
In this tutorial, you will learn how to install and configure FreeIPA client on Ubuntu 24.04. With FreeIPA client, you can be able to authenticate against your central authentication FreeIPA server making it easier to manage user accounts, passwords, and access rights across a network of systems.
Table of Contents
Install and Configure FreeIPA Client on Ubuntu 24.04
Install and Setup FreeIPA Server
Before you can proceed, you need to have a running FreeIPA server.
Install and Setup FreeIPA Server
Add User Accounts to FreeIPA Server
Once the server is up and running, add user accounts.
Add FreeIPA User Accounts via CLI or Web Interface
Add Client DNS Record to FreeIPA Server
If you configured your FreeIPA Server with integrated DNS, you need to add the client’s A record details on the server. Note: In our FreeIPA server, I didnt setup integrated DNS so I am skipping this step. But just in case you enabled the option, then this is how you can add the record.
From CLI
ipa dnsrecord-add <domain> <hostname> --a-rec=<IP-address>For example, to add an A record for the halo.kifarunix.com on FreeIPA CLI;
ipa dnsrecord-add kifarunix.com halo --a-rec=10.10.20.35From Web UI:
- Log in to the FreeIPA web interface (
https://<your-ipa-server>/ipa/ui) - Navigate to:
Network Services → DNS → DNS Zones - Select your domain zone (e.g.,
example.com) - Click Add → Add Record
- Choose A Record and fill in:
- Hostname (e.g.,
haloforhalo.example.com) - IP Address (the client’s static IP)
- Hostname (e.g.,
- Click Add to save.
Verifying the Record
ipa dnsrecord-show <domain> <hostname>
Update Client and FreeIPA Server DNS Records on the Client Node
If you are using an integrated DNS on your FreeIPA server and your client is already configured to use it for as DNS server, then you should be able to resolve both the server and the client addresses.
However, if you did not set the DNS server, you can use the hosts file on the client to set the records.
For example, to add FreeIPA server records on the Client hosts file
echo "192.168.122.110 freeipa.kifarunix.com" | sudo tee -a /etc/hostsSimilarly, update the client DNS records;
echo "192.168.122.40 noble.kifarunix.com noble" | sudo tee -a /etc/hostsIf you hostname was already resolving to the loopback address, update the hosts file accordingly to remove that record.
Install FreeIPA Client on Ubuntu 24.04
You are now ready to install FreeIPA client on your Ubuntu system for central authentication via the FreeIPA server.
Run the command below to install FreeIPA client and other required packages.
sudo apt install freeipa-client oddjob-mkhomedir- freeipa-client provide tools required to configure a system as FreeIPA server client.
- oddjob-mkhomedir package provides PAM module, that enables automatic home directories creation for users when they first log in to a system
During installation, you will be prompted to set your Kerberos realm, an administrative domain in which the Kerberos authentication service operates.
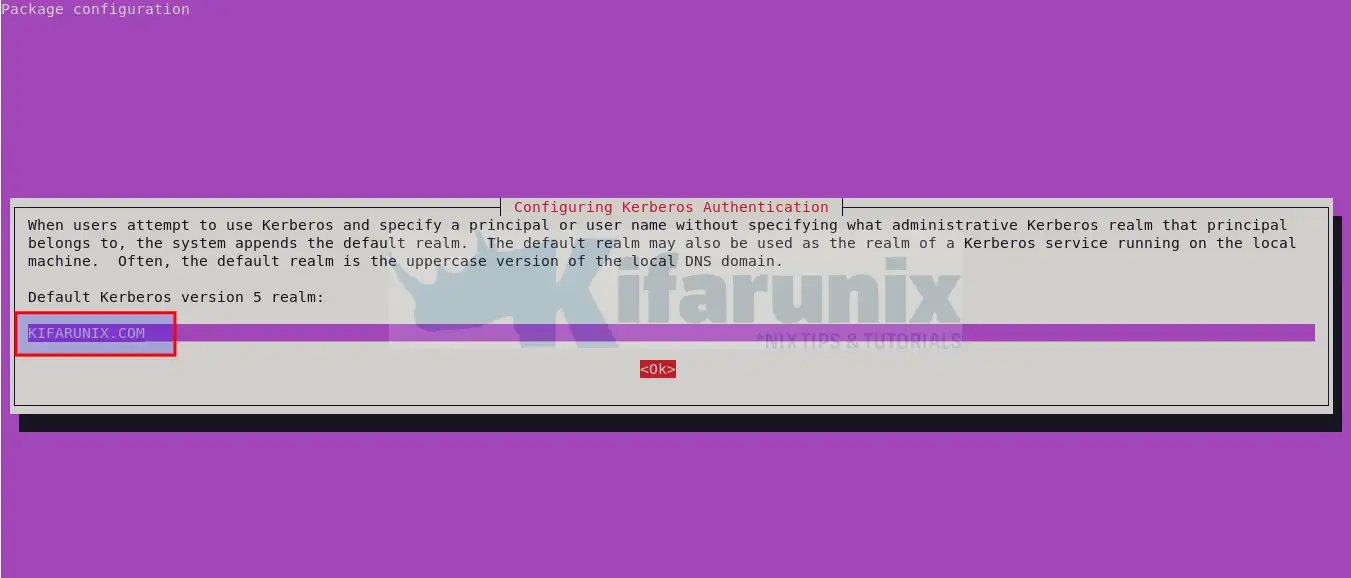
Press tab to select Okay and proceed. Otherwise, update the realm domain and press Okay to proceed.
Also, set the FreeIPA server FQDN address and proceed.
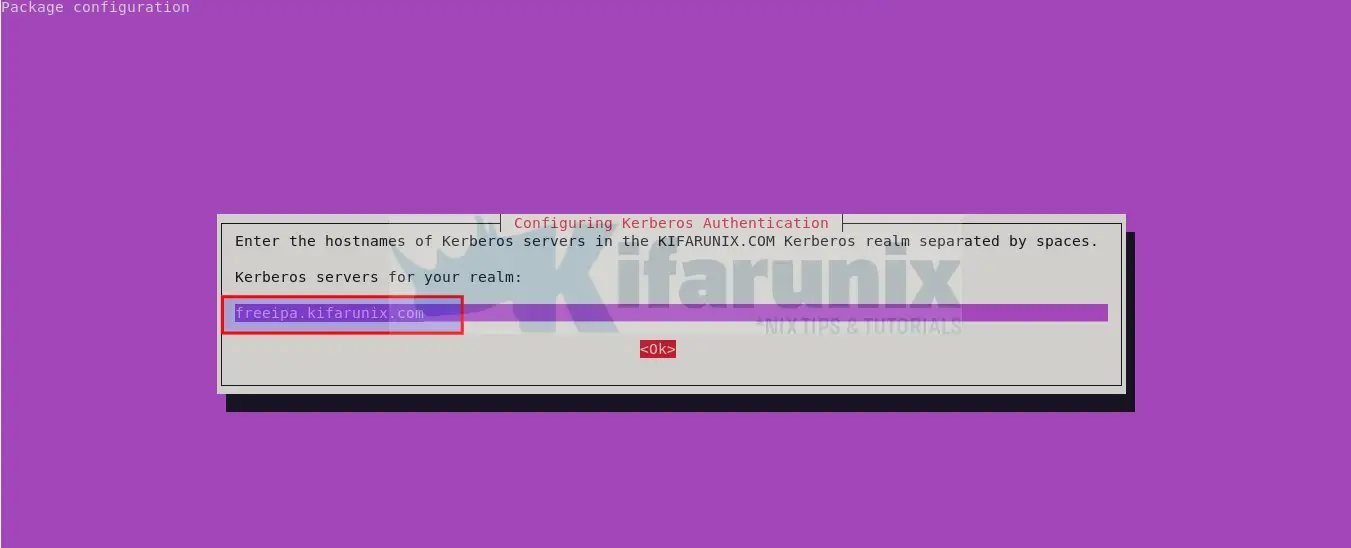
For the administrative server for your Kerberos realm, use the same FreeIPA server FQDN.
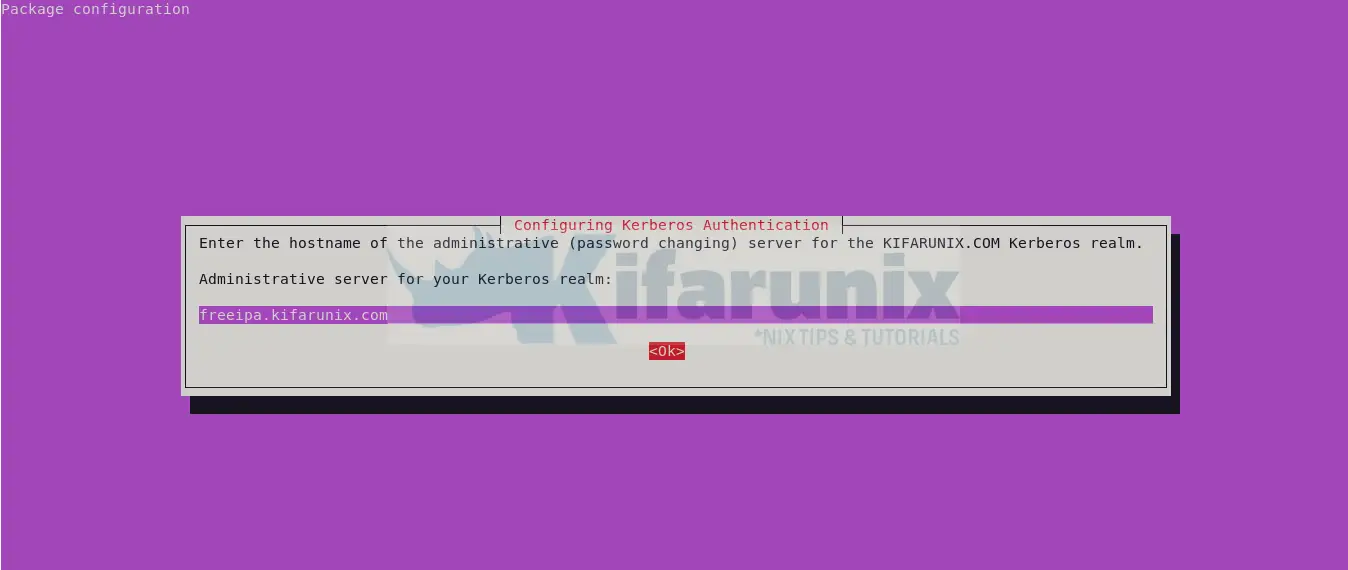
Configure FreeIPA Client to authenticate via FreeIPA Server
The FreeIPA client installed above, ships with a number of IPA tools that can be use to manage and configure the client for authentication against the FreeIPA server. Among the tools installed is the ipa-client-install command.
ipa-client-install command configures a client machine to use IPA for authentication and identity services. By default this configures SSSD to connect to an IPA server for authentication and authorization.
You can see how to use this command via man page or help info;
ipa-client-install --helpUsage: ipa-client-install [options]
Options:
--version show program's version number and exit
-h, --help show this help message and exit
-U, --unattended unattended (un)installation never prompts the user
--uninstall uninstall an existing installation. The uninstall can
be run with --unattended option
Basic options:
-p PRINCIPAL, --principal=PRINCIPAL
principal to use to join the IPA realm
--ca-cert-file=FILE
load the CA certificate from this file
--ip-address=IP_ADDRESS
Specify IP address that should be added to DNS. This
option can be used multiple times
--all-ip-addresses All routable IP addresses configured on any interface
will be added to DNS
--domain=DOMAIN_NAME
primary DNS domain of the IPA deployment (not
necessarily related to the current hostname)
--server=SERVER FQDN of IPA server
--realm=REALM_NAME Kerberos realm name of the IPA deployment (typically
an upper-cased name of the primary DNS domain)
--hostname=HOST_NAME
The hostname of this machine (FQDN). If specified, the
hostname will be set and the system configuration will
be updated to persist over reboot. By default the
result of getfqdn() call from Python's socket module
is used.
Client options:
-w PASSWORD, --password=PASSWORD
password to join the IPA realm (assumes bulk password
unless principal is also set)
-W Prompt for a password to join the IPA realm
-f, --force force setting of LDAP/Kerberos conf
--configure-firefox
configure Firefox to use IPA domain credentials
--firefox-dir=FIREFOX_DIR
specify directory where Firefox is installed (for
example: '/usr/lib/firefox')
-k KEYTAB, --keytab=KEYTAB
path to backed up keytab from previous enrollment
--mkhomedir create home directories for users on their first login
--force-join Force client enrollment even if already enrolled
--ntp-server=NTP_SERVER
ntp server to use. This option can be used multiple
times
--ntp-pool=NTP_POOL
ntp server pool to use
-N, --no-ntp do not configure ntp
--nisdomain=NISDOMAIN
NIS domain name
--no-nisdomain do not configure NIS domain name
--ssh-trust-dns configure OpenSSH client to trust DNS SSHFP records
--no-ssh do not configure OpenSSH client
--no-sshd do not configure OpenSSH server
--no-sudo do not configure SSSD as data source for sudo
--subid configure SSSD as data source for subid
--no-dns-sshfp do not automatically create DNS SSHFP records
--kinit-attempts=KINIT_ATTEMPTS
number of attempts to obtain host TGT (defaults to 5).
SSSD options:
--fixed-primary Configure sssd to use fixed server as primary IPA
server
--permit disable access rules by default, permit all access.
--enable-dns-updates
Configures the machine to attempt dns updates when the
ip address changes.
--no-krb5-offline-passwords
Configure SSSD not to store user password when the
server is offline
--preserve-sssd Preserve old SSSD configuration if possible
PKINIT options:
--pkinit-identity=IDENTITY
PKINIT identity information (for example
FILE:/path/to/cert.pem,/path/to/key.pem)
--pkinit-anchor=FILEDIR
PKINIT trust anchors, prefixed with FILE: for CA PEM
bundle file or DIR: for an OpenSSL hash dir. The
option can be used used multiple times.
Automount options:
--automount-location=AUTOMOUNT_LOCATION
Automount location
Logging and output options:
-v, --verbose print debugging information
-d, --debug alias for --verbose (deprecated)
-q, --quiet output only errors
--log-file=FILE log to the given file
Or
man ipa-client-installHence, you can simply execute the command below to setup the client
sudo ipa-client-install --mkhomedir --no-ntpThe option, –mkhomedir, is important to ensure user’s home directory is created on first login to the machine.
Also, note that we disabled NTP services since we are not using FreeIPA server as our time server.
When ran, the DNS discovery may fail if you didnt integrate FreeIPA server with DNS, so you need to provide your domain name, e.g kifarunix.com and FreeIPA FQDN such as freeipa.kifarunix.com. Ensure you say yes for continuing with no DNS discovery.
Similarly, when prompted on who is authorized to enroll computers, use IPA admin and its credentials.
This program will set up IPA client.
Version 4.11.1
DNS discovery failed to determine your DNS domain
Provide the domain name of your IPA server (ex: example.com): kifarunix.com
Provide your IPA server name (ex: ipa.example.com): freeipa.kifarunix.com
The failure to use DNS to find your IPA server indicates that your resolv.conf file is not properly configured.
Autodiscovery of servers for failover cannot work with this configuration.
If you proceed with the installation, services will be configured to always access the discovered server for all operations and will not fail over to other servers in case of failure.
Proceed with fixed values and no DNS discovery? [no]: yes
Client hostname: noble.kifarunix.com
Realm: KIFARUNIX.COM
DNS Domain: kifarunix.com
IPA Server: freeipa.kifarunix.com
BaseDN: dc=kifarunix,dc=com
Continue to configure the system with these values? [no]: yes
Skipping chrony configuration
User authorized to enroll computers: admin
Password for [email protected]:
Successfully retrieved CA cert
Subject: CN=Certificate Authority,O=KIFARUNIX.COM
Issuer: CN=Certificate Authority,O=KIFARUNIX.COM
Valid From: 2024-05-04 03:38:52+00:00
Valid Until: 2044-05-04 03:38:52+00:00
Enrolled in IPA realm KIFARUNIX.COM
Created /etc/ipa/default.conf
Configured /etc/sssd/sssd.conf
Systemwide CA database updated.
Adding SSH public key from /etc/ssh/ssh_host_ed25519_key.pub
Adding SSH public key from /etc/ssh/ssh_host_ecdsa_key.pub
Adding SSH public key from /etc/ssh/ssh_host_rsa_key.pub
Could not update DNS SSHFP records.
SSSD enabled
Configured /etc/openldap/ldap.conf
Configured /etc/ssh/ssh_config
Configured /etc/ssh/sshd_config.d/04-ipa.conf
Configuring kifarunix.com as NIS domain.
Configured /etc/krb5.conf for IPA realm KIFARUNIX.COM
Client configuration complete.
The ipa-client-install command was successful
If you do not want to type the domain name/IPA server name, specify them on CLI;
sudo ipa-client-install --mkhomedir --no-ntp --domain=kifarunix.com --server=freeipa.kifarunix.comIf there is any error, a log file where it is written to is provided.
The command configures and enable SSSD service.
systemctl status sssd● sssd.service - System Security Services Daemon
Loaded: loaded (/usr/lib/systemd/system/sssd.service; enabled; preset: enabled)
Active: active (running) since Sat 2024-05-04 12:48:19 EAT; 7min ago
Main PID: 8327 (sssd)
Tasks: 7 (limit: 4615)
Memory: 57.6M (peak: 58.0M)
CPU: 249ms
CGroup: /system.slice/sssd.service
├─8327 /usr/sbin/sssd -i --logger=files
├─8328 /usr/libexec/sssd/sssd_be --domain kifarunix.com --uid 0 --gid 0 --logger=files
├─8329 /usr/libexec/sssd/sssd_nss --uid 0 --gid 0 --logger=files
├─8330 /usr/libexec/sssd/sssd_pam --uid 0 --gid 0 --logger=files
├─8331 /usr/libexec/sssd/sssd_ssh --uid 0 --gid 0 --logger=files
├─8332 /usr/libexec/sssd/sssd_sudo --uid 0 --gid 0 --logger=files
└─8333 /usr/libexec/sssd/sssd_pac --uid 0 --gid 0 --logger=files
May 04 12:48:19 noble systemd[1]: Starting sssd.service - System Security Services Daemon...
May 04 12:48:19 noble sssd[8327]: Starting up
May 04 12:48:19 noble sssd_be[8328]: Starting up
May 04 12:48:19 noble sssd_nss[8329]: Starting up
May 04 12:48:19 noble sssd_ssh[8331]: Starting up
May 04 12:48:19 noble sssd_pam[8330]: Starting up
May 04 12:48:19 noble sssd_sudo[8332]: Starting up
May 04 12:48:19 noble sssd_pac[8333]: Starting up
May 04 12:48:19 noble systemd[1]: Started sssd.service - System Security Services Daemon.
You can also check what configurations are installed on the SSSD configuration.
sudo cat /etc/sssd/sssd.conf[domain/kifarunix.com]
id_provider = ipa
ipa_server = _srv_, freeipa.kifarunix.com
ipa_domain = kifarunix.com
ipa_hostname = noble.kifarunix.com
auth_provider = ipa
chpass_provider = ipa
access_provider = ipa
cache_credentials = True
ldap_tls_cacert = /etc/ipa/ca.crt
krb5_store_password_if_offline = True
[sssd]
services = nss, pam, ssh, sudo
domains = kifarunix.com
[nss]
homedir_substring = /home
[pam]
[sudo]
[autofs]
[ssh]
[pac]
[ifp]
[session_recording]
If you check users using id command, you should be able to see them listed.
id bcooperuid=1152000006(bcooper) gid=1152000006(bcooper) groups=1152000006(bcooper)Login to Ubuntu 24.04 using FreeIPA user Account
We have already created some accounts on our FreeIPA server;
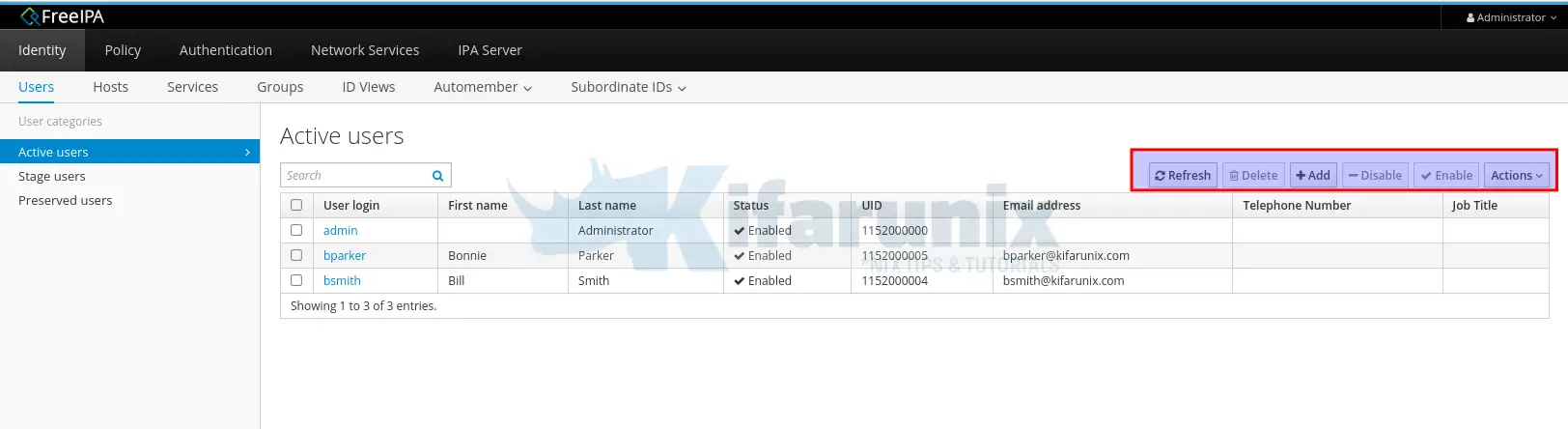
Or list them from command line
ipa user-find --all | grep "User login" User login: admin
User login: bcooper
User login: bparker
User login: bsmith
So, on our Ubuntu 24.04 client, let’s login as one of the users above;
On the login interface, select Not listed to be able to enter new username and password for login.

Enter the username and password. If the authentication is successful, you will be prompted to reset the password.

So, enter the current password and set a new one. When you login, you should see a message saying home directory is creating.
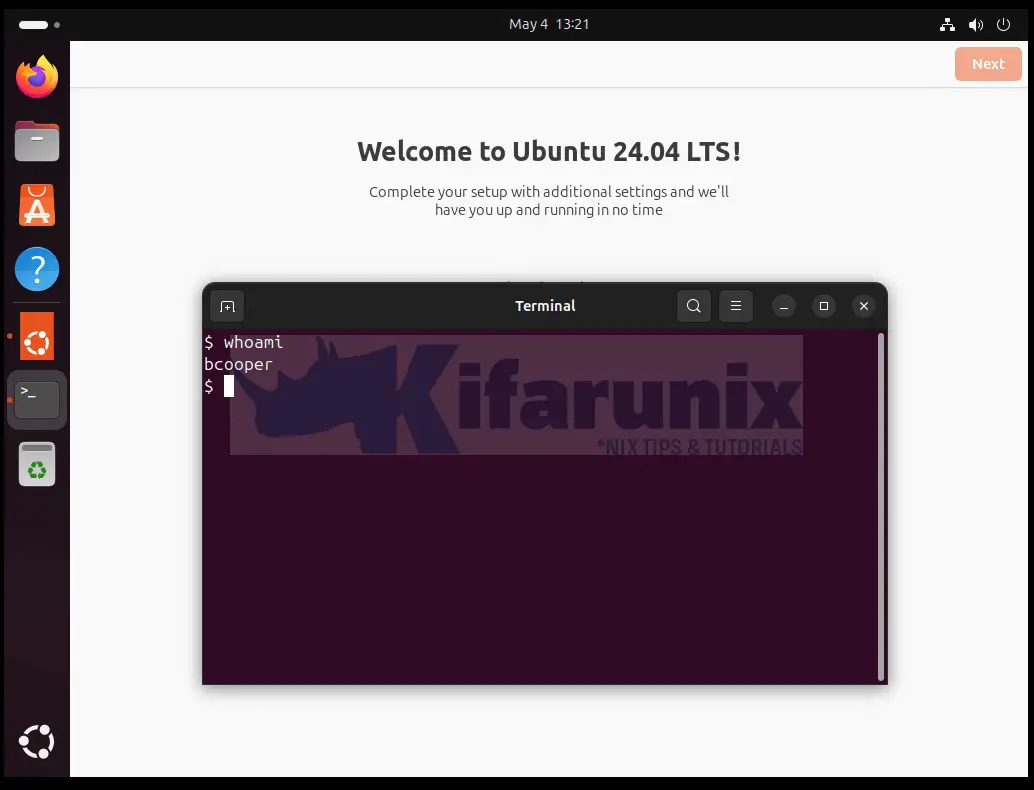
You can also try to ssh into the client using the FreeIPA server user account.
kifarunix@u24:~$ ssh [email protected]
The authenticity of host 'localhost ()' can't be established.
ED25519 key fingerprint is SHA256:VXA9MTsTF/73wJyT6qs9VeS/JVKKYJ2zUq9EqPzT4Tw.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'localhost' (ED25519) to the list of known hosts.
(bcooper@localhost) Password:
Welcome to Ubuntu 24.04 LTS (GNU/Linux 6.8.0-31-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
Expanded Security Maintenance for Applications is not enabled.
3 updates can be applied immediately.
3 of these updates are standard security updates.
To see these additional updates run: apt list --upgradable
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
$
And there you go. You have setup FreeIPA client on Ubuntu 24.04 and you should be able to login using the centrally managed user accounts. Stay connected for more tutorials around FreeIPA server.

