 for more information.', 'audience': 'sysadmin', 'key': 'd3050d265759a79ce895e64f45e9c56e49b3a953', 'id': '713dbc223571ebf608d752e56cf94c92846b0ccde9442bccf499d6dd11703ab0', 'severity': 'high'})
skipping: [192.168.122.113] => (item={'groups': ['repository', 'failure'], 'title': 'Excluded target system repositories', 'timeStamp': '2025-09-14T19:05:16.440845Z', 'hostname': 'db01.kifarunix.com', 'detail': {'remediations': [{'type': 'hint', 'context': 'If some of excluded repositories are still required to be used during the upgrade, execute leapp with the --enablerepo option with the repoid of the repository required to be enabled as an argument (the option can be used multiple times).'}]}, 'actor': 'repositories_blacklist', 'summary': 'The following repositories are not supported by Red Hat and are excluded from the list of repositories used during the upgrade.\n- codeready-builder-beta-for-rhel-8-s390x-rpms\n- codeready-builder-beta-for-rhel-8-ppc64le-rpms\n- rhui-codeready-builder-for-rhel-8-x86_64-rhui-rpms\n- codeready-builder-for-rhel-8-aarch64-eus-rpms\n- codeready-builder-for-rhel-8-ppc64le-eus-rpms\n- codeready-builder-beta-for-rhel-8-x86_64-rpms\n- codeready-builder-for-rhel-8-aarch64-rpms\n- codeready-builder-for-rhel-8-s390x-rpms\n- codeready-builder-for-rhel-8-s390x-eus-rpms\n- codeready-builder-for-rhel-8-x86_64-eus-rpms\n- rhui-codeready-builder-for-rhel-8-aarch64-rhui-rpms\n- codeready-builder-beta-for-rhel-8-aarch64-rpms\n- codeready-builder-for-rhel-8-rhui-rpms\n- codeready-builder-for-rhel-8-x86_64-rhui-rpms\n- codeready-builder-for-rhel-8-x86_64-rpms\n- codeready-builder-for-rhel-8-x86_64-eus-rhui-rpms\n- codeready-builder-for-rhel-8-ppc64le-rpms', 'audience': 'sysadmin', 'key': '1b9132cb2362ae7830e48eee7811be9527747de8', 'id': 'df101d8c2318a3155aaddb9389b2770465b064eb7af40f1f1b2a95c3c324ac2c', 'severity': 'info'})
skipping: [192.168.122.113] => (item={'groups': ['repository'], 'title': 'Packages available in excluded repositories will not be installed', 'timeStamp': '2025-09-14T19:05:26.230023Z', 'hostname': 'db01.kifarunix.com', 'detail': {'related_resources': [{'scheme': 'package', 'title': 'python3-pyxattr'}, {'scheme': 'package', 'title': 'rpcgen'}]}, 'actor': 'pes_events_scanner', 'summary': '2 packages will be skipped because they are available only in target system repositories that are intentionally excluded from the list of repositories used during the upgrade. See the report message titled "Excluded target system repositories" for details.\nThe list of these packages:\n- python3-pyxattr (repoid: codeready-builder-for-rhel-8-x86_64-rpms)\n- rpcgen (repoid: codeready-builder-for-rhel-8-x86_64-rpms)', 'audience': 'sysadmin', 'key': '2437e204808f987477c0e9be8e4c95b3a87a9f3e', 'id': '180cbb8d679af19b3ce7bb52416361329fbdee530ef3908e7a5c80dcc326751a', 'severity': 'high'})
skipping: [192.168.122.113] => (item={'groups': ['services', 'email'], 'title': 'Postfix has incompatible changes in the next major version', 'timeStamp': '2025-09-14T19:05:28.915211Z', 'hostname': 'db01.kifarunix.com', 'detail': {'related_resources': [{'scheme': 'package', 'title': 'postfix'}]}, 'actor': 'check_postfix', 'summary': 'Postfix 3.x has so called "compatibility safety net" that runs Postfix programs with backwards-compatible default settings. It will log a warning whenever backwards-compatible default setting may be required for continuity of service. Based on this logging the system administrator can decide if any backwards-compatible settings need to be made permanent in main.cf or master.cf, before turning off the backwards-compatibility safety net.\nThe backward compatibility safety net is by default turned off in Red Hat Enterprise Linux 8.\nIt can be turned on by running: "postconf -e compatibility_level=0\nIt can be turned off by running: "postconf -e compatibility_level=2\n\nIn the Postfix MySQL database client, the default "option_group" value has changed to "client", i.e. it now reads options from the [client] group from the MySQL configuration file. To disable it, set "option_group" to the empty string.\n\nThe postqueue command no longer forces all message arrival times to be reported in UTC. To get the old behavior, set TZ=UTC in main.cf:import_environment.\n\nPostfix 3.2 enables elliptic curve negotiation. This changes the default smtpd_tls_eecdh_grade setting to "auto", and introduces a new parameter "tls_eecdh_auto_curves" with the names of curves that may be negotiated.\n\nThe "master.cf" chroot default value has changed from "y" (yes) to "n" (no). This applies to master.cf services where chroot field is not explicitly specified.\n\nThe "append_dot_mydomain" default value has changed from "yes" to "no". You may need changing it to "yes" if senders cannot use complete domain names in e-mail addresses.\n\nThe "relay_domains" default value has changed from "$mydestination" to the empty value. This could result in unexpected "Relay access denied" errors or ETRN errors, because now will postfix by default relay only for the localhost.\n\nThe "mynetworks_style" default value has changed from "subnet" to "host". This parameter is used to implement the "permit_mynetworks" feature. The change could result in unexpected "access denied" errors, because postfix will now by default trust only the local machine, not the remote SMTP clients on the same IP subnetwork.\n\nPostfix now supports dynamically loaded database plugins. Plugins are shipped in individual RPM sub-packages. Correct database plugins have to be installed, otherwise the specific database client will not work. For example for PostgreSQL map to work, the postfix-pgsql RPM package has to be installed.\n', 'audience': 'sysadmin', 'key': '5721e0a07a67d82cf7e5ea6f17662cd4f82e0a33', 'id': '458db741f010f9f794baaade24bd1dbb0c148582cba09d101ede50e8631036bd', 'severity': 'low'})
skipping: [192.168.122.113] => (item={'groups': ['authentication', 'security', 'tools'], 'title': 'Current PAM and nsswitch.conf configuration will be kept.', 'timeStamp': '2025-09-14T19:05:29.244997Z', 'hostname': 'db01.kifarunix.com', 'detail': {'related_resources': [{'scheme': 'package', 'title': 'authselect'}, {'scheme': 'package', 'title': 'authconfig'}, {'scheme': 'file', 'title': '/etc/nsswitch.conf'}]}, 'actor': 'authselect_check', 'summary': 'There is a new tool called authselect in RHEL8 that replaced authconfig. The upgrade process was unable to find an authselect profile that would be equivalent to your current configuration. Therefore your configuration will be left intact.', 'audience': 'sysadmin', 'key': '40c4ab1da4a30dc1ca40e543f6385e1336d8810c', 'id': 'be1cd7747e9b75de9fb3e3f312000bae551aeb4e3f3fefa81abd23c95173931e', 'severity': 'info'})
skipping: [192.168.122.113] => (item={'groups': ['selinux', 'security'], 'title': 'SElinux relabeling will be scheduled', 'timeStamp': '2025-09-14T19:05:29.846483Z', 'hostname': 'db01.kifarunix.com', 'actor': 'check_se_linux', 'summary': 'SElinux relabeling will be scheduled as the status is permissive/enforcing.', 'audience': 'sysadmin', 'key': '8fb81863f8413bd617c2a55b69b8e10ff03d7c72', 'id': '691e774f3d6024008baf68459dd0eae6fca877ee7080877f62156e5d199e6116', 'severity': 'info'})
skipping: [192.168.122.113] => (item={'groups': ['selinux', 'security'], 'title': 'SElinux will be set to permissive mode', 'timeStamp': '2025-09-14T19:05:29.849799Z', 'hostname': 'db01.kifarunix.com', 'detail': {'remediations': [{'type': 'hint', 'context': 'Make sure there are no SElinux related warnings after the upgrade and enable SElinux manually afterwards. Notice: You can ignore the "/root/tmp_leapp_py3" SElinux warnings.'}]}, 'actor': 'check_se_linux', 'summary': 'SElinux will be set to permissive mode. Current mode: enforcing. This action is required by the upgrade process to make sure the upgraded system can boot without beinig blocked by SElinux rules.', 'audience': 'sysadmin', 'key': '39d7183dafba798aa4bbb1e70b0ef2bbe5b1772f', 'id': '37c825a748e1ff17630f5fb5763a66d7d3d5b13e371fc92f781301356f2e61f4', 'severity': 'low'})
skipping: [192.168.122.113] => (item={'groups': ['tools'], 'title': 'Grep has incompatible changes in the next major version', 'timeStamp': '2025-09-14T19:05:30.037961Z', 'hostname': 'db01.kifarunix.com', 'detail': {'related_resources': [{'scheme': 'package', 'title': 'grep'}], 'remediations': [{'type': 'hint', 'context': 'Please update your scripts to be compatible with the changes.'}]}, 'actor': 'checkgrep', 'summary': 'If a file contains data improperly encoded for the current locale, and this is discovered before any of the file\'s contents are output, grep now treats the file as binary.\nThe \'grep -P\' no longer reports an error and exits when given invalid UTF-8 data. Instead, it considers the data to be non-matching.\nIn locales with multibyte character encodings other than UTF-8, grep -P now reports an error and exits instead of misbehaving.\nWhen searching binary data, grep now may treat non-text bytes as line terminators. This can boost performance significantly.\nThe \'grep -z\' no longer automatically treats the byte \'\\200\' as binary data.\nContext no longer excludes selected lines omitted because of -m. For example, \'grep "^" -m1 -A1\' now outputs the first two input lines, not just the first line.\n', 'audience': 'sysadmin', 'key': '94665a499e2eeee35eca3e7093a7abe183384b16', 'id': '784d95461b6f29da836440f95e2a32c8a62f08f19539cee7c3a37d3e0eeb9a10', 'severity': 'low'})
skipping: [192.168.122.113] => (item={'groups': ['services', 'time management'], 'title': 'chrony using default configuration', 'timeStamp': '2025-09-14T19:05:31.352819Z', 'hostname': 'db01.kifarunix.com', 'detail': {'related_resources': [{'scheme': 'package', 'title': 'ntpd'}, {'scheme': 'package', 'title': 'chrony'}, {'scheme': 'file', 'title': '/etc/chrony.conf'}]}, 'actor': 'check_chrony', 'summary': 'default chrony configuration in RHEL8 uses leapsectz directive, which cannot be used with leap smearing NTP servers, and uses a single pool directive instead of four server directives', 'audience': 'sysadmin', 'key': 'c4222ebd18730a76f6bc7b3b66df898b106e6554', 'id': '871c92c073d90f50aeb7eca8823feef633757cae1a37bbcf454fe87a45e7e7ab', 'severity': 'medium'})
skipping: [192.168.122.113] => (item={'groups': ['services'], 'title': 'Automatic registration into Red Hat Insights', 'timeStamp': '2025-09-14T19:05:31.657640Z', 'hostname': 'db01.kifarunix.com', 'actor': 'check_insights_auto_register', 'summary': "After the upgrade, this system will be automatically registered into Red Hat Insights. The 'insights-client' package required for the registration will be installed during the upgrade. To skip the automatic registration, use the '--no-insights-register' command line option or set the LEAPP_NO_INSIGHTS_REGISTER environment variable.", 'audience': 'sysadmin', 'key': '693963253195f418526f045b6d630a1f4c7a193d', 'id': '01e8e642f1919afeb175f21ae47f2806848d7971fe8970e5248124f896596f95', 'severity': 'info'})
skipping: [192.168.122.113] => (item={'groups': ['authentication', 'security', 'tools'], 'title': 'Module pam_pkcs11 will be removed from PAM configuration', 'timeStamp': '2025-09-14T19:05:31.703394Z', 'hostname': 'db01.kifarunix.com', 'detail': {'related_resources': [{'scheme': 'package', 'title': 'sssd'}], 'remediations': [{'type': 'hint', 'context': 'Configure SSSD to replace pam_pkcs11'}]}, 'actor': 'removed_pam_modules_check', 'summary': 'Module pam_pkcs11 was surpassed by SSSD and therefore it was removed from RHEL-8. Keeping it in PAM configuration may lock out the system thus it will be automatically removed from PAM configuration before upgrading to RHEL-8. Please switch to SSSD to recover the functionality of pam_pkcs11.', 'audience': 'sysadmin', 'key': 'bf47e7305d6805e8bbeaa7593cf01e38030c23f3', 'id': 'b9e5d0ac7d1a88b226abf1a17ce7ee777e87d1cb6cd207b1bd09d22443640015', 'severity': 'medium'})
skipping: [192.168.122.113] => (item={'groups': ['sanity'], 'title': 'Packages not signed by Red Hat found on the system', 'timeStamp': '2025-09-14T19:05:31.975841Z', 'hostname': 'db01.kifarunix.com', 'actor': 'red_hat_signed_rpm_check', 'summary': 'The following packages have not been signed by Red Hat and may be removed during the upgrade process in case Red Hat-signed packages to be removed during the upgrade depend on them:\n- containerd.io\n- docker-buildx-plugin\n- docker-ce\n- docker-ce-cli\n- docker-ce-rootless-extras\n- docker-compose-plugin\n- fuse-overlayfs\n- fuse3-libs\n- slirp4netns', 'audience': 'sysadmin', 'key': '13f0791ae5f19f50e7d0d606fb6501f91b1efb2c', 'id': 'c6e9383c684ff011c5ba35c316ef8f372129868bd4c6c53f32b5f2ee79707dbe', 'severity': 'high'})
skipping: [192.168.122.113] => (item={'groups': ['python'], 'title': 'Difference in Python versions and support in RHEL 8', 'timeStamp': '2025-09-14T19:05:32.383202Z', 'hostname': 'db01.kifarunix.com', 'detail': {'related_resources': [{'scheme': 'package', 'title': 'python'}, {'scheme': 'package', 'title': 'python2'}, {'scheme': 'package', 'title': 'python3'}], 'external': [{'url': 'https://red.ht/rhel-8-python', 'title': 'Difference in Python versions and support in RHEL 8'}], 'remediations': [{'type': 'hint', 'context': 'Please run "alternatives --set python /usr/bin/python3" after upgrade'}]}, 'actor': 'python_inform_user', 'summary': "In RHEL 8, there is no 'python' command. Python 3 (backward incompatible) is the primary Python version and Python 2 is available with limited support and limited set of packages. If you no longer require Python 2 packages following the upgrade, please remove them. Read more here: https://red.ht/rhel-8-python", 'audience': 'developer', 'key': '0c98585b1d8d252eb540bf61560094f3495351f5', 'id': '3d0d02f72396ff7fd871e7609413b84443ce2ca9bd21b1f27856e80ed5720a05', 'severity': 'high'})
skipping: [192.168.122.113] => (item={'groups': ['boot'], 'title': 'GRUB2 core will be automatically updated during the upgrade', 'timeStamp': '2025-09-14T19:05:33.027098Z', 'hostname': 'db01.kifarunix.com', 'actor': 'check_grub_core', 'summary': 'On legacy (BIOS) systems, GRUB2 core (located in the gap between the MBR and the first partition) cannot be updated during the rpm transaction and Leapp has to initiate the update running "grub2-install" after the transaction. No action is needed before the upgrade. After the upgrade, it is recommended to check the GRUB configuration.', 'audience': 'sysadmin', 'key': 'ac7030e05d2ee248d34f08a9fa040b352bc410a3', 'id': '4a78ee397dc2f8eb59f229f79f925774f9ca6b3b8294af2d037fcf471582307e', 'severity': 'high'})
skipping: [192.168.122.113]
TASK [infra.leapp.remediate : leapp_nfs_detected | End execution of playbook if no entry found in leapp report] **********************************************************************************************
fatal: [192.168.122.113]: FAILED! => {"ansible_facts": {"leapp_report_missing": true}, "changed": false, "failed_when_result": true}
TASK [infra.leapp.remediate : leapp_nfs_detected | Continue when leapp report is missing] ********************************************************************************************************************
skipping: [192.168.122.113]
TASK [infra.leapp.remediate : leapp_remote_using_root | Configure sshd to prohibit-passwords on root login] **************************************************************************************************
changed: [192.168.122.115] => (item={'key': 'PermitRootLogin', 'value': 'prohibit-password'})
TASK [infra.leapp.remediate : leapp_nfs_detected | Read leapp report] ****************************************************************************************************************************************
ok: [192.168.122.114]
TASK [infra.leapp.remediate : leapp_rpms_with_rsa_sha1_detected | Check that the leapp-report.json exists] ***************************************************************************************************
skipping: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_nfs_detected | Parse leapp report to json] *******************************************************************************************************************************
ok: [192.168.122.114]
TASK [infra.leapp.remediate : leapp_rpms_with_rsa_sha1_detected | End play if no leapp report exists] ********************************************************************************************************
skipping: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_nfs_detected | Find matching entries] ************************************************************************************************************************************
skipping: [192.168.122.114] => (item={'audience': 'sysadmin', 'detail': {'remediations': [{'context': 'If some of excluded repositories are still required to be used during the upgrade, execute leapp with the --enablerepo option with the repoid of the repository required to be enabled as an argument (the option can be used multiple times).', 'type': 'hint'}]}, 'groups': ['repository', 'failure'], 'key': '1b9132cb2362ae7830e48eee7811be9527747de8', 'severity': 'info', 'summary': 'The following repositories are not supported by Red Hat and are excluded from the list of repositories used during the upgrade.\n- codeready-builder-beta-for-rhel-9-x86_64-rpms\n- codeready-builder-beta-for-rhel-9-aarch64-rpms\n- codeready-builder-for-rhel-9-aarch64-eus-rpms\n- rhui-codeready-builder-for-rhel-9-aarch64-rhui-rpms\n- codeready-builder-beta-for-rhel-9-s390x-rpms\n- codeready-builder-for-rhel-9-rhui-rpms\n- codeready-builder-for-rhel-9-ppc64le-rpms\n- codeready-builder-for-rhel-9-x86_64-eus-rpms\n- codeready-builder-beta-for-rhel-9-ppc64le-rpms\n- codeready-builder-for-rhel-9-ppc64le-eus-rpms\n- codeready-builder-for-rhel-9-x86_64-rhui-rpms\n- codeready-builder-for-rhel-9-x86_64-rpms\n- rhui-codeready-builder-for-rhel-9-x86_64-rhui-rpms\n- codeready-builder-for-rhel-9-aarch64-rpms\n- codeready-builder-for-rhel-9-s390x-eus-rpms\n- codeready-builder-for-rhel-9-s390x-rpms', 'title': 'Excluded target system repositories', 'timeStamp': '2025-09-14T19:05:26.043394Z', 'hostname': 'app01.kifarunix.com', 'actor': 'repositories_blacklist', 'id': 'a09f821d262b79436575a05730f92bb04e849378c9223fae4c955f5d0f11eda5'})
skipping: [192.168.122.114] => (item={'audience': 'sysadmin', 'groups': ['boot'], 'key': 'ac7030e05d2ee248d34f08a9fa040b352bc410a3', 'severity': 'high', 'summary': 'On legacy (BIOS) systems, GRUB2 core (located in the gap between the MBR and the first partition) cannot be updated during the rpm transaction and Leapp has to initiate the update running "grub2-install" after the transaction. No action is needed before the upgrade. After the upgrade, it is recommended to check the GRUB configuration.', 'title': 'GRUB2 core will be automatically updated during the upgrade', 'timeStamp': '2025-09-14T19:05:36.887091Z', 'hostname': 'app01.kifarunix.com', 'actor': 'check_grub_core', 'id': 'b3502b5d6b2885f591a946892d9d6d8e55b832395ada5b02593f0d5a0c4f5ec3'})
skipping: [192.168.122.114] => (item={'audience': 'sysadmin', 'groups': ['kernel', 'drivers'], 'key': 'b03c306f274b33b4cf3c7cd3764366c599681481', 'severity': 'high', 'summary': 'The following RHEL 8 device drivers are no longer maintained RHEL 9:\n - ip_set\n', 'title': 'Leapp detected loaded kernel drivers which are no longer maintained in RHEL 9.', 'timeStamp': '2025-09-14T19:05:38.025716Z', 'hostname': 'app01.kifarunix.com', 'actor': 'check_detected_devices_and_drivers', 'id': '44b1b382f69da71a93bdb28907bff17db461538ae093bb69849130670ee18a6c'})
skipping: [192.168.122.114] => (item={'audience': 'sysadmin', 'groups': ['services'], 'key': '693963253195f418526f045b6d630a1f4c7a193d', 'severity': 'info', 'summary': "After the upgrade, this system will be automatically registered into Red Hat Insights. To skip the automatic registration, use the '--no-insights-register' command line option or set the LEAPP_NO_INSIGHTS_REGISTER environment variable.", 'title': 'Automatic registration into Red Hat Insights', 'timeStamp': '2025-09-14T19:05:38.519741Z', 'hostname': 'app01.kifarunix.com', 'actor': 'check_insights_auto_register', 'id': '9eb4184eb1a350d6e35a18f43cb4fe3d1463a2f75a429d1022318c38e86d5651'})
TASK [infra.leapp.remediate : leapp_rpms_with_rsa_sha1_detected | Read leapp report] *************************************************************************************************************************
skipping: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_nfs_detected | Find matching entries] ************************************************************************************************************************************
skipping: [192.168.122.114] => (item={'audience': 'sysadmin', 'detail': {'external': [{'title': 'Handling the migration of your custom and third-party applications', 'url': 'https://red.ht/customize-rhel-upgrade-actors'}], 'remediations': [{'context': 'The most simple solution that does not require additional knowledge about the upgrade process is the uninstallation of such packages before the upgrade and installing these (or their newer versions compatible with the target system) back after the upgrade. Also you can just try to upgrade the system on a testing machine (or after the full system backup) to see the result.\nHowever, it is common use case to migrate or upgrade installed third party packages together with the system during the in-place upgrade process. To examine how to customize the process to deal with such packages, follow the documentation in the attached link for more details.', 'type': 'hint'}]}, 'groups': ['sanity'], 'key': '13f0791ae5f19f50e7d0d606fb6501f91b1efb2c', 'severity': 'high', 'summary': 'The following packages have not been signed by Red Hat and may be removed during the upgrade process in case Red Hat-signed packages to be removed during the upgrade depend on them:\n- docker-buildx-plugin\n- docker-ce-cli\n- docker-compose-plugin', 'title': 'Packages not signed by Red Hat found on the system', 'timeStamp': '2025-09-14T19:05:38.596490Z', 'hostname': 'app01.kifarunix.com', 'actor': 'red_hat_signed_rpm_check', 'id': '78a1f4f1bfdc02527e386d0f1a3b7358fba1592ee4ae5ce7b99acc58561a5851'})
skipping: [192.168.122.114] => (item={'audience': 'sysadmin', 'detail': {'external': [{'title': 'Why Leapp Preupgrade for RHEL 8 to 9 getting "Possible problems with remote login using root account" ?', 'url': 'https://access.redhat.com/solutions/7003083'}], 'related_resources': [{'scheme': 'package', 'title': 'openssh-server'}, {'scheme': 'file', 'title': '/etc/ssh/sshd_config'}], 'remediations': [{'context': 'If you depend on remote root logins using passwords, consider setting up a different user for remote administration or adding a comment into the sshd_config next to the "PermitRootLogin yes" directive to prevent rpm replacing it during the upgrade.', 'type': 'hint'}]}, 'groups': ['authentication', 'security', 'network', 'services', 'inhibitor'], 'key': '3d21e8cc9e1c09dc60429de7716165787e99515f', 'severity': 'high', 'summary': 'OpenSSH configuration file will get updated to RHEL9 version, no longer allowing root login with password. It is a good practice to use non-root administrative user and non-password authentications, but if you rely on the remote root login, this change can lock you out of this system.', 'title': 'Possible problems with remote login using root account', 'timeStamp': '2025-09-14T19:05:39.703699Z', 'hostname': 'app01.kifarunix.com', 'actor': 'openssh_permit_root_login', 'id': 'd395c016d16d65386835be02ce83705ecdc9eb38913cf68a98e1318d884d05c0'})
skipping: [192.168.122.114] => (item={'audience': 'sysadmin', 'detail': {'related_resources': [{'scheme': 'package', 'title': 'openssh-server'}, {'scheme': 'file', 'title': '/etc/ssh/sshd_config'}], 'remediations': [{'context': 'If you depend on remote root logins using passwords, consider setting up a different user for remote administration. Otherwise you can ignore this message.', 'type': 'hint'}]}, 'groups': ['authentication', 'security', 'network', 'services'], 'key': 'e738f78bc8f3a84411a4210e3b609057139d1855', 'severity': 'high', 'summary': 'RHEL9 no longer allows remote root logins, but the server configuration explicitly overrides this default. The configuration file will not be updated and root is still going to be allowed to login with password. This is not recommended and considered as a security risk.', 'title': 'Remote root logins globally allowed using password', 'timeStamp': '2025-09-14T19:05:39.705497Z', 'hostname': 'app01.kifarunix.com', 'actor': 'openssh_permit_root_login', 'id': '206f047e53bad8e749086b50e844bfc63593b406a3d52644d1c97fea26768430'})
skipping: [192.168.122.114] => (item={'audience': 'sysadmin', 'groups': ['selinux', 'security'], 'key': '8fb81863f8413bd617c2a55b69b8e10ff03d7c72', 'severity': 'info', 'summary': 'SElinux relabeling will be scheduled as the status is permissive/enforcing.', 'title': 'SElinux relabeling will be scheduled', 'timeStamp': '2025-09-14T19:05:40.301828Z', 'hostname': 'app01.kifarunix.com', 'actor': 'check_se_linux', 'id': 'b3c51ebc4ab4cecabed84b188aa4b415c02279b9f808b45e1b2ddced7fceda9a'})
skipping: [192.168.122.114]
TASK [infra.leapp.remediate : leapp_rpms_with_rsa_sha1_detected | Parse leapp report to json] ****************************************************************************************************************
skipping: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_nfs_detected | End execution of playbook if no entry found in leapp report] **********************************************************************************************
fatal: [192.168.122.114]: FAILED! => {"ansible_facts": {"leapp_report_missing": true}, "changed": false, "failed_when_result": true}
TASK [infra.leapp.remediate : leapp_nfs_detected | Continue when leapp report is missing] ********************************************************************************************************************
skipping: [192.168.122.114]
TASK [infra.leapp.remediate : leapp_rpms_with_rsa_sha1_detected | Find matching entries] *********************************************************************************************************************
skipping: [192.168.122.115] => (item={'audience': 'sysadmin', 'detail': {'remediations': [{'context': 'If some of excluded repositories are still required to be used during the upgrade, execute leapp with the --enablerepo option with the repoid of the repository required to be enabled as an argument (the option can be used multiple times).', 'type': 'hint'}]}, 'groups': ['repository', 'failure'], 'key': '1b9132cb2362ae7830e48eee7811be9527747de8', 'severity': 'info', 'summary': 'The following repositories are not supported by Red Hat and are excluded from the list of repositories used during the upgrade.\n- codeready-builder-beta-for-rhel-10-aarch64-rpms\n- codeready-builder-beta-for-rhel-10-s390x-rpms\n- codeready-builder-beta-for-rhel-10-x86_64-rpms\n- codeready-builder-for-rhel-10-ppc64le-rpms\n- codeready-builder-for-rhel-10-x86_64-rpms\n- codeready-builder-for-rhel-10-s390x-rpms\n- codeready-builder-for-rhel-10-aarch64-rpms\n- codeready-builder-beta-for-rhel-10-ppc64le-rpms', 'title': 'Excluded target system repositories', 'timeStamp': '2025-09-14T19:04:57.308998Z', 'hostname': 'lb01.kifarunix.com', 'actor': 'repositories_blacklist', 'id': '94cb08515dd797e3824939aafcd44322253d77bda9563cb60936db9a17e3b0f4'})
skipping: [192.168.122.115] => (item={'audience': 'sysadmin', 'groups': ['kernel', 'drivers'], 'key': 'fbb11ae5828d624c4e4c91e73d766c8e27b066d9', 'severity': 'high', 'summary': 'The following RHEL 9 device drivers are no longer maintained RHEL 10:\n - ip_set\n', 'title': 'Leapp detected loaded kernel drivers which are no longer maintained in RHEL 10.', 'timeStamp': '2025-09-14T19:04:58.449749Z', 'hostname': 'lb01.kifarunix.com', 'actor': 'check_detected_devices_and_drivers', 'id': 'ddf847575c9a0f4eb44a6b8a19aedbf3d5cebd20e46a26ce28f125c9f669844d'})
skipping: [192.168.122.115] => (item={'audience': 'sysadmin', 'groups': ['selinux', 'security'], 'key': '8fb81863f8413bd617c2a55b69b8e10ff03d7c72', 'severity': 'info', 'summary': 'SElinux relabeling will be scheduled as the status is permissive/enforcing.', 'title': 'SElinux relabeling will be scheduled', 'timeStamp': '2025-09-14T19:04:59.028065Z', 'hostname': 'lb01.kifarunix.com', 'actor': 'check_se_linux', 'id': '54dfab25f907a9d4bea10bf9461e53638e906d473b5808fbe6ef6057331d9e7b'})
skipping: [192.168.122.115] => (item={'audience': 'sysadmin', 'detail': {'remediations': [{'context': 'Make sure there are no SElinux related warnings after the upgrade and enable SElinux manually afterwards. Notice: You can ignore the "/root/tmp_leapp_py3" SElinux warnings.', 'type': 'hint'}]}, 'groups': ['selinux', 'security'], 'key': '39d7183dafba798aa4bbb1e70b0ef2bbe5b1772f', 'severity': 'low', 'summary': 'SElinux will be set to permissive mode. Current mode: enforcing. This action is required by the upgrade process to make sure the upgraded system can boot without beinig blocked by SElinux rules.', 'title': 'SElinux will be set to permissive mode', 'timeStamp': '2025-09-14T19:04:59.030734Z', 'hostname': 'lb01.kifarunix.com', 'actor': 'check_se_linux', 'id': '1ca609e1e14e87602f941729ee1d3ba56f34982b8e8ce7c934bbb68a47481bb2'})
skipping: [192.168.122.115] => (item={'audience': 'sysadmin', 'detail': {'external': [{'title': 'Migrating to a RHEL 10 without libdb', 'url': 'https://access.redhat.com/articles/7099256'}], 'related_resources': [{'scheme': 'package', 'title': 'libdb'}], 'remediations': [{'context': 'Back up your data before proceeding with the data upgrade/migration. For the conversion, the tool db_converter from the libdb-utils rpm could be used. This database format conversion must be performed before the system upgrade. The db_converter is not available in RHEL 10 systems. For more information, see the provided article.', 'type': 'hint'}]}, 'groups': ['services'], 'key': 'fdc8f5b084e95922a4f59485a807a92cae2fc738', 'severity': 'medium', 'summary': 'Libdb was marked as deprecated in RHEL-9 and in RHEL-10 is not included anymore. There are a couple of alternatives in RHEL-10; the applications that depend on libdb will not work. Such applications must implement another type of backend storage. And migrate existing data to the new database format.', 'title': 'Berkeley DB (libdb) has been detected on your system', 'timeStamp': '2025-09-14T19:04:59.229329Z', 'hostname': 'lb01.kifarunix.com', 'actor': 'libdb_check', 'id': 'f2a126c7bdce24bbb8031837dc463f131b0eb2736e639166a57da88d3028bccc'})
skipping: [192.168.122.115] => (item={'audience': 'sysadmin', 'groups': ['boot'], 'key': 'ac7030e05d2ee248d34f08a9fa040b352bc410a3', 'severity': 'high', 'summary': 'On legacy (BIOS) systems, GRUB2 core (located in the gap between the MBR and the first partition) cannot be updated during the rpm transaction and Leapp has to initiate the update running "grub2-install" after the transaction. No action is needed before the upgrade. After the upgrade, it is recommended to check the GRUB configuration.', 'title': 'GRUB2 core will be automatically updated during the upgrade', 'timeStamp': '2025-09-14T19:05:00.125578Z', 'hostname': 'lb01.kifarunix.com', 'actor': 'check_grub_core', 'id': '5613d43f82bf326a4e990921b24cc01530cc9dba95aacb7a4b35b70ebcfe40a3'})
skipping: [192.168.122.115] => (item={'audience': 'sysadmin', 'groups': ['services'], 'key': '693963253195f418526f045b6d630a1f4c7a193d', 'severity': 'info', 'summary': "After the upgrade, this system will be automatically registered into Red Hat Insights. To skip the automatic registration, use the '--no-insights-register' command line option or set the LEAPP_NO_INSIGHTS_REGISTER environment variable.", 'title': 'Automatic registration into Red Hat Insights', 'timeStamp': '2025-09-14T19:05:00.441653Z', 'hostname': 'lb01.kifarunix.com', 'actor': 'check_insights_auto_register', 'id': 'b41968c7998227420b259fd9d04966ad28a9322bc3ba3a9c9fa4ae84c049a531'})
skipping: [192.168.122.115] => (item={'audience': 'sysadmin', 'detail': {'related_resources': [{'scheme': 'package', 'title': 'subscription-manager'}], 'remediations': [{'context': 'If you wish to receive updates for the latest released version of the target system, run `subscription-manager release --unset` after the upgrade.', 'type': 'hint'}]}, 'groups': ['upgrade process'], 'key': '747a4ca25303eda17d1891bb85eeb226be14f252', 'severity': 'low', 'summary': 'After the upgrade has completed the release of the subscription-manager will be set to 10.0. This will ensure that you will receive and keep the version you choose to upgrade to.', 'title': 'The subscription-manager release is going to be set after the upgrade', 'timeStamp': '2025-09-14T19:06:39.027540Z', 'hostname': 'lb01.kifarunix.com', 'actor': 'report_set_target_release', 'id': 'f7aadf3f8580b7bc6a4bcc79b86342a8ac043114e10d060222378c04a6221e1b'})
skipping: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_rpms_with_rsa_sha1_detected | End execution of playbook if no entry found in leapp report] *******************************************************************************
skipping: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_rpms_with_rsa_sha1_detected | Parse bad_pkgs] ****************************************************************************************************************************
skipping: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_rpms_with_rsa_sha1_detected | Remove bad packages] ***********************************************************************************************************************
skipping: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_vdo_check_needed | Install vdo package] **********************************************************************************************************************************
skipping: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Debug interfaces to rename] **********************************************************************************************************
ok: [192.168.122.115] => {
"msg": []
}
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Update udev rules] *******************************************************************************************************************
skipping: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Check that src_prefix files exists] **************************************************************************************************
skipping: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_partitions_with_noexec | Get all mountpoints with noexec option] *********************************************************************************************************
ok: [192.168.122.113]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Copy ifcfg files using dst_prefix] ***************************************************************************************************
skipping: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_partitions_with_noexec | Go through the the mountpoints and remount] *****************************************************************************************************
skipping: [192.168.122.113]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Edit NAME in new network-script files] ***********************************************************************************************
skipping: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Edit DEVICE in new network-script files] *********************************************************************************************
skipping: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_partitions_with_noexec | Modify /etc/fstab to replace the noexec option] *************************************************************************************************
skipping: [192.168.122.113]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Backup old ifcfg network-script files] ***********************************************************************************************
skipping: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Remove old ifcfg network-script files] ***********************************************************************************************
skipping: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_partitions_with_noexec | Get all mountpoints with noexec option] *********************************************************************************************************
ok: [192.168.122.114]
TASK [infra.leapp.remediate : leapp_partitions_with_noexec | Go through the the mountpoints and remount] *****************************************************************************************************
skipping: [192.168.122.114]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Check that route files exists] *******************************************************************************************************
skipping: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Copy route files using dst_prefix] ***************************************************************************************************
skipping: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_partitions_with_noexec | Modify /etc/fstab to replace the noexec option] *************************************************************************************************
skipping: [192.168.122.114]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Update dst_prefix in route files that use IP command arguments format] ***************************************************************
skipping: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Backup old route files] **************************************************************************************************************
skipping: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Remove old route files] **************************************************************************************************************
skipping: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_remote_using_root | Configure sshd to prohibit-passwords on root login] **************************************************************************************************
changed: [192.168.122.114] => (item={'key': 'PermitRootLogin', 'value': 'prohibit-password'})
TASK [infra.leapp.remediate : leapp_remote_using_root | Configure sshd to prohibit-passwords on root login] **************************************************************************************************
changed: [192.168.122.113] => (item={'key': 'PermitRootLogin', 'value': 'prohibit-password'})
TASK [infra.leapp.remediate : leapp_rpms_with_rsa_sha1_detected | Check that the leapp-report.json exists] ***************************************************************************************************
skipping: [192.168.122.113]
TASK [infra.leapp.remediate : leapp_rpms_with_rsa_sha1_detected | End play if no leapp report exists] ********************************************************************************************************
skipping: [192.168.122.113]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Get a list of all ifcfg files] *******************************************************************************************************
ok: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_rpms_with_rsa_sha1_detected | Read leapp report] *************************************************************************************************************************
skipping: [192.168.122.113]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Perform final regex on ifcfg files] **************************************************************************************************
skipping: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_rpms_with_rsa_sha1_detected | Parse leapp report to json] ****************************************************************************************************************
skipping: [192.168.122.113]
TASK [infra.leapp.remediate : leapp_rpms_with_rsa_sha1_detected | Find matching entries] *********************************************************************************************************************
skipping: [192.168.122.113] => (item={'groups': ['network', 'inhibitor'], 'title': 'Unsupported network configuration', 'timeStamp': '2025-09-14T19:05:16.373921Z', 'hostname': 'db01.kifarunix.com', 'detail': {'external': [{'url': 'https://access.redhat.com/solutions/4067471', 'title': 'How to perform an in-place upgrade to RHEL 8 when using kernel NIC names on RHEL 7'}, {'url': 'https://access.redhat.com/solutions/7009239', 'title': 'RHEL 8 to RHEL 9: inplace upgrade fails at "Network configuration for unsupported device types detected"'}], 'remediations': [{'type': 'hint', 'context': 'Rename all ethX network interfaces following the attached KB solution article.'}]}, 'actor': 'persistentnetnamesdisable', 'summary': 'Detected multiple physical network interfaces where one or more use kernel naming (e.g. eth0). Upgrade process can not continue because stability of names can not be guaranteed. Please read the article at https://access.redhat.com/solutions/4067471 for more information.', 'audience': 'sysadmin', 'key': 'd3050d265759a79ce895e64f45e9c56e49b3a953', 'id': '713dbc223571ebf608d752e56cf94c92846b0ccde9442bccf499d6dd11703ab0', 'severity': 'high'})
skipping: [192.168.122.113] => (item={'groups': ['repository', 'failure'], 'title': 'Excluded target system repositories', 'timeStamp': '2025-09-14T19:05:16.440845Z', 'hostname': 'db01.kifarunix.com', 'detail': {'remediations': [{'type': 'hint', 'context': 'If some of excluded repositories are still required to be used during the upgrade, execute leapp with the --enablerepo option with the repoid of the repository required to be enabled as an argument (the option can be used multiple times).'}]}, 'actor': 'repositories_blacklist', 'summary': 'The following repositories are not supported by Red Hat and are excluded from the list of repositories used during the upgrade.\n- codeready-builder-beta-for-rhel-8-s390x-rpms\n- codeready-builder-beta-for-rhel-8-ppc64le-rpms\n- rhui-codeready-builder-for-rhel-8-x86_64-rhui-rpms\n- codeready-builder-for-rhel-8-aarch64-eus-rpms\n- codeready-builder-for-rhel-8-ppc64le-eus-rpms\n- codeready-builder-beta-for-rhel-8-x86_64-rpms\n- codeready-builder-for-rhel-8-aarch64-rpms\n- codeready-builder-for-rhel-8-s390x-rpms\n- codeready-builder-for-rhel-8-s390x-eus-rpms\n- codeready-builder-for-rhel-8-x86_64-eus-rpms\n- rhui-codeready-builder-for-rhel-8-aarch64-rhui-rpms\n- codeready-builder-beta-for-rhel-8-aarch64-rpms\n- codeready-builder-for-rhel-8-rhui-rpms\n- codeready-builder-for-rhel-8-x86_64-rhui-rpms\n- codeready-builder-for-rhel-8-x86_64-rpms\n- codeready-builder-for-rhel-8-x86_64-eus-rhui-rpms\n- codeready-builder-for-rhel-8-ppc64le-rpms', 'audience': 'sysadmin', 'key': '1b9132cb2362ae7830e48eee7811be9527747de8', 'id': 'df101d8c2318a3155aaddb9389b2770465b064eb7af40f1f1b2a95c3c324ac2c', 'severity': 'info'})
skipping: [192.168.122.113] => (item={'groups': ['repository'], 'title': 'Packages available in excluded repositories will not be installed', 'timeStamp': '2025-09-14T19:05:26.230023Z', 'hostname': 'db01.kifarunix.com', 'detail': {'related_resources': [{'scheme': 'package', 'title': 'python3-pyxattr'}, {'scheme': 'package', 'title': 'rpcgen'}]}, 'actor': 'pes_events_scanner', 'summary': '2 packages will be skipped because they are available only in target system repositories that are intentionally excluded from the list of repositories used during the upgrade. See the report message titled "Excluded target system repositories" for details.\nThe list of these packages:\n- python3-pyxattr (repoid: codeready-builder-for-rhel-8-x86_64-rpms)\n- rpcgen (repoid: codeready-builder-for-rhel-8-x86_64-rpms)', 'audience': 'sysadmin', 'key': '2437e204808f987477c0e9be8e4c95b3a87a9f3e', 'id': '180cbb8d679af19b3ce7bb52416361329fbdee530ef3908e7a5c80dcc326751a', 'severity': 'high'})
skipping: [192.168.122.113] => (item={'groups': ['services', 'email'], 'title': 'Postfix has incompatible changes in the next major version', 'timeStamp': '2025-09-14T19:05:28.915211Z', 'hostname': 'db01.kifarunix.com', 'detail': {'related_resources': [{'scheme': 'package', 'title': 'postfix'}]}, 'actor': 'check_postfix', 'summary': 'Postfix 3.x has so called "compatibility safety net" that runs Postfix programs with backwards-compatible default settings. It will log a warning whenever backwards-compatible default setting may be required for continuity of service. Based on this logging the system administrator can decide if any backwards-compatible settings need to be made permanent in main.cf or master.cf, before turning off the backwards-compatibility safety net.\nThe backward compatibility safety net is by default turned off in Red Hat Enterprise Linux 8.\nIt can be turned on by running: "postconf -e compatibility_level=0\nIt can be turned off by running: "postconf -e compatibility_level=2\n\nIn the Postfix MySQL database client, the default "option_group" value has changed to "client", i.e. it now reads options from the [client] group from the MySQL configuration file. To disable it, set "option_group" to the empty string.\n\nThe postqueue command no longer forces all message arrival times to be reported in UTC. To get the old behavior, set TZ=UTC in main.cf:import_environment.\n\nPostfix 3.2 enables elliptic curve negotiation. This changes the default smtpd_tls_eecdh_grade setting to "auto", and introduces a new parameter "tls_eecdh_auto_curves" with the names of curves that may be negotiated.\n\nThe "master.cf" chroot default value has changed from "y" (yes) to "n" (no). This applies to master.cf services where chroot field is not explicitly specified.\n\nThe "append_dot_mydomain" default value has changed from "yes" to "no". You may need changing it to "yes" if senders cannot use complete domain names in e-mail addresses.\n\nThe "relay_domains" default value has changed from "$mydestination" to the empty value. This could result in unexpected "Relay access denied" errors or ETRN errors, because now will postfix by default relay only for the localhost.\n\nThe "mynetworks_style" default value has changed from "subnet" to "host". This parameter is used to implement the "permit_mynetworks" feature. The change could result in unexpected "access denied" errors, because postfix will now by default trust only the local machine, not the remote SMTP clients on the same IP subnetwork.\n\nPostfix now supports dynamically loaded database plugins. Plugins are shipped in individual RPM sub-packages. Correct database plugins have to be installed, otherwise the specific database client will not work. For example for PostgreSQL map to work, the postfix-pgsql RPM package has to be installed.\n', 'audience': 'sysadmin', 'key': '5721e0a07a67d82cf7e5ea6f17662cd4f82e0a33', 'id': '458db741f010f9f794baaade24bd1dbb0c148582cba09d101ede50e8631036bd', 'severity': 'low'})
skipping: [192.168.122.113] => (item={'groups': ['authentication', 'security', 'tools'], 'title': 'Current PAM and nsswitch.conf configuration will be kept.', 'timeStamp': '2025-09-14T19:05:29.244997Z', 'hostname': 'db01.kifarunix.com', 'detail': {'related_resources': [{'scheme': 'package', 'title': 'authselect'}, {'scheme': 'package', 'title': 'authconfig'}, {'scheme': 'file', 'title': '/etc/nsswitch.conf'}]}, 'actor': 'authselect_check', 'summary': 'There is a new tool called authselect in RHEL8 that replaced authconfig. The upgrade process was unable to find an authselect profile that would be equivalent to your current configuration. Therefore your configuration will be left intact.', 'audience': 'sysadmin', 'key': '40c4ab1da4a30dc1ca40e543f6385e1336d8810c', 'id': 'be1cd7747e9b75de9fb3e3f312000bae551aeb4e3f3fefa81abd23c95173931e', 'severity': 'info'})
skipping: [192.168.122.113] => (item={'groups': ['selinux', 'security'], 'title': 'SElinux relabeling will be scheduled', 'timeStamp': '2025-09-14T19:05:29.846483Z', 'hostname': 'db01.kifarunix.com', 'actor': 'check_se_linux', 'summary': 'SElinux relabeling will be scheduled as the status is permissive/enforcing.', 'audience': 'sysadmin', 'key': '8fb81863f8413bd617c2a55b69b8e10ff03d7c72', 'id': '691e774f3d6024008baf68459dd0eae6fca877ee7080877f62156e5d199e6116', 'severity': 'info'})
skipping: [192.168.122.113] => (item={'groups': ['selinux', 'security'], 'title': 'SElinux will be set to permissive mode', 'timeStamp': '2025-09-14T19:05:29.849799Z', 'hostname': 'db01.kifarunix.com', 'detail': {'remediations': [{'type': 'hint', 'context': 'Make sure there are no SElinux related warnings after the upgrade and enable SElinux manually afterwards. Notice: You can ignore the "/root/tmp_leapp_py3" SElinux warnings.'}]}, 'actor': 'check_se_linux', 'summary': 'SElinux will be set to permissive mode. Current mode: enforcing. This action is required by the upgrade process to make sure the upgraded system can boot without beinig blocked by SElinux rules.', 'audience': 'sysadmin', 'key': '39d7183dafba798aa4bbb1e70b0ef2bbe5b1772f', 'id': '37c825a748e1ff17630f5fb5763a66d7d3d5b13e371fc92f781301356f2e61f4', 'severity': 'low'})
skipping: [192.168.122.113] => (item={'groups': ['tools'], 'title': 'Grep has incompatible changes in the next major version', 'timeStamp': '2025-09-14T19:05:30.037961Z', 'hostname': 'db01.kifarunix.com', 'detail': {'related_resources': [{'scheme': 'package', 'title': 'grep'}], 'remediations': [{'type': 'hint', 'context': 'Please update your scripts to be compatible with the changes.'}]}, 'actor': 'checkgrep', 'summary': 'If a file contains data improperly encoded for the current locale, and this is discovered before any of the file\'s contents are output, grep now treats the file as binary.\nThe \'grep -P\' no longer reports an error and exits when given invalid UTF-8 data. Instead, it considers the data to be non-matching.\nIn locales with multibyte character encodings other than UTF-8, grep -P now reports an error and exits instead of misbehaving.\nWhen searching binary data, grep now may treat non-text bytes as line terminators. This can boost performance significantly.\nThe \'grep -z\' no longer automatically treats the byte \'\\200\' as binary data.\nContext no longer excludes selected lines omitted because of -m. For example, \'grep "^" -m1 -A1\' now outputs the first two input lines, not just the first line.\n', 'audience': 'sysadmin', 'key': '94665a499e2eeee35eca3e7093a7abe183384b16', 'id': '784d95461b6f29da836440f95e2a32c8a62f08f19539cee7c3a37d3e0eeb9a10', 'severity': 'low'})
skipping: [192.168.122.113] => (item={'groups': ['services', 'time management'], 'title': 'chrony using default configuration', 'timeStamp': '2025-09-14T19:05:31.352819Z', 'hostname': 'db01.kifarunix.com', 'detail': {'related_resources': [{'scheme': 'package', 'title': 'ntpd'}, {'scheme': 'package', 'title': 'chrony'}, {'scheme': 'file', 'title': '/etc/chrony.conf'}]}, 'actor': 'check_chrony', 'summary': 'default chrony configuration in RHEL8 uses leapsectz directive, which cannot be used with leap smearing NTP servers, and uses a single pool directive instead of four server directives', 'audience': 'sysadmin', 'key': 'c4222ebd18730a76f6bc7b3b66df898b106e6554', 'id': '871c92c073d90f50aeb7eca8823feef633757cae1a37bbcf454fe87a45e7e7ab', 'severity': 'medium'})
skipping: [192.168.122.113] => (item={'groups': ['services'], 'title': 'Automatic registration into Red Hat Insights', 'timeStamp': '2025-09-14T19:05:31.657640Z', 'hostname': 'db01.kifarunix.com', 'actor': 'check_insights_auto_register', 'summary': "After the upgrade, this system will be automatically registered into Red Hat Insights. The 'insights-client' package required for the registration will be installed during the upgrade. To skip the automatic registration, use the '--no-insights-register' command line option or set the LEAPP_NO_INSIGHTS_REGISTER environment variable.", 'audience': 'sysadmin', 'key': '693963253195f418526f045b6d630a1f4c7a193d', 'id': '01e8e642f1919afeb175f21ae47f2806848d7971fe8970e5248124f896596f95', 'severity': 'info'})
skipping: [192.168.122.113] => (item={'groups': ['authentication', 'security', 'tools'], 'title': 'Module pam_pkcs11 will be removed from PAM configuration', 'timeStamp': '2025-09-14T19:05:31.703394Z', 'hostname': 'db01.kifarunix.com', 'detail': {'related_resources': [{'scheme': 'package', 'title': 'sssd'}], 'remediations': [{'type': 'hint', 'context': 'Configure SSSD to replace pam_pkcs11'}]}, 'actor': 'removed_pam_modules_check', 'summary': 'Module pam_pkcs11 was surpassed by SSSD and therefore it was removed from RHEL-8. Keeping it in PAM configuration may lock out the system thus it will be automatically removed from PAM configuration before upgrading to RHEL-8. Please switch to SSSD to recover the functionality of pam_pkcs11.', 'audience': 'sysadmin', 'key': 'bf47e7305d6805e8bbeaa7593cf01e38030c23f3', 'id': 'b9e5d0ac7d1a88b226abf1a17ce7ee777e87d1cb6cd207b1bd09d22443640015', 'severity': 'medium'})
skipping: [192.168.122.113] => (item={'groups': ['sanity'], 'title': 'Packages not signed by Red Hat found on the system', 'timeStamp': '2025-09-14T19:05:31.975841Z', 'hostname': 'db01.kifarunix.com', 'actor': 'red_hat_signed_rpm_check', 'summary': 'The following packages have not been signed by Red Hat and may be removed during the upgrade process in case Red Hat-signed packages to be removed during the upgrade depend on them:\n- containerd.io\n- docker-buildx-plugin\n- docker-ce\n- docker-ce-cli\n- docker-ce-rootless-extras\n- docker-compose-plugin\n- fuse-overlayfs\n- fuse3-libs\n- slirp4netns', 'audience': 'sysadmin', 'key': '13f0791ae5f19f50e7d0d606fb6501f91b1efb2c', 'id': 'c6e9383c684ff011c5ba35c316ef8f372129868bd4c6c53f32b5f2ee79707dbe', 'severity': 'high'})
skipping: [192.168.122.113] => (item={'groups': ['python'], 'title': 'Difference in Python versions and support in RHEL 8', 'timeStamp': '2025-09-14T19:05:32.383202Z', 'hostname': 'db01.kifarunix.com', 'detail': {'related_resources': [{'scheme': 'package', 'title': 'python'}, {'scheme': 'package', 'title': 'python2'}, {'scheme': 'package', 'title': 'python3'}], 'external': [{'url': 'https://red.ht/rhel-8-python', 'title': 'Difference in Python versions and support in RHEL 8'}], 'remediations': [{'type': 'hint', 'context': 'Please run "alternatives --set python /usr/bin/python3" after upgrade'}]}, 'actor': 'python_inform_user', 'summary': "In RHEL 8, there is no 'python' command. Python 3 (backward incompatible) is the primary Python version and Python 2 is available with limited support and limited set of packages. If you no longer require Python 2 packages following the upgrade, please remove them. Read more here: https://red.ht/rhel-8-python", 'audience': 'developer', 'key': '0c98585b1d8d252eb540bf61560094f3495351f5', 'id': '3d0d02f72396ff7fd871e7609413b84443ce2ca9bd21b1f27856e80ed5720a05', 'severity': 'high'})
skipping: [192.168.122.113] => (item={'groups': ['boot'], 'title': 'GRUB2 core will be automatically updated during the upgrade', 'timeStamp': '2025-09-14T19:05:33.027098Z', 'hostname': 'db01.kifarunix.com', 'actor': 'check_grub_core', 'summary': 'On legacy (BIOS) systems, GRUB2 core (located in the gap between the MBR and the first partition) cannot be updated during the rpm transaction and Leapp has to initiate the update running "grub2-install" after the transaction. No action is needed before the upgrade. After the upgrade, it is recommended to check the GRUB configuration.', 'audience': 'sysadmin', 'key': 'ac7030e05d2ee248d34f08a9fa040b352bc410a3', 'id': '4a78ee397dc2f8eb59f229f79f925774f9ca6b3b8294af2d037fcf471582307e', 'severity': 'high'})
skipping: [192.168.122.113]
TASK [infra.leapp.remediate : leapp_rpms_with_rsa_sha1_detected | End execution of playbook if no entry found in leapp report] *******************************************************************************
skipping: [192.168.122.113]
TASK [infra.leapp.remediate : leapp_rpms_with_rsa_sha1_detected | Parse bad_pkgs] ****************************************************************************************************************************
skipping: [192.168.122.113]
TASK [infra.leapp.remediate : leapp_rpms_with_rsa_sha1_detected | Remove bad packages] ***********************************************************************************************************************
skipping: [192.168.122.113]
TASK [infra.leapp.remediate : leapp_rpms_with_rsa_sha1_detected | Check that the leapp-report.json exists] ***************************************************************************************************
ok: [192.168.122.114]
TASK [infra.leapp.remediate : leapp_vdo_check_needed | Install vdo package] **********************************************************************************************************************************
skipping: [192.168.122.113]
TASK [infra.leapp.remediate : leapp_rpms_with_rsa_sha1_detected | End play if no leapp report exists] ********************************************************************************************************
skipping: [192.168.122.114]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Debug interfaces to rename] **********************************************************************************************************
ok: [192.168.122.113] => {
"msg": [
"eth0",
"eth1"
]
}
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Check if undercloud.conf exists] *****************************************************************************************************
ok: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Replace interface name in undercloud.conf] *******************************************************************************************
skipping: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_rpms_with_rsa_sha1_detected | Read leapp report] *************************************************************************************************************************
ok: [192.168.122.114]
TASK [infra.leapp.remediate : leapp_rpms_with_rsa_sha1_detected | Parse leapp report to json] ****************************************************************************************************************
ok: [192.168.122.114]
TASK [infra.leapp.remediate : leapp_rpms_with_rsa_sha1_detected | Find matching entries] *********************************************************************************************************************
skipping: [192.168.122.114] => (item={'audience': 'sysadmin', 'detail': {'remediations': [{'context': 'If some of excluded repositories are still required to be used during the upgrade, execute leapp with the --enablerepo option with the repoid of the repository required to be enabled as an argument (the option can be used multiple times).', 'type': 'hint'}]}, 'groups': ['repository', 'failure'], 'key': '1b9132cb2362ae7830e48eee7811be9527747de8', 'severity': 'info', 'summary': 'The following repositories are not supported by Red Hat and are excluded from the list of repositories used during the upgrade.\n- codeready-builder-beta-for-rhel-9-x86_64-rpms\n- codeready-builder-beta-for-rhel-9-aarch64-rpms\n- codeready-builder-for-rhel-9-aarch64-eus-rpms\n- rhui-codeready-builder-for-rhel-9-aarch64-rhui-rpms\n- codeready-builder-beta-for-rhel-9-s390x-rpms\n- codeready-builder-for-rhel-9-rhui-rpms\n- codeready-builder-for-rhel-9-ppc64le-rpms\n- codeready-builder-for-rhel-9-x86_64-eus-rpms\n- codeready-builder-beta-for-rhel-9-ppc64le-rpms\n- codeready-builder-for-rhel-9-ppc64le-eus-rpms\n- codeready-builder-for-rhel-9-x86_64-rhui-rpms\n- codeready-builder-for-rhel-9-x86_64-rpms\n- rhui-codeready-builder-for-rhel-9-x86_64-rhui-rpms\n- codeready-builder-for-rhel-9-aarch64-rpms\n- codeready-builder-for-rhel-9-s390x-eus-rpms\n- codeready-builder-for-rhel-9-s390x-rpms', 'title': 'Excluded target system repositories', 'timeStamp': '2025-09-14T19:05:26.043394Z', 'hostname': 'app01.kifarunix.com', 'actor': 'repositories_blacklist', 'id': 'a09f821d262b79436575a05730f92bb04e849378c9223fae4c955f5d0f11eda5'})
skipping: [192.168.122.114] => (item={'audience': 'sysadmin', 'groups': ['boot'], 'key': 'ac7030e05d2ee248d34f08a9fa040b352bc410a3', 'severity': 'high', 'summary': 'On legacy (BIOS) systems, GRUB2 core (located in the gap between the MBR and the first partition) cannot be updated during the rpm transaction and Leapp has to initiate the update running "grub2-install" after the transaction. No action is needed before the upgrade. After the upgrade, it is recommended to check the GRUB configuration.', 'title': 'GRUB2 core will be automatically updated during the upgrade', 'timeStamp': '2025-09-14T19:05:36.887091Z', 'hostname': 'app01.kifarunix.com', 'actor': 'check_grub_core', 'id': 'b3502b5d6b2885f591a946892d9d6d8e55b832395ada5b02593f0d5a0c4f5ec3'})
skipping: [192.168.122.114] => (item={'audience': 'sysadmin', 'groups': ['kernel', 'drivers'], 'key': 'b03c306f274b33b4cf3c7cd3764366c599681481', 'severity': 'high', 'summary': 'The following RHEL 8 device drivers are no longer maintained RHEL 9:\n - ip_set\n', 'title': 'Leapp detected loaded kernel drivers which are no longer maintained in RHEL 9.', 'timeStamp': '2025-09-14T19:05:38.025716Z', 'hostname': 'app01.kifarunix.com', 'actor': 'check_detected_devices_and_drivers', 'id': '44b1b382f69da71a93bdb28907bff17db461538ae093bb69849130670ee18a6c'})
skipping: [192.168.122.114] => (item={'audience': 'sysadmin', 'groups': ['services'], 'key': '693963253195f418526f045b6d630a1f4c7a193d', 'severity': 'info', 'summary': "After the upgrade, this system will be automatically registered into Red Hat Insights. To skip the automatic registration, use the '--no-insights-register' command line option or set the LEAPP_NO_INSIGHTS_REGISTER environment variable.", 'title': 'Automatic registration into Red Hat Insights', 'timeStamp': '2025-09-14T19:05:38.519741Z', 'hostname': 'app01.kifarunix.com', 'actor': 'check_insights_auto_register', 'id': '9eb4184eb1a350d6e35a18f43cb4fe3d1463a2f75a429d1022318c38e86d5651'})
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Check if os-net-config's config.json exists] *****************************************************************************************
ok: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_rpms_with_rsa_sha1_detected | Find matching entries] *********************************************************************************************************************
skipping: [192.168.122.114] => (item={'audience': 'sysadmin', 'detail': {'external': [{'title': 'Handling the migration of your custom and third-party applications', 'url': 'https://red.ht/customize-rhel-upgrade-actors'}], 'remediations': [{'context': 'The most simple solution that does not require additional knowledge about the upgrade process is the uninstallation of such packages before the upgrade and installing these (or their newer versions compatible with the target system) back after the upgrade. Also you can just try to upgrade the system on a testing machine (or after the full system backup) to see the result.\nHowever, it is common use case to migrate or upgrade installed third party packages together with the system during the in-place upgrade process. To examine how to customize the process to deal with such packages, follow the documentation in the attached link for more details.', 'type': 'hint'}]}, 'groups': ['sanity'], 'key': '13f0791ae5f19f50e7d0d606fb6501f91b1efb2c', 'severity': 'high', 'summary': 'The following packages have not been signed by Red Hat and may be removed during the upgrade process in case Red Hat-signed packages to be removed during the upgrade depend on them:\n- docker-buildx-plugin\n- docker-ce-cli\n- docker-compose-plugin', 'title': 'Packages not signed by Red Hat found on the system', 'timeStamp': '2025-09-14T19:05:38.596490Z', 'hostname': 'app01.kifarunix.com', 'actor': 'red_hat_signed_rpm_check', 'id': '78a1f4f1bfdc02527e386d0f1a3b7358fba1592ee4ae5ce7b99acc58561a5851'})
skipping: [192.168.122.114] => (item={'audience': 'sysadmin', 'detail': {'external': [{'title': 'Why Leapp Preupgrade for RHEL 8 to 9 getting "Possible problems with remote login using root account" ?', 'url': 'https://access.redhat.com/solutions/7003083'}], 'related_resources': [{'scheme': 'package', 'title': 'openssh-server'}, {'scheme': 'file', 'title': '/etc/ssh/sshd_config'}], 'remediations': [{'context': 'If you depend on remote root logins using passwords, consider setting up a different user for remote administration or adding a comment into the sshd_config next to the "PermitRootLogin yes" directive to prevent rpm replacing it during the upgrade.', 'type': 'hint'}]}, 'groups': ['authentication', 'security', 'network', 'services', 'inhibitor'], 'key': '3d21e8cc9e1c09dc60429de7716165787e99515f', 'severity': 'high', 'summary': 'OpenSSH configuration file will get updated to RHEL9 version, no longer allowing root login with password. It is a good practice to use non-root administrative user and non-password authentications, but if you rely on the remote root login, this change can lock you out of this system.', 'title': 'Possible problems with remote login using root account', 'timeStamp': '2025-09-14T19:05:39.703699Z', 'hostname': 'app01.kifarunix.com', 'actor': 'openssh_permit_root_login', 'id': 'd395c016d16d65386835be02ce83705ecdc9eb38913cf68a98e1318d884d05c0'})
skipping: [192.168.122.114] => (item={'audience': 'sysadmin', 'detail': {'related_resources': [{'scheme': 'package', 'title': 'openssh-server'}, {'scheme': 'file', 'title': '/etc/ssh/sshd_config'}], 'remediations': [{'context': 'If you depend on remote root logins using passwords, consider setting up a different user for remote administration. Otherwise you can ignore this message.', 'type': 'hint'}]}, 'groups': ['authentication', 'security', 'network', 'services'], 'key': 'e738f78bc8f3a84411a4210e3b609057139d1855', 'severity': 'high', 'summary': 'RHEL9 no longer allows remote root logins, but the server configuration explicitly overrides this default. The configuration file will not be updated and root is still going to be allowed to login with password. This is not recommended and considered as a security risk.', 'title': 'Remote root logins globally allowed using password', 'timeStamp': '2025-09-14T19:05:39.705497Z', 'hostname': 'app01.kifarunix.com', 'actor': 'openssh_permit_root_login', 'id': '206f047e53bad8e749086b50e844bfc63593b406a3d52644d1c97fea26768430'})
skipping: [192.168.122.114] => (item={'audience': 'sysadmin', 'groups': ['selinux', 'security'], 'key': '8fb81863f8413bd617c2a55b69b8e10ff03d7c72', 'severity': 'info', 'summary': 'SElinux relabeling will be scheduled as the status is permissive/enforcing.', 'title': 'SElinux relabeling will be scheduled', 'timeStamp': '2025-09-14T19:05:40.301828Z', 'hostname': 'app01.kifarunix.com', 'actor': 'check_se_linux', 'id': 'b3c51ebc4ab4cecabed84b188aa4b415c02279b9f808b45e1b2ddced7fceda9a'})
skipping: [192.168.122.114]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Replace interface name in config.json] ***********************************************************************************************
skipping: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_rpms_with_rsa_sha1_detected | End execution of playbook if no entry found in leapp report] *******************************************************************************
fatal: [192.168.122.114]: FAILED! => {"ansible_facts": {"leapp_report_missing": true}, "changed": false, "failed_when_result": true}
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Reboot system to apply network interface changes] ************************************************************************************
skipping: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Update udev rules] *******************************************************************************************************************
changed: [192.168.122.113] => (item=eth0)
TASK [infra.leapp.remediate : leapp_rpms_with_rsa_sha1_detected | Continue when leapp report is missing] *****************************************************************************************************
skipping: [192.168.122.114]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Update udev rules] *******************************************************************************************************************
changed: [192.168.122.113] => (item=eth1)
RUNNING HANDLER [infra.leapp.remediate : Restart sshd] *******************************************************************************************************************************************************
changed: [192.168.122.115]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Check that src_prefix files exists] **************************************************************************************************
ok: [192.168.122.113] => (item=eth0)
ok: [192.168.122.113] => (item=eth1)
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Copy ifcfg files using dst_prefix] ***************************************************************************************************
changed: [192.168.122.113] => (item=eth0)
changed: [192.168.122.113] => (item=eth1)
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Edit NAME in new network-script files] ***********************************************************************************************
changed: [192.168.122.113] => (item=eth0)
changed: [192.168.122.113] => (item=eth1)
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Edit DEVICE in new network-script files] *********************************************************************************************
changed: [192.168.122.113] => (item=eth0)
changed: [192.168.122.113] => (item=eth1)
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Backup old ifcfg network-script files] ***********************************************************************************************
changed: [192.168.122.113] => (item=eth0)
changed: [192.168.122.113] => (item=eth1)
TASK [infra.leapp.remediate : leapp_vdo_check_needed | Install vdo package] **********************************************************************************************************************************
ok: [192.168.122.114]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Debug interfaces to rename] **********************************************************************************************************
ok: [192.168.122.114] => {
"msg": []
}
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Update udev rules] *******************************************************************************************************************
skipping: [192.168.122.114]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Check that src_prefix files exists] **************************************************************************************************
skipping: [192.168.122.114]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Copy ifcfg files using dst_prefix] ***************************************************************************************************
skipping: [192.168.122.114]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Edit NAME in new network-script files] ***********************************************************************************************
skipping: [192.168.122.114]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Edit DEVICE in new network-script files] *********************************************************************************************
skipping: [192.168.122.114]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Backup old ifcfg network-script files] ***********************************************************************************************
skipping: [192.168.122.114]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Remove old ifcfg network-script files] ***********************************************************************************************
skipping: [192.168.122.114]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Check that route files exists] *******************************************************************************************************
skipping: [192.168.122.114]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Remove old ifcfg network-script files] ***********************************************************************************************
changed: [192.168.122.113] => (item=eth0)
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Copy route files using dst_prefix] ***************************************************************************************************
skipping: [192.168.122.114]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Update dst_prefix in route files that use IP command arguments format] ***************************************************************
skipping: [192.168.122.114]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Backup old route files] **************************************************************************************************************
skipping: [192.168.122.114]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Remove old route files] **************************************************************************************************************
skipping: [192.168.122.114]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Get a list of all ifcfg files] *******************************************************************************************************
ok: [192.168.122.114]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Perform final regex on ifcfg files] **************************************************************************************************
skipping: [192.168.122.114]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Remove old ifcfg network-script files] ***********************************************************************************************
changed: [192.168.122.113] => (item=eth1)
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Check if undercloud.conf exists] *****************************************************************************************************
ok: [192.168.122.114]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Replace interface name in undercloud.conf] *******************************************************************************************
skipping: [192.168.122.114]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Check that route files exists] *******************************************************************************************************
ok: [192.168.122.113] => (item=eth0)
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Check if os-net-config's config.json exists] *****************************************************************************************
ok: [192.168.122.114]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Replace interface name in config.json] ***********************************************************************************************
skipping: [192.168.122.114]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Reboot system to apply network interface changes] ************************************************************************************
skipping: [192.168.122.114]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Check that route files exists] *******************************************************************************************************
ok: [192.168.122.113] => (item=eth1)
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Copy route files using dst_prefix] ***************************************************************************************************
skipping: [192.168.122.113] => (item=eth0)
skipping: [192.168.122.113] => (item=eth1)
skipping: [192.168.122.113]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Update dst_prefix in route files that use IP command arguments format] ***************************************************************
skipping: [192.168.122.113] => (item=eth0)
skipping: [192.168.122.113] => (item=eth1)
skipping: [192.168.122.113]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Backup old route files] **************************************************************************************************************
skipping: [192.168.122.113] => (item=eth0)
skipping: [192.168.122.113] => (item=eth1)
skipping: [192.168.122.113]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Remove old route files] **************************************************************************************************************
skipping: [192.168.122.113] => (item=eth0)
skipping: [192.168.122.113] => (item=eth1)
skipping: [192.168.122.113]
RUNNING HANDLER [infra.leapp.remediate : Restart sshd] *******************************************************************************************************************************************************
changed: [192.168.122.114]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Get a list of all ifcfg files] *******************************************************************************************************
ok: [192.168.122.113]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Perform final regex on ifcfg files] **************************************************************************************************
ok: [192.168.122.113] => (item=eth0 -> /etc/sysconfig/network-scripts/ifcfg-lo)
ok: [192.168.122.113] => (item=eth1 -> /etc/sysconfig/network-scripts/ifcfg-lo)
ok: [192.168.122.113] => (item=eth0 -> /etc/sysconfig/network-scripts/ifcfg-em0)
ok: [192.168.122.113] => (item=eth1 -> /etc/sysconfig/network-scripts/ifcfg-em0)
ok: [192.168.122.113] => (item=eth0 -> /etc/sysconfig/network-scripts/ifcfg-em1)
ok: [192.168.122.113] => (item=eth1 -> /etc/sysconfig/network-scripts/ifcfg-em1)
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Check if undercloud.conf exists] *****************************************************************************************************
ok: [192.168.122.113]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Replace interface name in undercloud.conf] *******************************************************************************************
skipping: [192.168.122.113] => (item=eth0)
skipping: [192.168.122.113] => (item=eth1)
skipping: [192.168.122.113]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Check if os-net-config's config.json exists] *****************************************************************************************
ok: [192.168.122.113]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Replace interface name in config.json] ***********************************************************************************************
skipping: [192.168.122.113] => (item=eth0)
skipping: [192.168.122.113] => (item=eth1)
skipping: [192.168.122.113]
TASK [infra.leapp.remediate : leapp_unsupported_network_configuration | Reboot system to apply network interface changes] ************************************************************************************
changed: [192.168.122.113]
RUNNING HANDLER [infra.leapp.remediate : Restart sshd] *******************************************************************************************************************************************************
changed: [192.168.122.113]
PLAY RECAP ***************************************************************************************************************************************************************************************************
192.168.122.113 : ok=34 changed=9 unreachable=0 failed=0 skipped=34 rescued=2 ignored=0
192.168.122.114 : ok=31 changed=2 unreachable=0 failed=0 skipped=28 rescued=4 ignored=0
192.168.122.115 : ok=24 changed=2 unreachable=0 failed=0 skipped=44 rescued=2 ignored=0
And the identified inhibitors have been fixed!
Ensure all inhibitors are resolved before you can proceed. You can rerun the analysis playbook to counter check this.
4. [Optional] Rerun Pre-Upgrade Analysis
You may re-execute the pre-upgrade analysis playbook to verify that all previous issues and upgrade inhibitors have been resolved.
ansible-playbook -i inventory/rhel playbooks/analysis.ymlSample output of our rerun:
...
RUNNING HANDLER [infra.leapp.analysis : Preupgrade analysis report is done] **********************************************************************************************************************************
ok: [192.168.122.115] => {
"msg": "The preupgrade analysis report generation is now complete. SUCCESS: No inhibitors found. Review the tasks above or the result file at /var/log/leapp/leapp-report.txt."
}
...
RUNNING HANDLER [infra.leapp.analysis : Preupgrade analysis report is done] **********************************************************************************************************************************
ok: [192.168.122.113] => {
"msg": "The preupgrade analysis report generation is now complete. SUCCESS: No inhibitors found. Review the tasks above or the result file at /var/log/leapp/leapp-report.txt."
}
...
RUNNING HANDLER [infra.leapp.analysis : Preupgrade analysis report is done] **********************************************************************************************************************************
ok: [192.168.122.114] => {
"msg": "The preupgrade analysis report generation is now complete. SUCCESS: No inhibitors found. Review the tasks above or the result file at /var/log/leapp/leapp-report.txt."
}
PLAY RECAP ***************************************************************************************************************************************************************************************************
192.168.122.113 : ok=32 changed=8 unreachable=0 failed=0 skipped=11 rescued=0 ignored=0
192.168.122.114 : ok=32 changed=8 unreachable=0 failed=0 skipped=11 rescued=0 ignored=0
192.168.122.115 : ok=32 changed=8 unreachable=0 failed=0 skipped=11 rescued=0 ignored=0
5. OS Upgrade Execution
This is the step where you now uttilize the infra.leapp upgrade role to perform the actual RHEL OS upgrade, handling system reboots and post-upgrade validation automatically.
ansible-playbook -i inventory/rhel playbooks/upgrade.ymlIf all goes well, your OS should be upgraded successfully.
Here is our upgrade truncated output:
PLAY [Upgrade] ***********************************************************************************************************************************************************************************************
TASK [Gathering Facts] ***************************************************************************************************************************************************************************************
ok: [192.168.122.115]
TASK [Set OS-specific variables for Leapp upgrade] ***********************************************************************************************************************************************************
ok: [192.168.122.115]
TASK [Gathering Facts] ***************************************************************************************************************************************************************************************
ok: [192.168.122.114]
TASK [Set OS-specific variables for Leapp upgrade] ***********************************************************************************************************************************************************
ok: [192.168.122.114]
TASK [common : Log directory exists] *************************************************************************************************************************************************************************
ok: [192.168.122.115]
TASK [Gathering Facts] ***************************************************************************************************************************************************************************************
ok: [192.168.122.113]
TASK [Set OS-specific variables for Leapp upgrade] ***********************************************************************************************************************************************************
ok: [192.168.122.113]
...
TASK [upgrade : leapp-upgrade | Start Leapp OS upgrade] ******************************************************************************************************************************************************
changed: [192.168.122.115]
ASYNC POLL on 192.168.122.114: jid=j656917469975.38434 started=1 finished=0
ASYNC POLL on 192.168.122.113: jid=j514413364155.3560 started=1 finished=0
ASYNC OK on 192.168.122.114: jid=j656917469975.38434
TASK [upgrade : leapp-upgrade | Start Leapp OS upgrade] ******************************************************************************************************************************************************
changed: [192.168.122.114]
ASYNC OK on 192.168.122.113: jid=j514413364155.3560
TASK [upgrade : leapp-upgrade | Start Leapp OS upgrade] ******************************************************************************************************************************************************
changed: [192.168.122.113]
TASK [upgrade : leapp-upgrade | Reboot to continue Leapp OS upgrade] *****************************************************************************************************************************************
changed: [192.168.122.115]
...
TASK [upgrade : upgrade-validation | Validate current OS major version] **************************************************************************************************************************************
ok: [192.168.122.115] => {
"changed": false,
"msg": "Current OS version is 10.0."
}
TASK [upgrade : upgrade-validation | Validate running kernel matches OS version] *****************************************************************************************************************************
ok: [192.168.122.115] => {
"changed": false,
"msg": "Current kernel version is 6.12.0-55.30.1.el10_0.x86_64."
}
...
TASK [upgrade : upgrade-validation | Validate current OS major version] **************************************************************************************************************************************
ok: [192.168.122.113] => {
"changed": false,
"msg": "Current OS version is 8.10."
}
TASK [upgrade : upgrade-validation | Validate running kernel matches OS version] *****************************************************************************************************************************
ok: [192.168.122.113] => {
"changed": false,
"msg": "Current kernel version is 4.18.0-553.72.1.el8_10.x86_64."
}
...
TASK [upgrade : upgrade-validation | Validate current OS major version] **************************************************************************************************************************************
ok: [192.168.122.114] => {
"changed": false,
"msg": "Current OS version is 9.6."
}
TASK [upgrade : upgrade-validation | Validate running kernel matches OS version] *****************************************************************************************************************************
ok: [192.168.122.114] => {
"changed": false,
"msg": "Current kernel version is 5.14.0-570.39.1.el9_6.x86_64."
}
...
RUNNING HANDLER [upgrade : RIPU in-place OS upgrade is done] *************************************************************************************************************************************************
ok: [192.168.122.113] => {
"msg": "The in-place OS upgrade is now complete. Engage partner teams to begin application validation."
}
...
RUNNING HANDLER [upgrade : RIPU in-place OS upgrade is done] *************************************************************************************************************************************************
ok: [192.168.122.114] => {
"msg": "The in-place OS upgrade is now complete. Engage partner teams to begin application validation."
}
PLAY RECAP ***************************************************************************************************************************************************************************************************
192.168.122.113 : ok=87 changed=20 unreachable=0 failed=0 skipped=26 rescued=0 ignored=1
192.168.122.114 : ok=83 changed=19 unreachable=0 failed=0 skipped=30 rescued=0 ignored=1
192.168.122.115 : ok=52 changed=13 unreachable=0 failed=1 skipped=20 rescued=0 ignored=1
The OSes will be rebooted after the upgrade.
This is the state of the OS release version after upgrades in my example infra:
[kifarunix@db01 ~]$ cat /etc/redhat-release
Red Hat Enterprise Linux release 8.10 (Ootpa)[kifarunix@app01 ~]$ cat /etc/redhat-release
Red Hat Enterprise Linux release 9.6 (Plow)[kifarunix@lb01 ~]$ cat /etc/redhat-release
Red Hat Enterprise Linux release 10.0 (Coughlan)If you check on the console, you may see the upgrade report.
See example console for the upgraded rhel 9, now running RHEL 10.0:
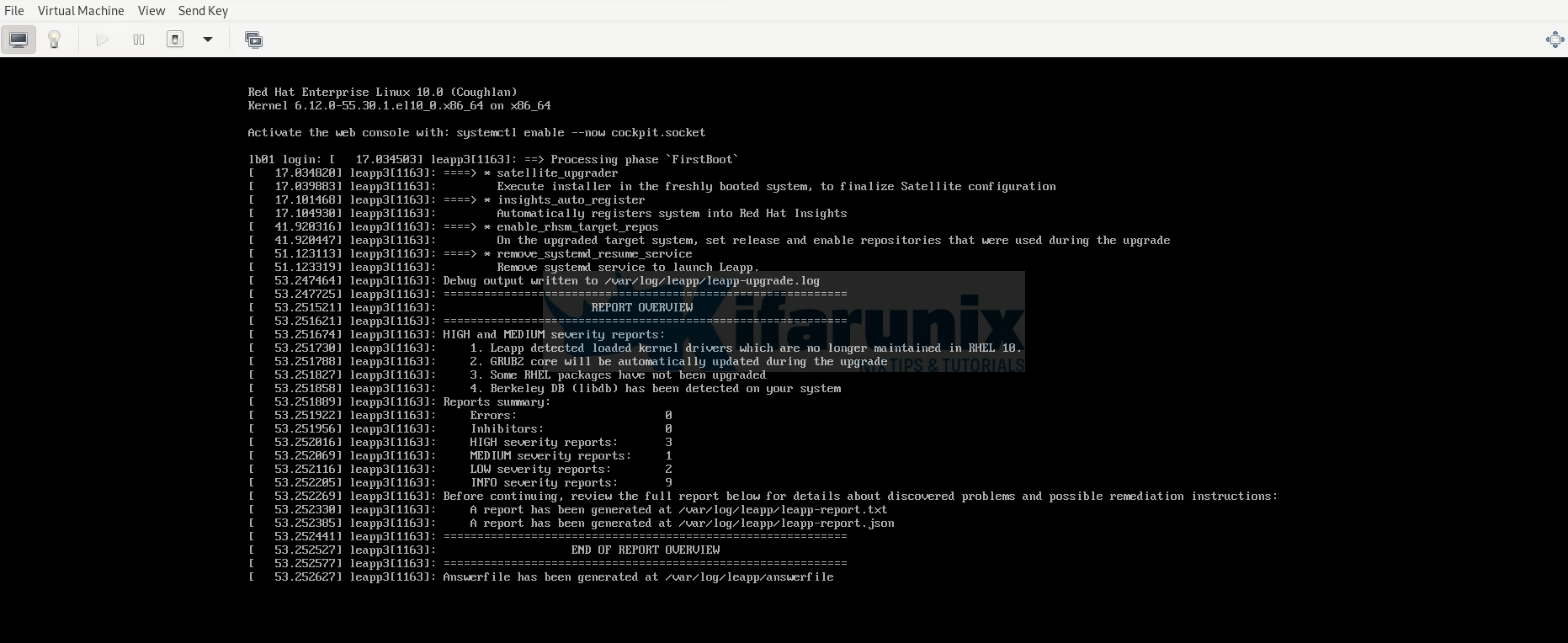
Simillary, the playbooks will run post-upgrade clean up and remove old kernels, no current OS packages...
See the grub menu for the upgraded RHEL 9.4, now RHEL 10.0;
Run Post OS Upgrade Validation
Just like the upgrade playbook prompts you at the final step after the OS upgrade has completed successfully, it's time to shift focus to validating your applications.
RUNNING HANDLER [upgrade : RIPU in-place OS upgrade is done] *************************************************************************************************************************************************
ok: [192.168.122.114] => {
"msg": "The in-place OS upgrade is now complete. Engage partner teams to begin application validation."The message above is your cue. This is not just a formality. Post-upgrade validation is critical to ensure that all application components are functioning as expected on the new OS version. At this stage, partner or application owner teams should verify service start-up, data integrity, integrations, and any performance baselines to catch regressions early. Skipping or rushing this phase can leave hidden issues that surface only in production. Take the time to do it right.
In our next guide, we will see how you can use Ansible Automation Platform (AAP) or AWX to create RHEL OS upgrade automation workflows.
Use Ansible Automation Platform
You can use AAP to automate the OS upgrades:
How to Automate RHEL OS Upgrades Using Ansible Automation Platform (AAP)
Conclusion
That marks the end of our guide on how to automate RHEL OS upgrades using Ansible infra.leapp playbooks. Using the infra.leapp Ansible collection to automate RHEL OS upgrades simplifies the process, reduces risk, and improves consistency across systems. With proper preparation, customization, and version control, you can confidently manage upgrades at scale while staying aligned with Red Hat’s best practices.

