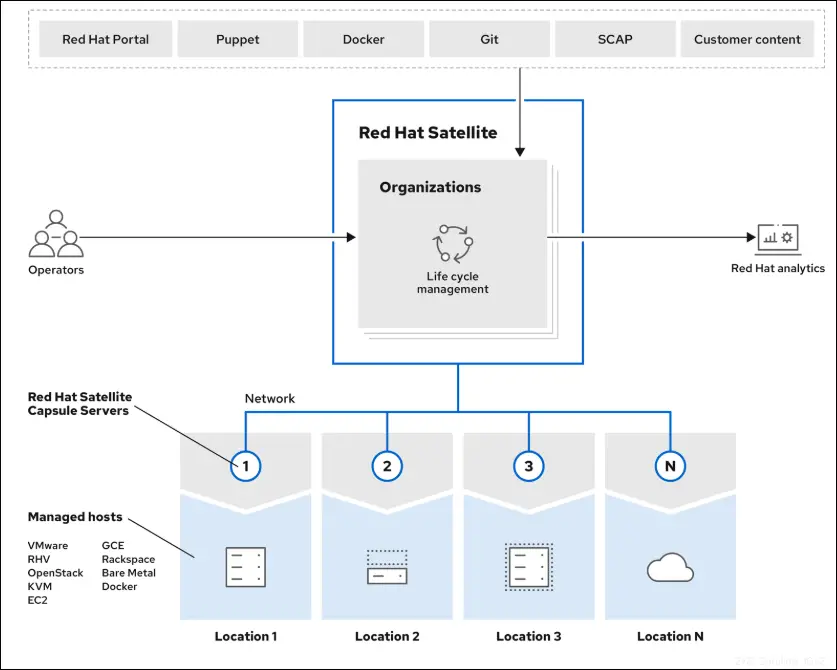
Understanding Red Hat Satellite: A Detailed Guide to Its Architecture and Key Features
In this guide, we’ll explore what Red Hat Satellite is, its key features and how its architecture enables centralized control, automation, and scalability. Managing a