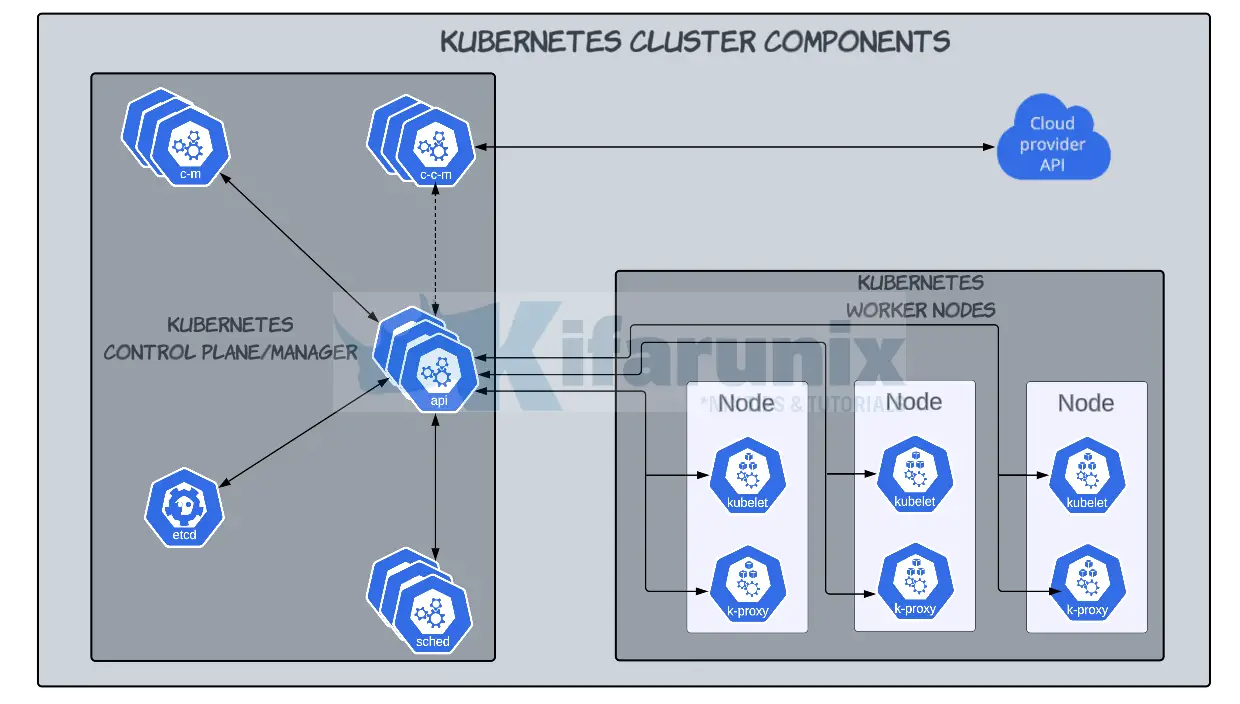
Kubernetes Architecture: A High-level Overview of Kubernetes Cluster Components
In this blog post, we will describe Kubernetes Architecture: a high-level overview of Kubernetes cluster components. Organizations are continually adopting cloud-native technologies with containerization becoming